关于加密,我应该了解什么?
最后更新: January 01, 2025
您可能对“加密”一词有所耳闻,但亦会对该词在不同语境下的使用而感到困惑。您或许曾见它出现在保护笔记本电脑、确保聊天应用安全以及防范在线购物风险等各种场景中。但无论是何场景,在提到加密时,指的都是同一概念:通过数学过程将信息转化为无法阅读的形式,只有拥有“解密密钥”的人方可解读。由此开始,事情会变得更复杂。
人们使用加密技术来发送(希望)只有预定收件人才能阅读的信息。如今,我们可以利用计算机来执行加密操作。数字加密技术已从简单的秘密信息传递扩展到更复杂的用途——不仅包括隐藏信息内容以防窥探,还包括验证信息作者的身份。
加密是我们所拥有的最佳信息保护技术,可用于防范恶意行为者、政府和服务提供商。如果运用得当,它几乎无法被破解。
在本指南中,我们将探讨加密技术的两种主要应用方式:用于处理静态数据和传输中数据。
静态数据加密
“静态数据”是指存储在某处(如移动设备、笔记本电脑、服务器或外接硬盘)的数据。静态数据不会在不同位置之间移动。
保护静态数据的一种加密形式是“全盘加密”(也称为“设备加密”)。启用全盘加密后,设备上存储的所有信息均被加密,并通过密码短语或其他认证方式进行保护。在移动设备或笔记本电脑上,这通常表现为设备锁屏,需要输入密码、密码短语或指纹才能解锁。但需注意,锁定设备(即需要密码“解锁”)并不一定意味着启用了全盘加密。
|
|
|
智能手机和笔记本电脑都有密码保护的“锁屏”界面。 |
请务必确认您的操作系统采用何种方式启用和管理全盘加密。虽然某些操作系统默认启用全盘加密,但有些系统并非如此。这意味着,他人可能会绕过设备锁并直接访问硬盘驱动器以获取设备数据;由于设备本身未加密,他们无需破解加密密钥即可实现此目的。有些系统即使在启用全盘加密时,仍会将未加密的明文存储在内存 (RAM) 中。内存属于临时存储器,因此设备关机后通常无法读取内存内容,但技术高超的攻击者可能会尝试冷启动攻击,理论上可检索内存内容。
全盘加密可以保护您的设备,防止他人对设备进行物理访问。此功能可以防止您的室友、同事或雇主、学校官员、家人、伴侣、警察或其他执法人员查看您的数据。如果设备被盗或丢失(例如您不小心把笔记本电脑落在公交车上或咖啡厅里),全盘加密也能保护设备上的数据。
静态数据加密还有其他方式。例如,“文件加密”仅加密计算机或其他存储设备中的单个文件;“驱动器加密”(也称“磁盘加密”)则可加密设备特定存储区域内的所有数据。
您可结合使用上述不同类型的静态加密方式。例如,若需保护医疗文档中的敏感信息,可先用文件加密单独加密设备上的医疗文件,再用驱动器加密来加密存储这些文件的设备区域,最后启用全盘加密。此时,所有医疗信息以及驱动器上的其他所有文件(甚至是计算机操作系统文件)均已被加密。因此,即使他人知晓计算机登录密码,也需额外获取加密医疗文件的密码才能访问内容。
请查阅我们关于在计算机、iPhone 或安卓设备上启用全盘加密的指南。
传输中数据加密
|
|
|
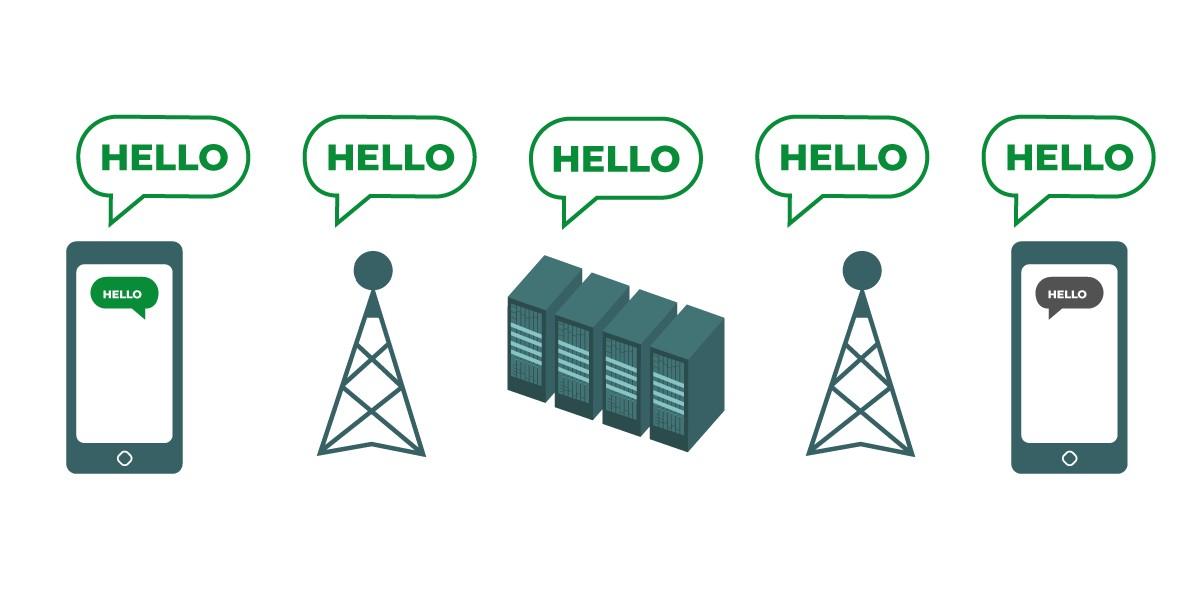
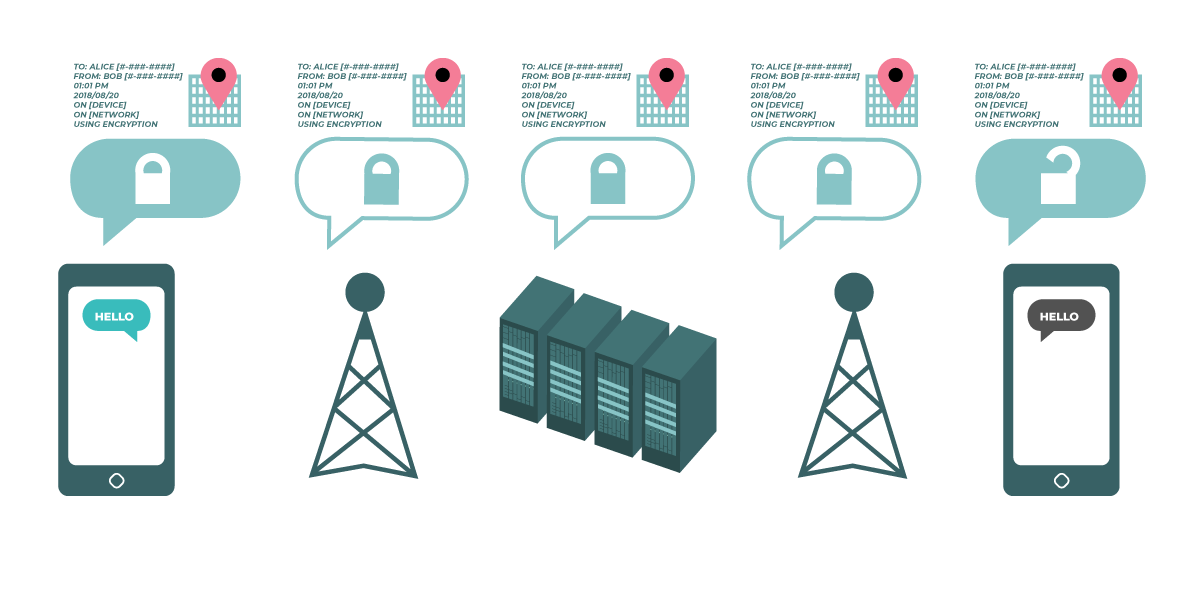
示意图展示了传输中的未加密数据。左侧的智能手机向最右侧的智能手机发送了一条绿色的未加密消息“Hello”。传输过程中,信号塔将消息传递至公司服务器,随后转送至另一座信号塔——这些中转节点以及所有传递未加密消息的计算机和网络都能看到未加密的“Hello”消息。最终,接收方手机收到未加密的“Hello”消息。 |
“传输中数据”是指通过网络在不同位置间传输的信息。例如,当您通过即时通讯应用发送消息时,该消息会从您的设备转移至应用公司的服务器,再送达收件人的设备。网页浏览亦是如此:当您访问网站时,该网页的数据会从网站服务器传输至您的浏览器。
某些热门应用提供了看似能保护消息的功能(如“阅后即焚”)。但根据您的安全需求,此类功能可能无法提供足够的保护。因为通信(如聊天或消息)看似安全,实则不然。传输消息的计算机可能窥探消息内容。
传输中数据加密有两种方式:传输层加密与端到端加密。服务提供商支持的加密类型是选择合适服务的重要考量因素。需明确对话是采用传输层加密还是端到端加密。
传输层加密
|
|
|
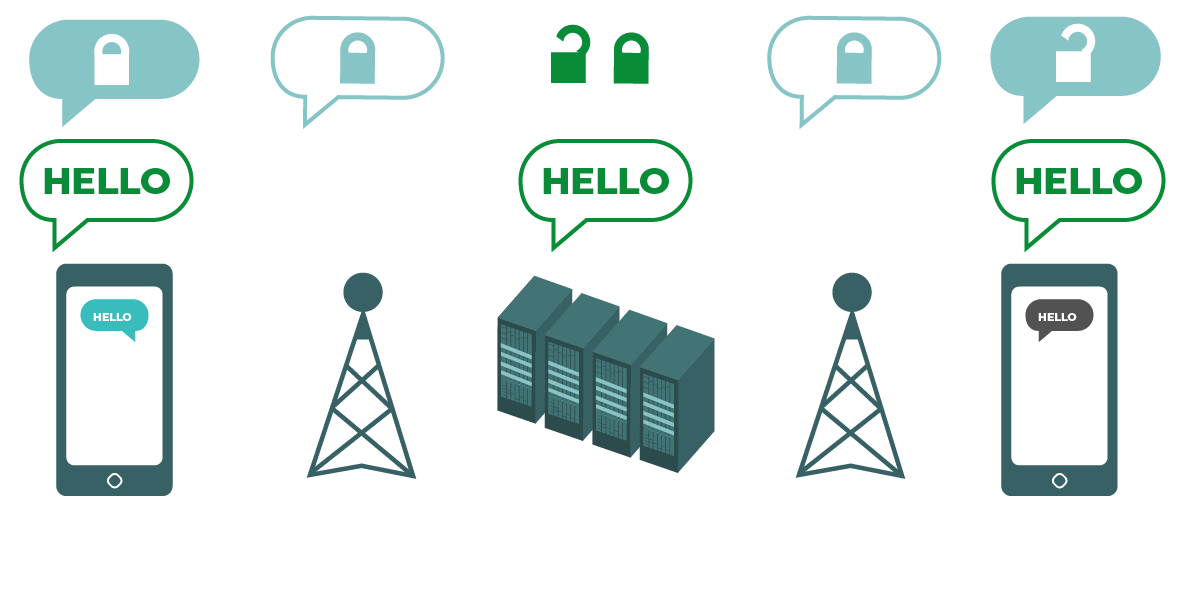
示意图展示了传输层加密。左侧的智能手机发送了一条绿色、未加密的消息:“Hello”。该消息经加密后传递至信号塔。中间的公司服务器可解密消息并将其重新加密后转至下一信号塔。最后,接收方手机收到加密消息后将其解密为“Hello”。 |
传输层加密(最常通过称为“传输层安全协议 (TLS)”的技术实现)在消息从设备传输至应用服务器,再从服务器传输至接收方设备的过程中提供保护。在此过程中,消息服务提供商(或您访问的网站、使用的应用)可查看消息的未加密副本。由于消息可能被公司服务器查看(且通常会被存储),当面临执法部门的数据调取请求或公司服务器遭到入侵时,这些消息存在泄露风险。
传输层加密示例:HTTPS

在浏览器地址栏中,您可能会看到锁形图标,或者您也可以点击菜单图标展开下拉菜单,并找到带有类似“连接安全”信息的锁形标识。这表示网站使用了 HTTPS ,这是一种常见的传输层加密技术,比未加密的 HTTP 更安全。
为什么呢?
HTTPS 网站的服务器可以查看您在其网站上输入的数据(如消息、搜索内容、信用卡号及登录凭证),但这些信息对网络窃听者不可读。
当有人监控网络并试图查看用户访问的网站时,HTTP 连接毫无防护。而 HTTPS 连接能隐藏您访问网站的具体页面路径,即“斜杠之后”的所有内容。例如,当您通过 HTTPS 访问 https://ssd.eff.org/en/module/what-encryption 时,窃听者只能看到 https://ssd.eff.org。
若浏览器地址栏未显示 HTTPS 或 HTTP,这是因为 HTTPS 已普及,许多浏览器默认不再显示完整网址。
但需注意,使用 HTTPS 并不意味着服务能够全面保护用户访问网站的隐私。例如,HTTPS 保护的网站仍可能使用跟踪 Cookie 或托管恶意软件。
传输层加密示例:VPN
虚拟专用网络 (VPN) 是传输层加密的另一范例。未使用 VPN 时,您的流量通过互联网服务提供商 (ISP) 连接进行传输;使用 VPN 后,流量仍经由 ISP 连接,但在您与 VPN 提供商之间实现了加密。若有人在本地网络监控您访问的网站,他们仅能发现您连接了 VPN 及其提供商的身份,但无法获知具体访问的网站。
尽管 VPN 能向 ISP 隐藏您的流量,但所有流量都会暴露给 VPN 提供商。VPN 提供商将能查看、存储并修改您的流量。使用 VPN 本质上是将信任从 ISP 转移至 VPN,因此必须确保您确信所选的 VPN 提供商能保护数据安全。
关于选择适合 VPN 的更多建议,请阅读我们的 VPN 指南。
端到端加密
|
|
|
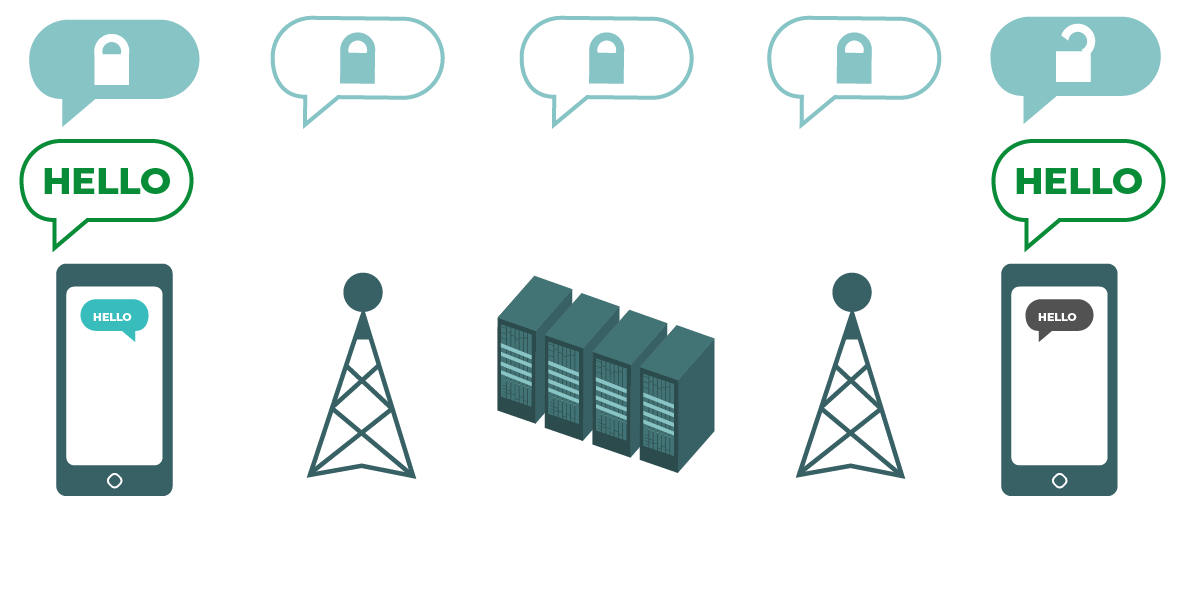
示意图展示了端到端加密流程。左侧的智能手机发送了一条绿色、未加密的消息:“Hello”。该消息经加密后传递至信号塔和公司服务器。最后,接收方手机收到加密消息后将其解密为“Hello”。与传输层加密不同,ISP 服务器无法解密该消息,唯有端点(发送和接收加密消息的原始设备)才能进行解密。 |
端到端加密全程保护传输中的消息,确保信息由原始发送方(第一“端”)转化为密文,并仅由最终接收方(第二“端”)解码。包括应用服务器在内的任何其他人都无法“监听”或窃取您的活动信息。
在设备的应用内访问端到端加密消息,这意味着该应用公司本身无法读取内容。然而,使用端到端加密的应用开发人员虽无法查看消息内容,仍可能收集某些元数据(如消息发送时间或您的 IP 地址)。
我们在《与他人通信指南》中提供了有关端到端加密工具的使用说明,并在《端到端加密深度解析指南》中详述了技术细节。另外还提供了关于 Signal 和 WhatsApp(两款采用端到端加密的热门聊天应用)的使用指南。
传输层加密还是端到端加密?
在决定选择哪种加密方式时,需回答以下关键问题:您是否信任正在使用的应用或服务?您是否信任其技术基础设施?其应对执法请求的政策是否可靠?
若任一答案为“否”,则应选择端到端加密。若答案均为“是”,则传输层加密可能已经足够,但仍建议尽可能选择支持端到端加密的服务。
传输中加密的局限性
加密并非万全之策。即使发送加密消息,接收方仍会将其解密。若通信端点(您使用的设备)被入侵,加密通信可能遭泄露。此外,接收方也可截屏或记录通信日志。
若自动将加密对话备份至云端,请确保备份也已加密。这能保证通信不仅在传输中加密,静态存储时亦有加密。
传输中加密可保护通信内容,但不会加密元数据。例如,加密可将您与朋友的对话转为乱码,但无法隐藏:
- 您与朋友通信的事实。
- 您使用加密通信的事实。
- 其他通信相关信息(如位置、时间、通信时长)。
对监控高度敏感者(如担心网络被主动监听)在敏感时段或特定活动中使用加密,这本身就可能会带来风险。为什么呢?若偶尔使用加密,元数据可能与重要日期/时间关联,并暴露您对特定通信的敏感性。因此,建议尽可能频繁使用加密,甚至包括日常活动。
若您是网络中唯一使用加密的人,此元数据可能被视为可疑数据。因此,许多加密倡导者鼓励所有人都尽可能使用加密工具:让加密工具的使用常态化,从而为真正需要加密的人提供掩护。
综合运用

同时加密传输中数据与静态数据能提供比单一加密更全面的安全性。通过多重防御手段,您可实现更深层次的保护——信息安全专家称之为“深度防御”。
例如:若从加密移动设备(静态加密)发送未加密消息(未加密传输中数据),这些消息仍可能遭政府、服务提供商或技术攻击者的网络窃听和拦截。但移动设备上的消息记录因静态加密,可防范物理接触者访问(在其无密码的情况下)。
相反,若从未加密设备(未静态加密)发送端到端加密消息(加密传输中数据),这些消息在网络传输中可防窃听,但设备若被物理接触,消息仍可能遭读取。
综上,同时加密网络传输中数据与设备静态数据是抵御更广泛风险的理想方案。
如需深入了解加密技术,请继续阅读我们的指南《加密的核心概念》。