ما هو التشفير؟
آخر تحديث: January 01, 2025
ربما سمعت كلمة "تشفير " مستخدمة، ولكن في العديد من السياقات المختلفة حتى أصبحت مربكة. ربما رأيتها تشير إلى كل شيء بدءًا من حماية الكمبيوتر المحمول، أو أمان تطبيق الدردشة، أو حماية التسوق عبر الإنترنت. بغض النظر عن وقت استخدامها، عندما نتحدث عن التشفير، فإننا نشير إلى نفس الشيء: العملية الرياضية لجعل الرسالة غير قابلة للقراءة إلا من قبل شخص لديه/ا "المفتاح" لفك تشفيرها. ومن هنا، يصبح الأمر أكثر تعقيدًا.
لقد استخدم الناس التشفير لإرسال رسائل إلى بعضهم/ن البعض والتي (نأمل) ألا يتمكن أي شخص من قراءتها باستثناء المتلقي المقصود. اليوم، لدينا أجهزة كمبيوتر قادرة على إجراء التشفير لنا. لقد توسعت تقنية التشفير الرقمي إلى ما هو أبعد من الرسائل السرية البسيطة، وهذه الأيام يمكنك استخدام التشفير لأغراض أكثر تفصيلاً، مثل ليس فقط إخفاء محتوى الرسائل عن أعين المتطفلين/ات، ولكن أيضًا التحقق من كاتب/ة تلك الرسائل.
التشفير هو أفضل تقنية لدينا لحماية المعلومات من الجهات السيئة والحكومات ومقدمي/ات الخدمات. عند استخدامه بشكل صحيح، يكاد يكون من المستحيل كسره.
في هذا الدليل، سننظر في طريقتين رئيسيتين يتم تطبيق التشفير بهما: لتشفير البيانات في وضع السكون والبيانات أثناء النقل.
تشفير البيانات في وضع السكون
البيانات "في وضع السكون" هي البيانات المخزنة في مكان ما، مثل جهاز محمول أو كمبيوتر محمول أو خادم أو محرك أقراص ثابت خارجي. عندما تكون البيانات في وضع السكون، فهي لا تنتقل من مكان إلى آخر.
أحد الأمثلة على شكل التشفير الذي يحمي البيانات في وضع السكون هو تشفير "القرص الكامل" (يُطلق عليه أحيانًا "تشفير الجهاز"). يؤدي تمكين تشفير القرص بالكامل إلى تشفير جميع المعلومات المخزنة على الجهاز وحمايتها بعبارة مرور أو طريقة مصادقة أخرى. على جهاز محمول أو كمبيوتر محمول، يبدو هذا عادةً مثل شاشة قفل الجهاز، والتي تتطلب رمز مرور أو عبارة مرور أو بصمة إبهام. ومع ذلك، فإن قفل جهازك (أي طلب كلمة مرور "لإلغاء قفل" جهازك) لا يعني دائمًا تمكين تشفير القرص بالكامل.
|
|
|
هاتف ذكي وجهاز كمبيوتر محمول يتمتع كل منهما بشاشة "قفل" محمية بكلمة مرور. |
تأكد/ي من التحقق من كيفية تمكين نظام التشغيل الخاص بك وإدارة تشفير القرص الكامل. في حين أن بعض أنظمة التشغيل لديها تشفير القرص الكامل ممكّن افتراضيًا، فإن بعض أنظمة التشغيل لا تفعل ذلك. وهذا يعني أنه يمكن لأي شخص الوصول إلى البيانات الموجودة على جهازك عن طريق تجاوز قفل الجهاز والوصول إلى القرص الصلب مباشرة، دون الحاجة إلى كسر مفتاح التشفير لأن الجهاز نفسه غير مشفر. تخزن بعض الأنظمة نصًا عاديًا غير مشفر في ذاكرة الوصول العشوائي، حتى عندما تستخدم تشفير القرص الكامل. ذاكرة الوصول العشوائي هي تخزين مؤقت، مما يعني أنه بعد إيقاف تشغيل جهازك، لا يمكن قراءة الذاكرة عادةً، ولكن يمكن لخصم متطور محاولة شن هجوم تمهيد بارد واسترجاع محتويات ذاكرة الوصول العشوائي.
يمكن أن يحمي تشفير القرص الكامل أجهزتك من الأشخاص الذين/ اللواتي لديهم/ن وصول فعلي إليها. هذا مفيد إذا كنت تريد/ين حماية بياناتك من زملائك/ زميلاتك في السكن أو زملاء/ زميلات العمل أو أصحاب/ صاحبات العمل أو مسؤولي/ات المدرسة أو أفراد الأسرة أو الشركاء/ الشريكات أو ضباط/ ضابطات الشرطة أو غيرهم/ن من مسؤولي/ات إنفاذ القانون. كما أنه يحمي البيانات الموجودة على أجهزتك في حالة سرقتها أو فقدها، مثل إذا تركت هاتفك عن طريق الخطأ في حافلة أو في مطعم.
هناك طرق أخرى لتشفير البيانات في وضع السكون. أحد الخيارات، المعروف باسم "تشفير الملفات"، يشفر فقط الملفات الفردية على جهاز كمبيوتر أو جهاز تخزين آخر. خيار آخر هو "تشفير محرك الأقراص" (المعروف أيضًا باسم "تشفير القرص") الذي يشفر جميع البيانات الموجودة على منطقة تخزين محددة على جهاز.
يمكنك استخدام هذه الأنواع المختلفة من التشفير في وضع السكون معًا. على سبيل المثال، لنفترض أنك تريد/ين حماية المعلومات الحساسة في مستنداتك الطبية. يمكنك استخدام تشفير الملفات لتشفير ملف طبي فردي مخزن على جهازك. يمكنك بعد ذلك استخدام تشفير محرك الأقراص لتشفير جزء جهازك الذي يتم تخزين هذه المعلومات الطبية عليه. أخيرًا، إذا قمت/ي بتمكين تشفير القرص الكامل على جهازك، فسيتم تشفير كل شيء - جميع المعلومات الطبية بالإضافة إلى كل ملف آخر على محرك الأقراص، بما في ذلك ملفات نظام تشغيل الكمبيوتر. لذا، حتى إذا اكتشف شخص ما كلمة مرور تسجيل الدخول لجهاز الكمبيوتر الخاص بك، فسيظل بحاجة إلى معرفة كلمة المرور التي استخدمتها لتشفير الملف بمعلوماتك الطبية قبل أن يتمكن من الوصول إليه.
اطلع/ي على أدلة تمكين تشفير القرص بالكامل على جهاز الكمبيوتر الخاص بك، أو جهاز آيفون أو أندرويد.
تشفير البيانات أثناء النقل
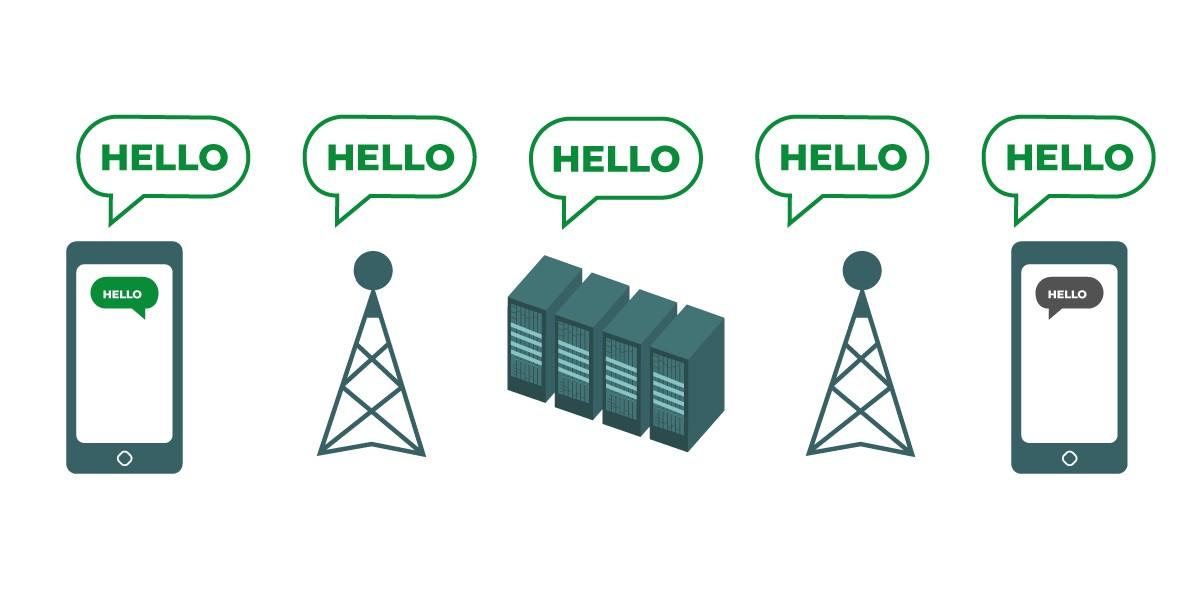
|
|
يوضح الرسم البياني بيانات غير مشفرة أثناء نقلها. على اليسار، يرسل هاتف ذكي رسالة خضراء غير مشفرة إلى هاتف ذكي آخر في أقصى اليمين. وعلى طول الطريق، يمرر برج الهاتف المحمول الرسالة إلى خوادم الشركة ثم إلى برج هاتف محمول آخر، حيث يمكن لكل منهما رؤية رسالة "Hello" غير المشفرة. تتمكن جميع أجهزة الكمبيوتر والشبكات التي تمرر الرسالة غير المشفرة من رؤية الرسالة. في النهاية، يتلقى الهاتف الذكي الآخر رسالة "Hello" غير المشفرة. |
البيانات "أثناء التنقل" هي المعلومات التي تنتقل عبر شبكة من مكان إلى آخر. على سبيل المثال، عندما ترسل/ين رسالة على تطبيق مراسلة، تنتقل الرسالة من جهازك إلى خوادم شركة التطبيق، ثم إلى جهاز المتلقي. مثال آخر هو تصفح الانترنت: عندما تذهب إلى موقع إلكتروني، تنتقل البيانات من الصفحة الإلكترونية هذه من خوادم الموقع الإلكتروني إلى متصفحك.
تقدم بعض التطبيقات الشائعة ميزات تبدو وكأنها تحمي الرسائل، مثل الرسائل التي تختفي. ومع ذلك، اعتمادًا على خطة الأمان الخاصة بك، قد لا توفر الرسائل التي تختفي خصائص الأمان التي تحتاجها. فقط لأن الاتصال (مثل الدردشة أو الرسالة) يمكن أن يشعر بالأمان، لا يعني أنه آمن. قد تتمكن أجهزة الكمبيوتر التي تمر عبر رسالتك من الاطلاع على محتويات رسالتك.
هناك طريقتان لتشفير البيانات أثناء النقل: تشفير طبقة النقل والتشفير من البداية إلى النهاية. يمكن أن يكون نوع التشفير الذي يدعمه مزود الخدمة عاملاً مهمًا في تحديد الخدمات المناسبة لك. من المهم معرفة ما إذا كانت المحادثات مشفرة عبر تشفير طبقة النقل أو التشفير من البداية إلى النهاية.
تشفير طبقة النقل
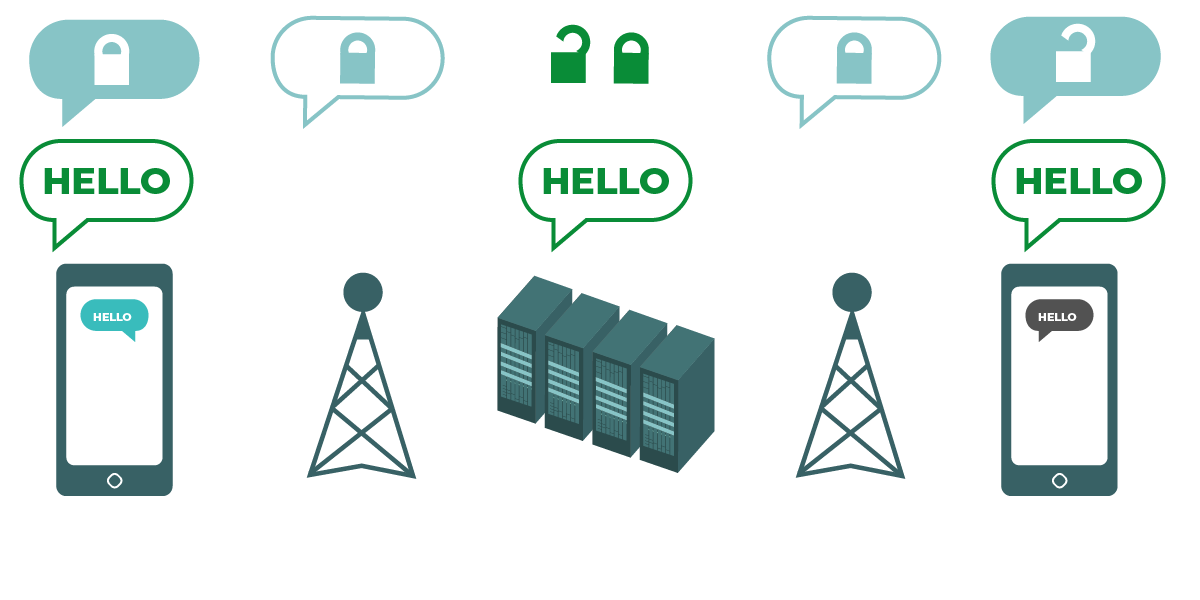
|
|
يوضح الرسم البياني تشفير طبقة النقل. على اليسار، يرسل هاتف ذكي رسالة خضراء غير مشفرة: "Hello". يتم تشفير هذه الرسالة، ثم يتم تمريرها إلى برج الهاتف المحمول. في المنتصف، تتمكن خوادم الشركة من فك تشفير الرسالة وإعادة تشفيرها وإرسالها إلى برج الهاتف المحمول التالي. في النهاية، يتلقى الهاتف الذكي الآخر الرسالة المشفرة، ويفك تشفيرها لتقرأ "Hello". |
إن تشفير طبقة النقل، والذي يتم تنفيذه عادةً باستخدام البروتوكول المعروف باسم أمان طبقة النقل (TLS)، يحمي الرسائل أثناء انتقالها من جهازك إلى خوادم التطبيق، ثم من خوادم التطبيق إلى جهاز المتلقي/ة. وفي المنتصف، يمكن لمزود/ة خدمة الرسائل الخاص بك - أو الموقع الإلكتروني الذي تتصفحه/يه، أو التطبيق الذي تستخدمه/يه - رؤية نسخ غير مشفرة من رسائلك. ولأن رسائلك يمكن رؤيتها (وغالبًا ما يتم تخزينها على) خوادم الشركة، فقد تكون عرضة لطلبات إنفاذ القانون أو التسريب إذا تم اختراق خوادم الشركة.
مثال على تشفير طبقة النقل: HTTPS

إذا قمت/ي بفحص شريط عنوان URL في متصفحك، فقد ترى/ين رمز قفل، أو رمز قائمة يمكنك النقر فوقه للحصول على قائمة منسدلة تعرض قفلًا مع رسالة مثل "اتصال آمن". وهذا يعني أن الموقع يستخدم HTTPS ، وهو مثال على تشفير طبقة النقل الذي نصادفه كثيرًا على الإنترنت. إنه يوفر أمانًا أكثر من HTTP غير المشفر.
لماذا؟
يمكن لخوادم موقع HTTPS رؤية البيانات التي تدخلها أثناء وجودك على موقعها (على سبيل المثال، الرسائل، والعمليات البحثية، وأرقام بطاقات الائتمان، وعمليات تسجيل الدخول)، ولكن هذه المعلومات غير قابلة للقراءة للمتنصتين/ات على الشبكة.
إذا كان شخص ما يتجسس على الشبكة ويحاول معرفة المواقع الإلكترونية التي يزورها المستخدمون/ات، فإن اتصال HTTP لا يوفر أي حماية. من ناحية أخرى، يخفي اتصال HTTPS الصفحة المحددة على الموقع الإلكتروني الذي تنتقل إليه - أي كل شيء "بعد الخط المائل". على سبيل المثال، إذا كنت تستخدم HTTPS للاتصال بـ "https://ssd.eff.org/en/module/what-encryption"، فلن يتمكن المتنصت من رؤية سوى https://ssd.eff.org.
إذا كنت تنظر/ين إلى عنوان URL الخاص بالمتصفح الخاص بك وتتساءل/ين عن سبب عدم رؤيتك لـ HTTPS أو HTTP، فذلك لأن HTTPS شائع جدًا هذه الأيام، حتى أن العديد من المتصفحات لا تعرض عنوان URL الكامل افتراضيًا بعد الآن.
مجرد استخدام الخدمة لـ HTTPS لا يعني أن الخدمة تحمي خصوصية مستخدميها/اتها الذين/ اللواتي يزورون موقعها بالكامل. على سبيل المثال، قد يظل الموقع المحمي بـ HTTPS يستخدم ملفات تعريف الارتباط للتتبع أو يستضيف برامج ضارة.
مثال على تشفير طبقة النقل : VPN
تُعد الشبكة الخاصة الافتراضية (VPN) مثالاً آخر على تشفير طبقة النقل. بدون VPN ، تنتقل حركة المرور الخاصة بك عبر اتصال مزود خدمة الإنترنت (ISP). مع VPN، لا تزال حركة المرور الخاصة بك تنتقل عبر اتصال مزود خدمة الإنترنت الخاص بك، ولكنها مشفرة بينك وبين مزود VPN الخاص بك. إذا كان شخص ما يتجسس على شبكتك المحلية ويحاول معرفة المواقع التي تزورها، فسوف يتمكن من معرفة أنك متصل/ة بشبكة VPN ومن هو مزود VPN هذا، لكنه لن يرى المواقع التي تزورها.
في حين أن استخدام VPN يخفي حركة مرورك عن مزود خدمة الإنترنت الخاص بك، فإنه يعرض أيضًا كل حركة مرورك لمزود VPN نفسه. سيتمكن مزود VPN من رؤية حركة مرورك وتخزينها وتعديلها. يؤدي استخدام VPN بشكل أساسي إلى تحويل ثقتك من مزود خدمة الإنترنت الخاص بك إلى VPN، لذلك من المهم التأكد من أنك تثق/ين في مزود VPN الخاص بك لحماية بياناتك.
لمزيد من النصائح حول اختيار VPN المناسب لك، اقرأ/ي دليلنا حول شبكات VPN.
التشفير من البداية إلى النهاية
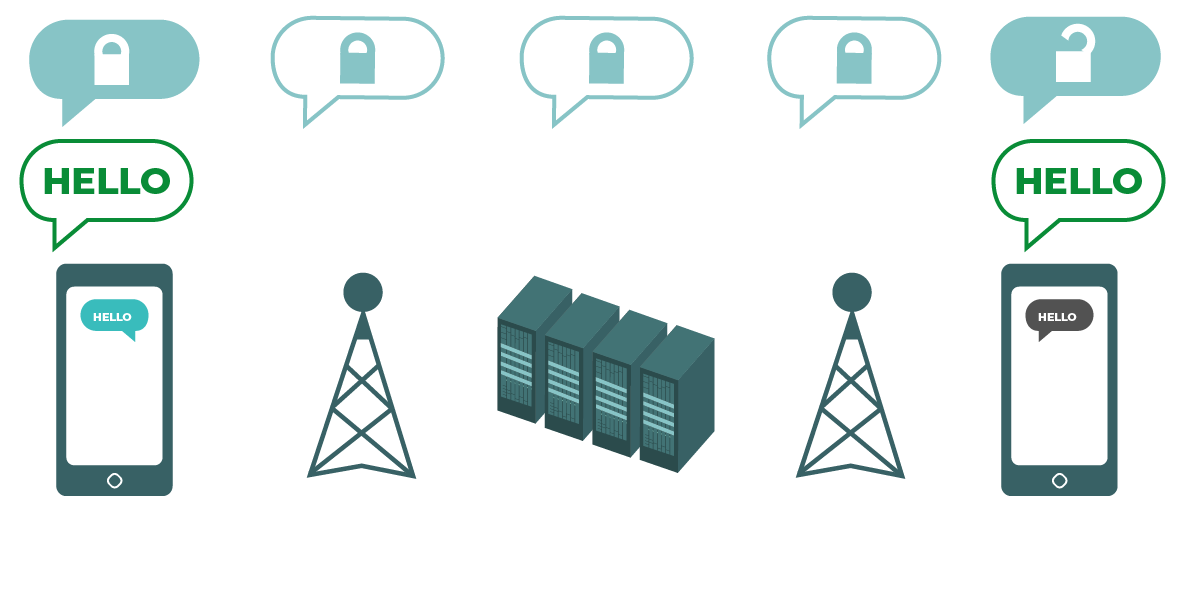
|
|
يوضح الرسم البياني التشفير من البداية إلى النهاية. على اليسار، يرسل هاتف ذكي رسالة خضراء غير مشفرة: "Hello". يتم تشفير هذه الرسالة، ثم يتم تمريرها إلى برج الهاتف المحمول وخوادم الشركة. في النهاية، يتلقى الهاتف الذكي الآخر الرسالة المشفرة، ويفك تشفيرها لتقرأ "Hello". على عكس تشفير طبقة النقل، لا تتمكن خوادم مزود خدمة الإنترنت الخاص بك من فك تشفير الرسالة. فقط نقاط النهاية (الأجهزة الأصلية التي ترسل وتستقبل الرسائل المشفرة) يمكنها فك تشفير الرسالة. |
تحمي تقنية التشفير من البداية إلى النهاية الرسائل أثناء نقلها من المرسل/ة إلى المستقبل/ة. وتضمن تحويل المعلومات إلى رسالة سرية من قبل المرسل/ة الأصلي/ة ("النهاية" الأولى) وفك تشفيرها فقط من قبل المتلقي/ة النهائي/ة ("النهاية" الثانية). ولا يمكن لأي شخص، بما في ذلك خوادم التطبيق الذي تستخدمه، "الاستماع" والتنصت على نشاطك.
إن الوصول إلى الرسائل المشفرة من البداية إلى النهاية في تطبيق على جهازك يعني أن شركة التطبيق نفسها لا تستطيع قراءتها. ومع ذلك، في حين لا يستطيع مطور التطبيق الذي يستخدم التشفير من البداية إلى النهاية رؤية محتويات الرسالة، فإنه لا يزال بإمكانه جمع أنواع معينة من البيانات الوصفية، مثل وقت إرسال الرسالة أو عنوان IP الخاص بك.
نقدم أدلة لاستخدام أدوات التشفير من البداية إلى النهاية في دليل التواصل مع الآخرين/ الأخريات والمزيد من التفاصيل حول التفاصيل في دليلنا المتعمق حول التشفير من البداية إلى النهاية. لدينا أيضًا أدلة لاستخدام اثنين من أكثر تطبيقات الدردشة شيوعًا التي تستخدم التشفير من البداية إلى النهاية، سيغنال وواتساب.
تشفير طبقة النقل أم التشفير من البداية إلى النهاية؟
الأسئلة المهمة التي يجب طرحها لتحديد ما إذا كنت بحاجة إلى تشفير طبقة النقل أو التشفير من البداية إلى النهاية هي: هل تثق/ين في التطبيق أو الخدمة التي تستخدمها؟ هل تثق/ين في البنية التحتية التقنية الخاصة بها؟ ماذا عن سياساتها للحماية من طلبات إنفاذ القانون؟
إذا أجبت بـ "لا" على أي من هذه الأسئلة، فأنت بحاجة إلى تشفير من البداية إلى النهاية. إذا أجبت بـ "نعم"، فقد تكون الخدمة التي تدعم تشفير طبقة النقل فقط كافية بالنسبة لك - ولكن من الأفضل استخدام الخدمات التي تدعم التشفير من البداية إلى النهاية عندما يكون ذلك ممكنًا.
ما لا يفعله التشفير أثناء النقل
التشفير ليس علاجًا لكل شيء. حتى إذا كنت ترسل رسائل مشفرة، فسيتم فك تشفير الرسالة بواسطة الشخص الذي تتواصل معه. إذا تعرضت نقاط النهاية الخاصة بك (الأجهزة التي تستخدمها للاتصال) للخطر، فقد تتعرض اتصالاتك المشفرة للخطر. بالإضافة إلى ذلك، يمكن للشخص الذي تتواصل/ين معه التقاط لقطات شاشة أو الاحتفاظ بسجلات (سجلات) لاتصالاتك.
إذا كنت تخزن/ين نسخًا احتياطية من المحادثات المشفرة تلقائيًا على السحابة، فتأكد/ي من تشفير النسخ الاحتياطية أيضًا. وهذا يضمن تشفير محادثاتك ليس فقط أثناء النقل ولكن أيضًا أثناء السكون.

إذا قمت/ي بتشفير البيانات أثناء النقل، فسوف يحمي ذلك محتوى اتصالاتك، لكنه لن يشفر البيانات الوصفية . على سبيل المثال، يمكنك استخدام التشفير لخلط الرسائل بينك وبين صديقك وتحويلها إلى هراء، لكنه لا يخفي:
● أنك وصديقك/تك تتواصلان.
● أنك تستخدم/ين التشفير للتواصل.
● أنواع أخرى من المعلومات حول اتصالاتك، مثل الموقع والأوقات وطول الاتصال.
يمكن للأشخاص الذين/ اللواتي لديهم/ن مخاوف متزايدة بشأن المراقبة (مثل أولئك الذين/ اللواتي يقلقون بشأن المراقبة النشطة لشبكاتهم/ن) تعريض أنفسهم/ن للخطر من خلال استخدام التشفير فقط خلال الأوقات الحساسة أو لأنشطة محددة. لماذا؟ إذا كنت تستخدم/ين التشفير أحيانًا فقط، فقد يربط بياناتك الوصفية بتواريخ وأوقات مهمة. كما يمكن أن يكشف أنك تعتبر هذه الاتصالات حساسة بشكل خاص. لذلك، استخدم/ي التشفير قدر الإمكان، حتى للأنشطة العادية.
إذا كنت الشخص الوحيد الذي يستخدم التشفير على الشبكة، فقد يُنظر إلى هذه البيانات الوصفية على أنها مشبوهة. لهذا السبب يشجع العديد من المتحمسين/ات للتشفير الجميع على استخدام أدوات التشفير كلما أمكنهم ذلك: لتطبيع استخدام التشفير للأشخاص الذين يحتاجون إليه حقًا.
جمع كل شيء معًا

إن تشفير البيانات أثناء النقل وفي حالة السكون معًا سيوفر لك أمانًا أكثر شمولاً من استخدام أحدهما فقط أو الآخر. من خلال استخدام طرق متعددة للدفاع عن بياناتك، يمكنك تحقيق مستوى أعمق من الحماية. هذا ما يسميه خبراء/ خبيرات أمن المعلومات "الدفاع المتعمق".
على سبيل المثال، إذا أرسلت رسائل غير مشفرة (لا تشفر بياناتك أثناء النقل) من جهاز محمول مشفر (تشفير بياناتك في حالة السكون)، فستظل هذه الرسائل عرضة للتنصت على الشبكة واعتراضها من قبل الحكومات أو مقدمي/ات الخدمات أو الخصوم ذوي/ات المهارات الفنية. ومع ذلك، سيتم حماية سجل الرسائل على جهازك المحمول من أي شخص لديه/ا وصول فعلي إلى جهازك المحمول إذا لم يكن لديه رمز المرور.
على العكس من ذلك، إذا أرسلت رسائل مشفرة من البداية إلى النهاية (تشفير بياناتك أثناء النقل) على جهاز غير مشفر (لا تشفر بياناتك في حالة السكون)، فستكون هذه الرسائل آمنة من التجسس والتنصت على الشبكة. ولكن سيتمكن شخص ما من الوصول إلى الرسائل وقراءتها إذا تمكن/ت من الوصول فعليًا إلى جهازك المحمول.
مع وضع هذه الأمثلة في الاعتبار، فإن تشفير بياناتك أثناء نقلها على الشبكة وأثناء تواجدها على جهازك يعد أمرًا مثاليًا لحماية نفسك من مجموعة أوسع من المخاطر المحتملة.
للحصول على نظرة أعمق حول كيفية استخدام التشفير، تابع/ي قراءة دليلنا المفاهيم الأساسية في التشفير.



