Temel Şifreleme Kavramları
Son güncelleme: January 01, 2025
Belli şartlarda şifreleme gayet otomatik ve basit ilerleyebilir. Fakat kimi durumlarda hata verebilir. Şifrelemeyi daha iyi anladıkça bu gibi durumlara karşı kendinizi daha iyi koruyabilirsiniz. Öncelikle, eğer okumadıysanız, Şifreleme Hakkında Bilmem Gerekenler adlı kılavuzumuzu okumanızı öneriyoruz.
Bu kılavuzda aktarım sırasında şifreleme konusunu anlayabilmek için beş önemli kavramı inceleyeceğiz.
- Şifreler ve anahtarlar
- Simetrik ve asimetrik şifreleme
- Özel ve açık anahtarlar
- Kişiler için kimlik doğrulama (açık anahtar parmak izleri)
- Web siteleri için kimlik doğrulama (güvenlik sertifikaları)
Şifreler ve anahtarlar
Kullanacağımız terimlerle başlayalım:
Şifreleme bir bilginin karıştırılarak, yalnızca özel bilgilerle açılmasını, yani “şifresinin çözülmesini” sağlayan matematiksel bir süreçtir. Bu süreç bir şifre ve anahtar içerir.
Şifre verileri şifreleyen ve şifreleri çözen bilgisayarın takip ettiği kurallar bütünüdür (algoritma). Verinin şifrelenmesi için uygulanan adım ve kuralların bire bir uygulanmasıyla şifre çözülür.
Şifreyi şifreleme ve şifre çözümü için yönlendiren bilgiye anahtar denir. Şifrelemeyi anlamak anahtarları anlamaktan geçer.
Tek Anahtar Mı, Çok Anahtar Mı?
Simetrik şifrelemede bilgilerin şifrelenmesi ve çözülmesi için tek bir anahtar kullanılır.
|
|
|
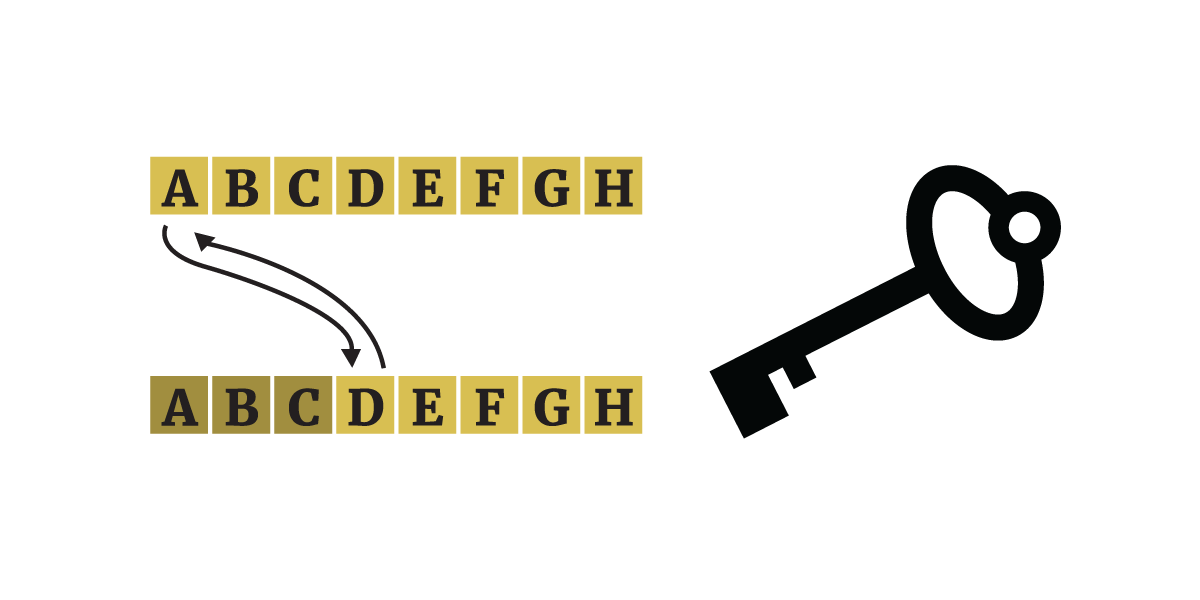
Eski şifreleme yöntemleri simetrikti. Jül Sezar’ın kullandığı “Sezar şifrelemesi” yönteminde mesajlar üç harf kaydırarak şifrelenir ve çözülür. Örneğin “A” harfi “D” harfine döner. Böylece, “ENCRYPTION IS COOL” ifadesi üçlü anahtar kullanıldığında “HQFUBSWLRQ LV FRRO” metnine dönüşür. Aynı anahtar kullanılarak özgün mesaj çözülebilir. |
Simetrik şifreleme bugün halen kullanılmaktadır. Genellikle şifrelemenin çözülmesini zorlaştıracak karmaşık matematiksel süreçlere dayanan “kesintisiz şifreleme” ve “blok şifreleme” yoluyla işler. Günümüzde şifreleme işlemleri, verileri karıştırarak özgün içeriği geçerli anahtar olmaksızın göstermeyi zorlaştıran pek çok adım izler. Gelişmiş Şifreleme Standardı (AES) gibi modern simetrik şifreleme algoritmaları güçlü ve hızlı çalışır.
Bilgisayarlarda dosya şifreleme, bölüm şifreleme ve tam disk şifreleme yoluyla cihazların ve bilgisayarların tamamında ve parola yöneticileri gibi şifreleme veri tabanlarında simetrik şifreleme kullanılır. Simetrik şifrelenen bilginin çözülmesi için sizden genellikle parola istenir. Bu sebeple güçlü parolalar kullanmanızı öneriyoruz.
Eğer anahtara erişmesi gereken tek kişi sizseniz, tek bir anahtar bulundurmak harika olur. Ancak tek anahtar kullanmanın dezavantajı vardır. Çok uzaktaki bir arkadaşınızla şifrelenmiş bir bilgi paylaşmak istediğinizde ne yapacaksınız? Arkadaşınızla bizzat buluşup anahtarı veremezseniz ne olacak? Anahtarınızı açık bir internet bağlantısı üzerinden arkadaşınızla güvenli biçimde nasıl paylaşabilirsiniz?
Açık anahtarlı şifreleme olarak da bilinen asimetrik şifreleme bu sorunları çözmeye yarar. Asimetrik şifreleme iki anahtar içerir: Özel anahtar (şifre çözümü için) ve açık anahtar (şifreleme için)

|
Simetrik Şifreleme:
|
Asimetrik Şifreleme:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Aktarım halindeki veriler genellikle simetrik ve asimetrik şifreleme birlikte kullanılarak şifrelenir.
Asimetrik Şifreleme: Özel ve Açık Anahtarlar
Özel ve açık anahtarlar matematiksel olarak birbirleriyle bağlı oldukları için eşleşir. Ortadan ikiye yarılmış bir kaya gibi düşünün. Bir araya getirilen iki yarı, bütünü oluşturur. Farklı bir kayanın yarısı ile bütün oluşturulamaz. Açık ve özel anahtar dosyaları hemen hemen aynıdır ve bilgisayarların okuyabileceği çok büyük sayılarla ifade edilir.
“Açık anahtar” adını alan bu öğe aslında gerçek hayatta bir şeyleri açmaya yarayan anahtar işlevi görmez. Veri kilidi gibi düşünmek daha doğru olacaktır. Açık ve özel anahtarlar hakkında daha fazla bilgi için ayrıntılarıyla açık anahtarlı şifreleme yazımıza göz atabilirsiniz.
|
|
|
Açık anahtar herkese verebileceğiniz, her yerde paylaşabileceğiniz bir dosyadır. Size uçtan uca şifrelenmiş mesaj göndermek isteyen kişi açık anahtarınıza ihtiyaç duyacaktır. Günümüzde uçtan uca şifrelemeyi destekleyen çoğu sohbet yazılımı bunu otomatik olarak yapar.
|
|
|
|
Özel anahtarınız ise şifrelenmiş bu mesajı çözmenize yarar. Şifrelenmiş mesajları okumanızı sağladığı için, özel anahtarınızı korumanız çok önemlidir. Özel anahtarınızla ayrıca belge imzalayabilirsiniz, böylelikle alıcılar belgelerin sizden geldiğini doğrulayabilir.
|
Özel anahtarınız cihazınızda korunması gereken bir dosya olduğu için, özel anahtarınızın bulunduğu cihazlarınızı parolayla ve şifreleyerek korumanızı öneririz. Güçlü parolalar ve cihaz şifrelemekılavuzlarımıza buradan erişebilirsiniz.
|
Açık Anahtar
|
Özel Anahtar
|
|
|
|
|
|
|
|
|
|
Aktarım halindeki bilgileri bir ölçüde kartpostal yollamaya benzetebiliriz. Aşağıda soldaki kartpostalda göndericinin metnine bakalım: “Selam! :-)” Gönderici, mesajın alıcısına hitaben yazmıştır bu ifadeyi. Mesaj şifrelenmediği için, alıcıya ulaşana kadar mesajı her kim eline geçirirse okuyabilir.

Sağda yine aynı kartpostalı görüyoruz, ancak mesaj gönderici ve alıcı arasında şifrelenmiş. Yine aynı “Selam! :-)” ifadesini taşıyan mesaj bize şifrelenmiş, anlamsız karakterler olarak gözüküyor.
Peki bu nasıl oluyor? Gönderici alıcının açık anahtarını buluyor. Mesajı alıcının açık anahtarına hitaben ilettiğinde anahtar mesajı şifreliyor. Gönderici aynı zamanda mesajın yalnızca kendisinden gelmiş olabileceğini göstermek için imzasını da mesaja ekliyor.
Mesajı kimin yollayıp kimin aldığı, gönderim ve iletim zamanı, nereden geçtiği gibi ek bilgiler olan üst veriler ise başkaları tarafından görülebilir durumdadır. Yani gönderici ve alıcının şifreleme kullandığını görebilir, iletişim kurduklarını anlayabiliriz, ancak mesajlarının içeriğini okuyamayız.
Mesajınızı Kime Şifreliyorsunuz? Gerçekten Söyledikleri Kişiler Mi?
Şöyle düşünebilirsiniz: “Açık anahtarımı kullanan kişinin bana şifrelenmiş bir mesaj gönderdiğini, özel anahtarımın ise şifrelenmiş mesajı okumamı sağladığını anladım. Peki ya biri beni taklit ederse? Yeni bir açık ve özel anahtar oluşturup beni taklit ederlerse?
Açık anahtarlı şifreleme tam da bu noktada özellikle işe yarayarak, hem sizin hem de alıcının kimliklerini doğrulama olanağı veriyor. Özel anahtarın neler yapabildiğine yakından bakalım.
Özel anahtarınız, açık anahtarınıza yollanan şifreli mesajları okumanızı sağlamanın yanı sıra, başkalarına yolladığınız mesajlara değiştirilemez dijital imza ekleme olanağı da tanır. Böylelikle “Evet, bu mesajı yazan gerçekten benim” demiş gibi olursunuz.
Alıcınız mesajınızla birlikte dijital imzanızı da görür ve açık anahtarınızdaki bilgiyle karşılaştırır.
Sürecin nasıl işlediğine bakalım.
Kişiler İçin Kimlik Doğrulama Açık Anahtar Parmak İzleri
Mesaj yolladığımız her an, iletişim kurduğumuz kişilerin iyi niyetine bağlı hareket ederiz. Örneğin, postacının bize gelen postaların içeriğini kurcaladığını düşünmeyiz. Arkadaşımızın bize yolladığı mektubu ele geçiren birinin mektubu açıp, değiştirip sonra sanki hiçbir şey olmamış gibi bize yollayacağını da düşünmeyiz. Ancak böyle bir risk yok değildir.
Şifrelenmiş mesajlarda da değiştirilme riski vardır. Ancak açık anahtarlı şifreleme, bize mesaj ileten kişinin gerçek hayattaki kimliğiyle dijital kimliğini kontrol ederek ulaşan bilginin değiştirilip değiştirilmediğini anlamamızı sağlar.
Açık anahtar, bir dosya içerisinde bulunan dev bir metin bloğudur. Aynı zamanda anahtar parmak izi adında, insanların okuyabileceği bir kısayoldan oluşur.

“Parmak izi ” bilgisayar güvenliği bağlamında pek çok anlama gelebilir.
“Anahtar parmak izi” terimi “65834 02604 86283 29728 37069 98932 73120 14774 81777 73663 16574 23234” gibi bir dizi karakterden oluşur ve internetteki bir kişinin doğru özel anahtarı kullandığını ve bu anahtarı yalnızca kendisinin kullandığını teyit etmemizi sağlar.
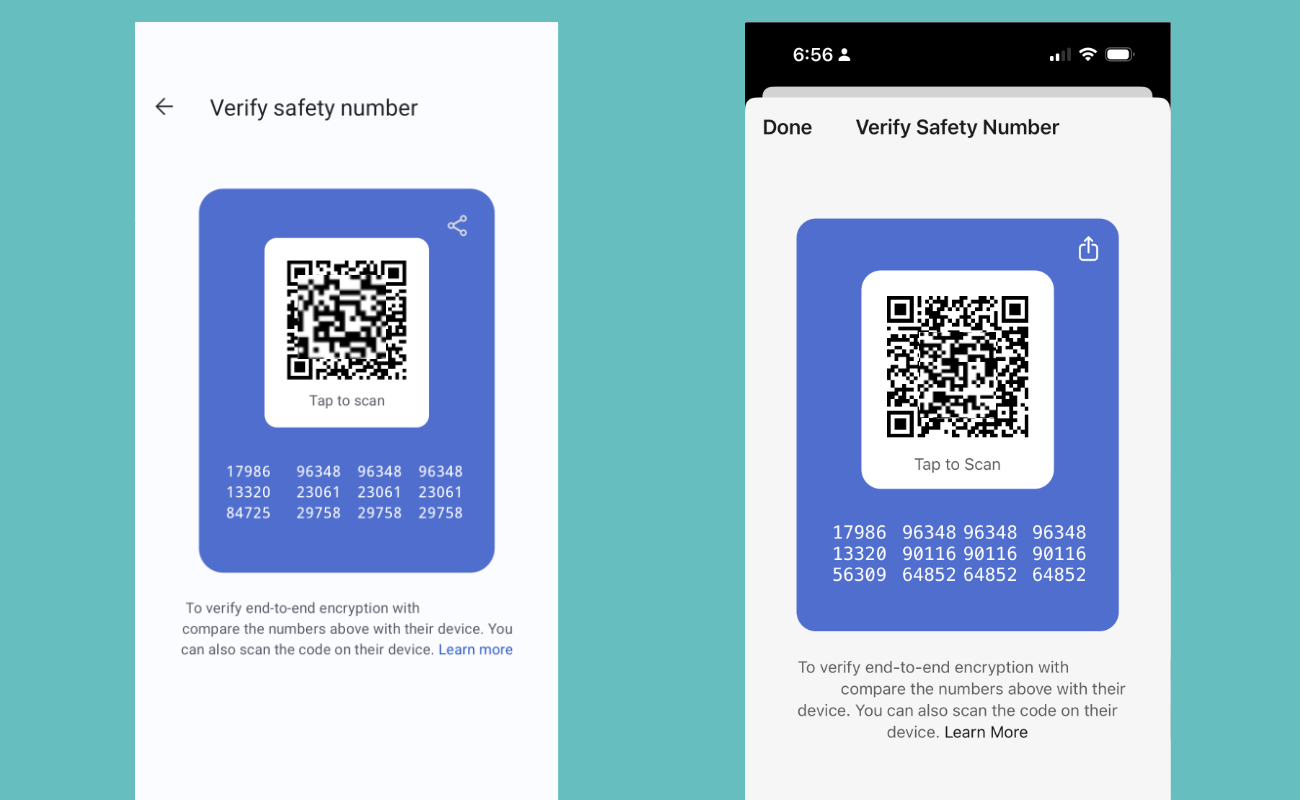
Bazı uygulamalarda bu bilgi, arkadaşınızla cihazlarınızda tarayabileceğiniz bir karekod şeklindedir.
“Parmak izi doğrulama” yoluyla bir dijital kimliğin, gerçek hayattaki kişinin kimliğiyle eşleşip eşleşmediğini kontrol edebilirsiniz. Bu özelliğin işleyişini Signal veya WhatsApp uygulamasında deneyerek daha fazla fikir edinebilirsiniz.
Parmak iziyle doğrulama en iyi gerçek hayatta işe yarar. Arkadaşınızla bizzat buluşamıyorsanız, arkadaşınızın elindeki açık anahtar parmak iziyle sizin yolladığınız açık anahtar parmak izindeki karakterlerin her birinin eşleştiğini kontrol etmesini sağlayın. “342e 2309 bd20 0912 ff10 6c63 2192 1928” gibi bir dizi karakteri kontrol etmek sıkıcı olmakla beraber, yazışmalarınızı güvence altına almak için elzemdir. Bizzat görüşemeyecekseniz, uçtan uca şifrelenmiş bir mesajlaşma veya sohbet sistemi gibi güvenli bir başka kanal üzerinden parmak izinizi yollayabilirsiniz.
Bir kişinin anahtar parmak izini doğruladığınızda, aldığınız mesajın gerçekten o kişiden gelme olasılığı iyice yüksektir. Ama bu işlem yine de mükemmel değildir. Eğer özel anahtarlar kopyalanır veya çalınırsa (cihazınıza kötü amaçlı yazılım bulaşmış olabilir ya da biri bilgisayarınıza fiziksel erişim yoluyla girip dosyayı kopyalayabilir), başka biri aynı parmak izini kullanabilir. Bu sebeple, eğer özel anahtarınız “çalınırsa”, yeni bir açık ve özel anahtar çifti üretmeniz ve yeni açık anahtar parmak izinizi arkadaşlarınızla paylaşmanız gerekir.
Özet: Açık Anahtarlı Şifrelemenin Kabiliyetleri
Açık anahtarlı şifreleme genellikle kullanıcılara aşağıdaki güvenceleri verir:
Gizlilik: Açık anahtarla şifrelenen bir mesaj, gönderene gizli bir mesaj oluşturma olanağı vererek yalnızca istenilen alıcının o mesajı okumasını sağlar.
Kimlik Doğrulama: Açık anahtarlı şifrelemeyle imzalanmış bir mesajın alıcısı, eğer ellerinde göndericinin açık anahtarı bulunuyorsa, mesajın gerçekten gönderici tarafından yazıldığını doğrulayabilir.
Bütünlük: Genel itibarıyla, açık anahtarla şifrelenen bir mesajın içeriği değiştirilemez. Aksi takdirde mesaj doğru biçimde çözülemez ve doğrulanamaz. Yani mesajın iletiminde geçici bir ağ sorunu gibi istenmeyen bir aksaklık bile yaşansa, bu sorun kendini belli eder.
Web Siteleri ve Servisler İçin Kimlik Doğrulama Güvenlik Sertifikaları
Şöyle düşünebilirsiniz: “Açık anahtar parmak izlerini doğrulayabiliyorum, ama bunun web sitelerine yönelik versiyonu nedir?” Bir web sitesinin gerçek olup olmadığını nasıl kontrol edebilirim? Bir servise bağlantı kurduğum esnada kimsenin buna müdahale etmediğinden nasıl emin olabilirim?”
Bilgisayarınız, taşıma katmanı şifrelemesi esnasında bir servisin açık anahtarının kimliğini otomatik olarak doğrular ve anahtarın istenilen servisi şifreleyip şifrelemediğini kontrol eder. Buna “güvenlik sertifikası ” denir.
Aşağıda genel bir internet tarayıcısında SSD için oluşturulan güvenlik sertifikasını görebilirsiniz. Bu bilgilere genellikle web tarayıcınızdaki HTTPS kilidine veya seçenekler paneline tıklayarak ve sertifika ayrıntılarını görüntüleyerek erişebilirsiniz.
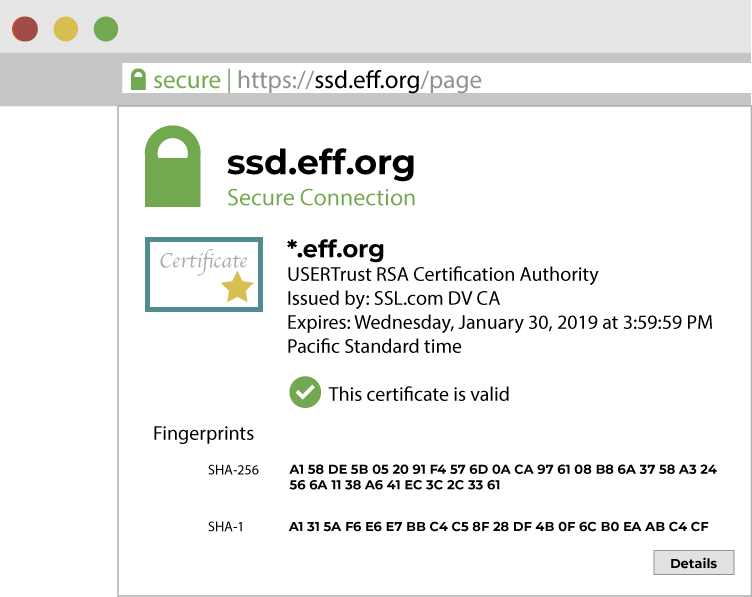
Bilgisayarınızdaki web tarayıcısı HTTPS kullanan sitelerle şifreli bağlantılar kurabilir. Web siteleri genellikle bağlantınızı değiştiren başka bir sisteme değil, güvenli biçimde gerçek siteye bağlandığınızı ispatlamak için güvenlik sertifikaları kullanır. Web tarayıcıları alan adlarının açık anahtarlarını kontrol etmek için sertifikaları inceler (Örnek: www.duckduckgo.com, www.wikipedia.org, veya ssd.eff.org). Bir kişiye veya web sitesine ait doğru anahtara sahip olduğunuzu sertifikalarla saptayabilir, böylelikle güvenle etkileşime geçebilirsiniz.
Peki bilgisayarınız ziyaret ettiğiniz sitelere ait doğru açık anahtarı nasıl saptayacaktır?
Modern tarayıcılar ve işletim sistemleri güvenilir Sertifika Yetkilileri (CA) listesi içerir. Bu CA’lara ait açık anahtarlar kullanacağınız tarayıcıyı indirdiğinizde veya bilgisayarınızı satın aldığınızda paket olarak gelir. Sertifika Yetkilileri, web sitelerinin açık anahtarlarının ilgili alanı meşru yollarla işlettiğini doğruladıktan sonra anahtarları imzalar. (Örnek: www.example.com). Tarayıcınız bir HTTPS sitesine girdiğinde, sitenin verdiği sertifikanın tarayıcının güvendiği bir CA tarafından imzalandığını doğrular. Bu durum, güvenilir bir üçüncü tarafın, ilgili sitenin gerçek olduğunu doğruladığını gösterir.
Bir sitenin sertifikasının Sertifika Yetkilisi tarafından imzalanması, o web sitesinin güvenli olduğu anlamına gelmez. CA’nın doğrulayabildiği öğeler sınırlı olduğundan, web sitelerinin dürüst veya güvenilir olduğunu teyit edemez. Örneğin, HTTPS kullanan bir web sitesi “güvence altına alınabilir” ama dolandırıcı ve kötü amaçlı yazılımlar bulundurabilir. Dikkatli olun ve daha fazla bilgi edinmek için kötü amaçlı yazılım ve kimlik avı saldırılarıyla ilgili kılavuzlarımızı okuyun.
Web’de zaman zaman sertifikalarla ilgili hata mesajları görürsünüz. Bu durum genellikle, sizi internette önce giriş portalına yönlendirmek isteyen bir otel veya kafe ağının, girmeye çalıştığınız web sitesine erişiminizi engellemesinden ya da sertifika sistemindeki bürokratik bir hatadan kaynaklanır. Ama kimi zaman da hackerlar, hırsızlar, polis veya gizli servis yetkilileri şifrelenmiş bağlantıyı kesiyor olabilir. Ne yazık ki bu iki durum arasında ayrım yapmak çok zordur.
Bu sebeple, size ait bir hesabın bulunduğu veya hassas bilgiler okuduğunuz bir siteye girerken sertifika uyarısıyla karşılaştığınızda, asla uyarıyı göz ardı edip siteye girmemelisiniz.
Bütün Öğeleri Birleştirelim: Simetrik Anahtarlar, Asimetrik Anahtarlar ve Açık Anahtar Parmak İzleri
Taşıma Katmanı Güvenliğinde El Sıkışma İşlemleri
Taşıma katmanı şifrelemesi kullanırken bilgisayarınızın tarayıcısı ve ziyaret ettiğiniz web sitesinin bilgisayarı hem simetrik, hem asimetrik algoritmalar kullanır.
Bütün bu sıraladığımız fikirlerin nasıl bir arada işlediğini somut bir örnekle inceleyelim: Şu HTTPS web sitesine girdiğinizde ne oluyor? (https://ssd.eff.org/)
Bir web sitesi eğer HTTPS kullanıyorsa, sizin tarayıcınız ve web sitesinin sunucusunun tarayıcısı “el sıkışma” adlı çok hızlı etkileşimlere girer. Kullandığınız Google Chrome, Mozilla Firefox veya Tor Browser vb. tarayıcınız bizim https://ssd.eff.org web sitemizin sunucusuyla konuşur.
El sıkışma esnasında tarayıcı ve sunucu öncelikle birbirine not iletir ve şifreleme algoritmaları konusunda ortak tercihleri olup olmadığını öğrenir (buna “şifreleme takımları” denir). Sanki tarayıcınız ve ssd.eff.org sunucusu kısa bir sohbet ediyormuş gibi düşünebilirsiniz: İkisinin de bildiği ve kullanabileceği şifreleme yöntemlerini ve hangi yöntemleri tercih ettiklerini bulmak için birbirlerine soru sorarlar.
Şuna benzer: “İkimiz de RSA gibi asimetrik bir algoritmayı AES gibi simetrik bir algoritmayla birlikte kullanmayı biliyor muyuz?” Evet, güzel. Eğer bu şifreleme algoritmaları bileşimi işimize yaramazsa, ikimizin de bildiği başka şifreleme algoritmaları var mı?”
Sonrasında tarayıcınız asimetrik şifreleme yoluyla ssd.eff.org’a açık anahtar sertifikası yollar ve kimliğinizi doğrular. Sitenin sunucusu bu açık anahtar sertifikasını açık anahtarınızla eşleştirir. Bu işlemi, kötü amaçlı bir bilgisayarın bağlantınızı ele geçirmesini önlemek için yapar.
Kimliğiniz doğrulandıktan sonra, sitenin sunucusu simetrik şifreleme kullanarak yeni, simetrik, gizli bir anahtar dosyası oluşturur. Sonra da, tarayıcınızın açık anahtarını asimetrik olarak şifreler ve tarayıcınıza gönderir. Tarayıcınız, bu özel anahtarla dosyanın şifresini çözer.
Eğer simetrik anahtar çalışırsa, tarayıcınız ve web sitesinin sunucusu sonraki etkileşimleri şifrelemek için anahtarı kullanmaya devam eder. Bu etkileşimlere taşıma katmanı güvenliği (TLS) el sıkışması denir. Böylece, eğer el sıkışması esnasında her şey yolunda giderse ssd.eff.org’a bağlantınızın güvenli olduğu gözükür ve ssd.eff.org harflerinin önünde HTTPS çıkar.
Anahtar doğrulama işleminin ayrıntıları için şimdi bu kılavuzuokuyabilirsiniz.