How to: Circumvent Online Censorship
Last Reviewed: August 09, 2017
This guide is out of date. Please refer to our new version, Understanding and Circumventing Network Censorship.
This is a short overview to circumventing online censorship, but is by no means comprehensive.
Governments, companies, schools, and Internet providers sometimes use software to prevent their users from accessing certain websites and services. This is called Internet filtering or blocking, and it is a form of censorship. Filtering comes in different forms. Censors can block individual web pages, or even entire websites. Sometimes, content is blocked based on the keywords it contains.
There are different ways of beating Internet censorship. Some protect you from surveillance, but many do not. When someone who controls your net connection filters or blocks a site, you can almost always use a circumvention tool to get to the information you need. Note: Circumvention tools that promise privacy or security are not always private or secure. And tools that use terms like “anonymizer” do not always keeps your identity completely secret.
The circumvention tool that is best for you depends on your threat model . If you’re not sure what your threat model is, start here.
In this article, we'll talk about four ways to circumvent censorship:
- Visiting a web proxy to access a blocked website.
- Visiting an encrypted web proxy to access a blocked website.
- Using a Virtual Private Network (VPN ) to access blocked websites or services.
- Using the Tor Browser to access a blocked website or protect your identity.
Basic techniques
Circumvention tools usually work by diverting your web traffic so it avoids the machines that do the blocking or filtering. A service that redirects your Internet connection past these blocks is sometimes called a proxy.
HTTPS is the secure version of the HTTP protocol you use to access websites. Sometimes a censor will only block the insecure (HTTP) version of a site. That means you can access the blocked site simply by entering the version of the web address that starts with HTTPS.
This is useful if the censorship you are fighting blocks individual web pages based on their contents. HTTPS stops censors from reading your web traffic, so they cannot tell what keywords are being sent, or which individual web page you are visiting.
Censors can still see the domain names of all websites you visit. So, for example, if you visit “eff.org/https-everywhere” censors can see that you are on “eff.org” but not that you are on the “https-everywhere” page.
If you suspect this type of simple blocking, try entering https:// before the domain in place of http:
Try installing EFF’s HTTPS Everywhere extension to automatically turn on HTTPS where possible.
Another way that you may be able to circumvent basic censorship techniques is by trying an alternate domain name or URL. For example, instead of visiting http://twitter.com, you might try the mobile version of the site at http://m.twitter.com. Censors that block websites or web pages work from a blacklist of banned websites, so anything that is not on that blacklist will get through. They might not know of all different versions of a particular website's name—especially if the administrators of the site know it is blocked and register more than one domain.
Web-based proxies
A web-based proxy is a website that lets its users access other blocked or censored websites. It is therefore a good way to circumvent censorship. In order to use a web-based proxy, visit the proxy and enter the web address that you want to see; the proxy will then display the web page you asked for.
However, web-based proxies don’t provide any security and will be a poor choice if your threat model includes someone monitoring your internet connection. They will not help you to use blocked services such as your instant messaging apps. The web-based proxy will have a complete record of everything you do online, which can be a privacy risk for some users depending on their threat model.
Encrypted proxies
Numerous proxy tools utilize encryption to provide an additional layer of security on top of the ability to bypass filtering. The connection is encrypted so others cannot see what you are visiting. While encrypted proxies are generally more secure than plain web-based proxies, the tool provider may have information about you. They might have your name and email address in their records, for instance. That means that these tools do not provide full anonymity.
The simplest form of an encrypted web proxy is one that starts with “https”— this will use the encryption usually provided by secure websites. However, be cautious—the owners of these proxies can see the data you send to and from other secure websites. Ultrasurf and Psiphon are examples of these tools.
Virtual Private Networks
A Virtual Private Network (VPN) encrypts and sends all Internet data from your computer through another computer. This computer could belong to a commercial or nonprofit VPN service, your company, or a trusted contact. Once a VPN service is correctly configured, you can use it to access webpages, e-mail, instant messaging, VoIP , and any other Internet service. A VPN protects your traffic from being spied on locally, but your VPN provider can still keep logs of the websites you access, or even let a third party snoop directly on your web browsing. Depending on your threat model, the possibility of a government listening in on your VPN connection or getting hold of VPN logs may be a significant risk. For some users, this could outweigh the short-term benefits of using a VPN.
For information about choosing a VPN service, click here.
Tor
Tor is open-source software designed to give you anonymity on the web. Tor Browser is a web browser built on top of the Tor anonymity network. Because of how Tor routes your web browsing traffic, it also allows you to circumvent censorship. (See our How to: Use Tor guides for Linux, macOS and Windows).
When you first start the Tor Browser, you can choose an option specifying that you are on a network that is censored:
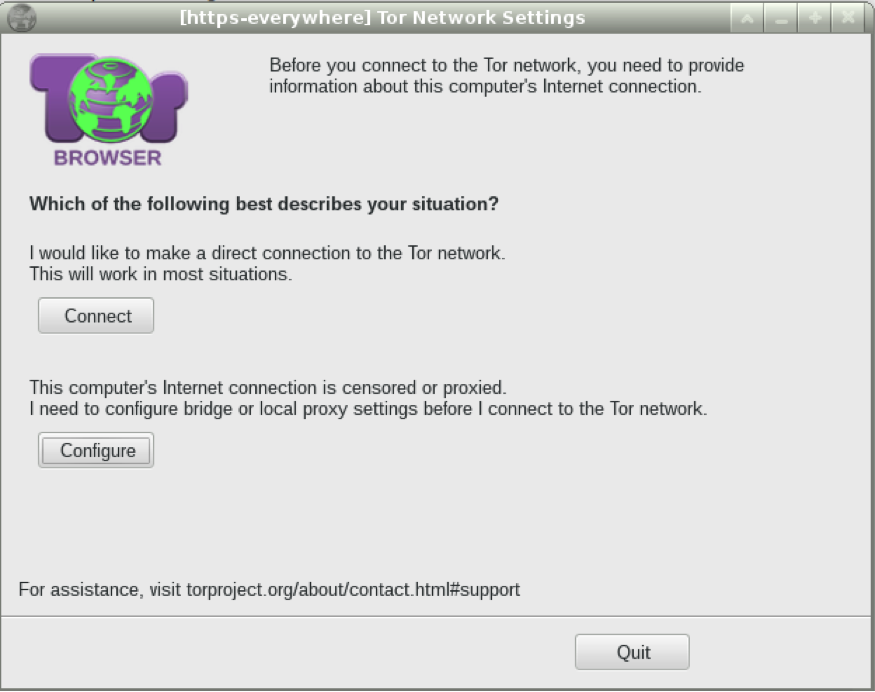
Tor will not only bypass almost all national censorship, but, if properly configured, can also protect your identity from an adversary listening in on your country’s networks. It can, however, be slow and difficult to use.
To learn how to use Tor on a desktop machine, click here for Linux, here for macOS, or here for Windows, but please be sure to tap “Configure” instead of “Connect” in the window displayed above.

