Choosing the VPN That's Right for You
Last Reviewed: May 08, 2024
A recently published attack technique, called TunnelVision, demonstrates how most commercial VPNs are susceptible to an attack where, if an attacker is on the same local network as you (such as at a coffee shop or on hotel Wi-Fi), they may be able to reroute your traffic through their computer to spy on your traffic—essentially rendering a VPN ’s already very limited security benefits on public Wi-Fi useless, since HTTPS will already make any user data on a site encrypted to them, VPN or not. VPNs are still useful in certain circumstances for circumventing certain types of network censorship, but it’s best not to consider them a security tool on public networks. We’ll be updating this guide in the future as we see how—or if—VPN providers can implement fixes. In the meantime, consider looking through a provider’s blog or news page to see if they’re acknowledging TunnelVision before choosing to use one.
VPN stands for “Virtual Private Network.” When you connect to a VPN, all data that you send (such as the requests to servers when browsing the web) appears to originate from the VPN itself, rather than your internet service provider (ISP). This masks your IP address , which can be an important tool for protecting your privacy, since your IP address provides an indication of your general location and can therefore be used to identify you.
In practice, VPNs can:
-
Protect your internet activity from prying eyes, especially if you’re connected to an unsecure Wi-Fi network in a café, airport, library, or somewhere else. This has become a less critical aspect of VPNs as the majority of web traffic is now encrypted using HTTPS, but in certain situations, where you may not want a network operator or ISP to see your basic web traffic, a VPN is still useful.
-
Circumvent internet censorship on a network that blocks certain sites or services. For example, when you are working from a school’s internet connection or in a country that blocks content. Note: it’s important to keep up to date on security news for specific countries’ policies on VPNs.
-
Connect you to the corporate intranet at your office while you’re traveling abroad, at home, or any other time you are out of the office.
One common misconception is that VPNs are just for desktop computers. Logging in to strange or unfamiliar Wi-Fi connections from your phone can be just as risky as logging onto a strange Wi-Fi network from your computer. You can have a VPN on your phone to encrypt traffic from your carrier and ISP.
There is no one-size-fits-all solution when it comes to VPNs. Just like email, there are many VPN services out there and you should choose the service that works best for you. Depending on which one you choose, you can benefit from an increased level of security when connected to networks you wouldn’t ordinarily trust. But this means you're placing your trust in the VPN.
So do you need a VPN? And which VPN should you use? This guide will help you think through what tools are right for you, and what factors you should consider in your search for a VPN.
Let’s Start With the Basics: How do VPNs Actually Work? anchor link
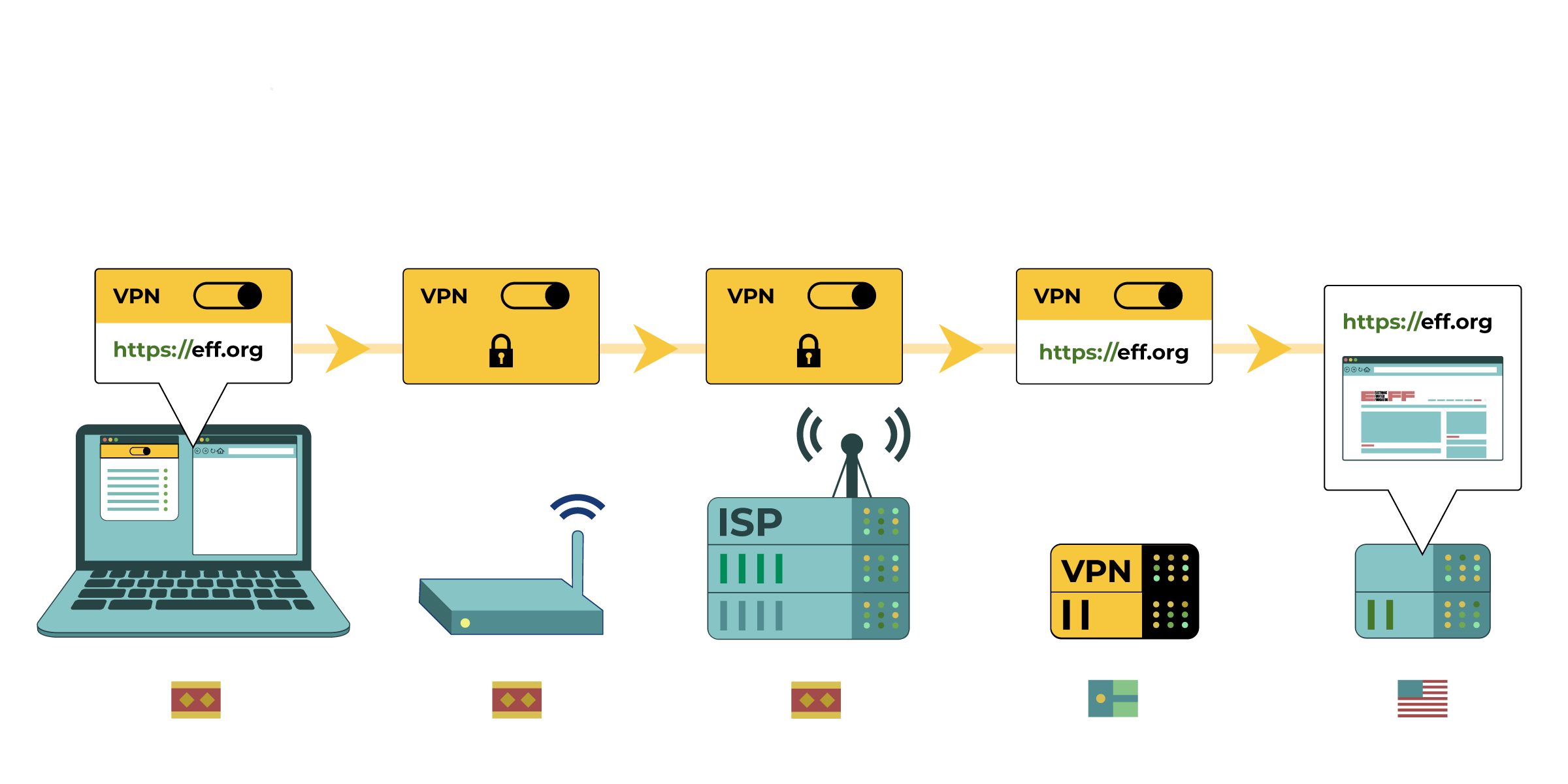
A VPN routes all your web traffic through an "encrypted tunnel" between your devices and the VPN server. Then, the traffic leaves the VPN to its ultimate destination, masking your original IP address. From a website's point of view, it appears your location is wherever the VPN server is. A VPN also hides your web browsing from your ISP and the local network owner (like a coffee shop or hotel). This is important because according to a 2021 report, the FTC found ISPs in the U.S. share more of your browsing data with third-parties than you might expect. However, while a VPN hides your browsing data from the ISP, it's all visible to the VPN provider.
For additional information, this article from the Center for Democracy & Technology covers more of the technical aspects.
Things to Consider: What VPNs Don’t Do anchor link
A VPN protects your internet traffic from surveillance on the public network, but it does not protect your data from the private network you’re using. If you are using a corporate VPN, then whoever runs the corporate network will see your traffic. If you are using a commercial VPN , whoever runs the service will see your traffic.
A disreputable VPN service might do this deliberately, to collect personal information or other valuable data.
The manager of your corporate or commercial VPN may also be subject to pressure from governments or law enforcement to turn over information about the data you have sent over the network. You should review your VPN provider’s privacy policy for information about the circumstances under which your VPN provider may turn your data over to governments or law enforcement.
You should also take note of the countries in which the VPN provider does business. The provider will be subject to the laws of those countries, including laws governing government requests for information. Laws vary from country to country, and sometimes those laws allow officials to collect information without notifying you or giving you an opportunity to contest it. The VPN provider may also be subject to legal requests for information from countries with whom the countries in which it operates have a legal assistance treaty.
Most commercial VPNs require you to pay using a credit card, which includes information about you that you may not want to disclose to your VPN provider, as it can easily be linked back to your identity. If you would like to keep your credit card number from your commercial VPN provider, use a VPN provider that accepts gift cards, or use temporary or disposable credit card numbers. Also, note that the VPN provider may still collect your IP address when you use the service, which can also be used to identify you, even if you use an alternative payment method. If you would like to hide your IP address from your VPN provider, you could use Tor when connecting to your VPN, or connect to the VPN only from a public Wi-Fi network.
A VPN is not a tool for anonymity, and while it can protect your location from some companies, there are many other ways companies may track you, including GPS, web cookies , tracking pixels, or fingerprinting.
For many circumstances, a VPN isn't the most important security step to take. Instead, using strong passwords, setting up two-factor authentication, enabling HTTPS-only mode, encrypting your devices, running software updates, and blocking trackers, are a more impactful step to securing yourself online.
How Do I Choose a VPN That’s Right For Me? anchor link
Everyone has different needs for how they hope to use a VPN. And the range and quality of VPNs varies a lot from one service to another. To find the VPN that’s right for you, you can evaluate VPNs based on the following criteria:
Claims anchor link
Is the VPN provider making claims about their product or services? Maybe they claim not to log any user connection data (see data collection below), or they claim not to share or sell data. Remember that a claim is not a guarantee, so be sure you verify these claims. Dig deep into a VPN provider’s privacy policy to uncover details about how your data is monetized, even if the VPN doesn’t sell it to third parties directly. On the VPN's marketing pages, keep an eye out for hyperbolic claims around privacy or security, too, as any VPN that makes impossible claims may not be trustworthy in other areas.
Trust and transparency anchor link
VPN providers can subject their service to third-party security audits, preferably annually, with results which are then made public. This type of transparency can reveal otherwise unknown security vulnerabilities in the VPN apps, data access, and infrastructure. As a potential subscriber, it's a sign the VPN provider is trying to take security seriously. But there's no certainty that the practices aren't changed after the audit, especially if compelled to do so by a government.
Business model anchor link
Even if a VPN isn’t selling your data, it must be able to stay in operation somehow. If the VPN doesn’t sell its service, how is it keeping its business afloat? Does it solicit donations? What is the business model for the service? Some VPNs run on a “freemium” model, meaning they are free to join, but after you hit a data cap they charge you. VPNs can be entirely free, but sell your data. They can use a recurring subscription, which will keep charging you if you forget to cancel. If your budget is constrained, this is useful information to know. VPNs may also throw in extra features, like ad and tracker blocking , though they provide you with much less control than an ad blocking browser extension.
Reputation anchor link
It is worthwhile to do a search on the people and organizations associated with the VPN. Is it endorsed by security professionals? Does the VPN have news articles written about it? If the VPN was established by people known in the information security community, it is more likely to be trustworthy. Be skeptical of a VPN offering a service that no one wants to stake their personal reputation on, or one that is run by a company that no one knows about. It can be beneficial to look for a VPN's "about" page to see if it lists its founders or employees. Transparency of leadership isn't a guarantee that a company is reputable, but it is a sign the company is trying to establish trust.
Data collection anchor link
A service that does not collect data in the first place will not be able to sell that data. When looking through the privacy policy, see whether the VPN actually collects user data and whether it sells it. A VPN company might log your data if it doesn't specifically rule it out in its privacy policy. And, depending on jurisdiction, a government can demand that data or issue a subpoena for it.
Even if a company claims not to log connection data, this is not a guarantee of good behavior. We encourage you to investigate instances where a VPN has been mentioned in the media. They may have been caught misleading or lying to their customers.
Encryption anchor link
How safe is the VPN encryption ? If a VPN is using broken encryption—such as Point-to-Point Tunneling Protocol (PPTP)—any data flowing through it can be easily decrypted and viewed by your ISP or country. Check to see if the VPNs use one of two different protocols, OpenVPN and WireGuard, which have become standard. Though, OpenVPN use seems to be on the decline in recent years, and some VPN providers may use their own implementations of Wireguard. If you’re using a work VPN, contact your IT department and inquire about the security of the connection.
EFF cannot vouch for any VPN or ratings. Some VPNs with exemplary privacy policies could be run by devious people. Do not use a VPN that you do not trust.
Remember: There is no one-size-fits-all VPN. There are many factors to consider when choosing a VPN. Always remember to consider your security plan before making any decisions about the tools you use to protect your digital security.

