深入解析端到端加密:公钥加密系统是如何运作的?
最后更新: January 01, 2025
在开始前,我们建议您先阅读以下指南以巩固相关概念(如果您尚未阅读的话):《关于加密,我应该了解什么?》、《加密的核心概念》,以及《密钥验证》。
若使用得当,端到端加密有助于确保消息、文本和文件内容仅被目标接收者读取。端到端加密工具可防止网络窃听者及服务提供商阅读消息,同时还能验证消息来源的真实性且内容未经篡改。
端到端加密工具曾因配置复杂而难以普及,但如今已大幅简化。例如,Signal 等安全通信工具通过端到端加密来保护收发双方的消息,同时又保持了易用性。甚至 WhatsApp 和 Facebook Messenger 等大型平台也支持端到端加密,且无需预先设置。
本指南讨论的加密类型称为公钥密码学(亦称“公钥加密”),这也是端到端加密工具的核心。
理解公钥密码学的基本原理将助您安全使用这些工具。公钥密码学的能力与局限同样值得了解。
加密的作用
发送秘密消息时,具体的加密流程如下:
- 明文消息首先被加密为不可读的乱码(例如将“hello mum”变为“OhsieW5ge+osh1aehah6”)。
- 加密后的消息通过网络传输,窃听者仅能截获乱码(即“OhsieW5ge+osh1aehah6”)。
- 消息抵达目标接收者后,仅接收者可通过特定方式将其解密为原始消息(将“OhsieW5ge+osh1aehah6”还原为“hello mum”)。
对称加密:单密钥传递秘密纸条的故事
让我们先来看看历史上的真实案例:凯撒密码。
Julia 想给朋友 César 传递消息:“在花园见。”但又不愿让同学窥探。
若直接传递明文纸条,消息需经多位同学中转。尽管中转者保持中立,但他们仍会好奇,可能会偷看、复制消息或记录消息传递的时间。
为保护隐私,Julia 决定用“三位移位密钥”来加密消息:将每个字母按字母表后移三位(例如 A→D,B→E,依此类推)。
若 Julia 与 César 使用此简单密钥来加密/解密,以乱码显示的消息或可迷惑同学,但仍易被破解。任何同学均可通过“暴力破解”法尝试所有可能的位移组合,直至破译部分单词。也就是说,他们可以不断地猜测,直到破解消息。
这种将字母按字母表移动三位的方法是凯撒大帝使用过的加密方法,颇具历史意义,故称“凯撒密码”。当加密与解密使用同一密钥时,称为对称密码学。
凯撒密码是对称密码学的一种较弱的形式。现代加密技术已大幅进步:密钥不再依赖简单的字母位移,而是通过数学运算与计算机生成长串数字,从而大幅提升破译难度。
然而,对称密码学仍存在漏洞:若窃听者截获 Julia 与 César 共享的密钥,然后用来解密消息呢?若窃听者通过观察发现其解密密钥为“三位移位”,那又该如何呢?
César 与 Julia 怎样才能解决此问题?
如今的最佳答案是公钥密码学。在公钥密码学中,加密密钥与解密密钥不同,且公钥可安全共享(只要私钥保持私密即可)。
公钥密码学:双密钥的故事
让我们深入问题核心:发送者如何在不被窃听的情况下将对称密钥传递给接收者?
公钥密码学(亦称“非对称密码学”)完美地解决了这个问题。它支持对话双方生成两把密钥:公钥与私钥。二者虽名为“钥匙”,实为具备特定数学属性的超大数字。若用某人的公钥加密消息,则只能由对方使用匹配的私钥解密。
如今,Julia 与 César 已告别课堂纸条,转而使用计算机通过公钥密码学发送加密消息。此前负责传递纸条的同学被计算机取代,成为 Julia 与 César 之间的“中转者”:他们各自的 Wi-Fi 节点、互联网服务提供商及邮件服务器。现实中,可能有数百台计算机参与 Julia 与 César 的消息中转,这些中转节点如同好奇的同学,会复制并存储流经的消息。
Julia 与 César 虽不介意中转者知晓其通信,但希望消息内容保持私密。
首先,Julia 需要获得 César 的公钥。César 通过非安全渠道(如未加密邮件)发送公钥。(好消息:现代通信应用可自动代替 César 完成此步骤,但手动操作仍有助于理解原理。)
César 并不担心中转者获取公钥,因为公钥本就可以自由共享(此时,密钥的比喻已不太恰当;将公钥视为字面意义上的钥匙并不正确:其本质是具特定数学属性的超大数字,常编码为字符串)。为安全起见,César 通过邮件与短信等多渠道发送公钥,以降低中转者替换公钥的风险。
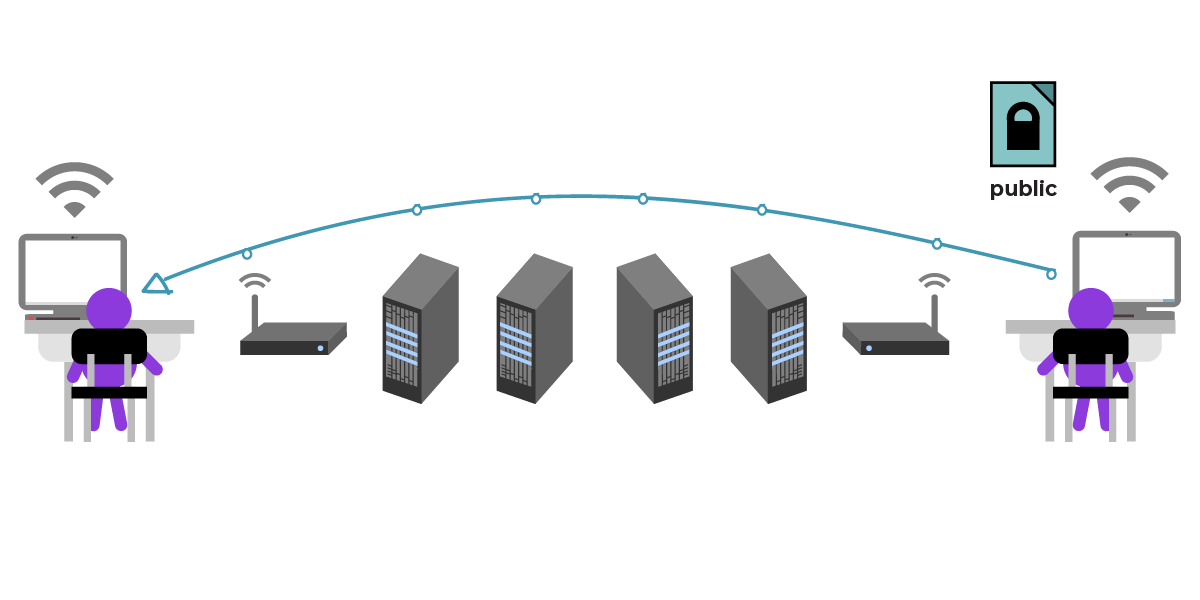
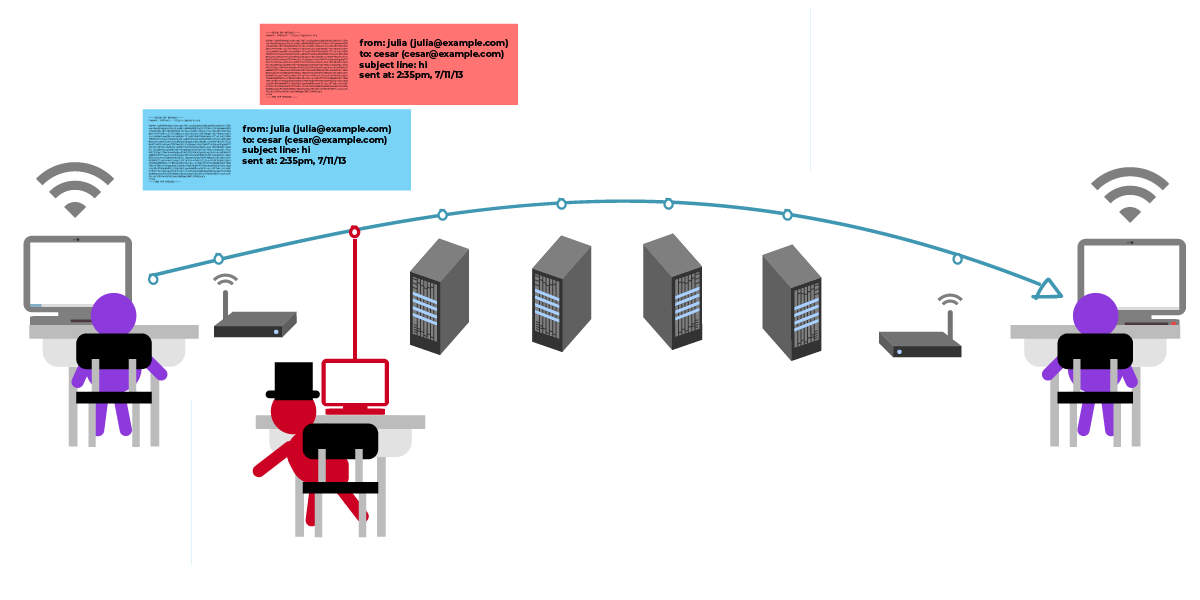
Julia 收到了 César 的公钥。现在,Julia 可以用它加密消息“在花园见”。
Julia 发出经过加密的消息。该消息仅面向 César 加密。
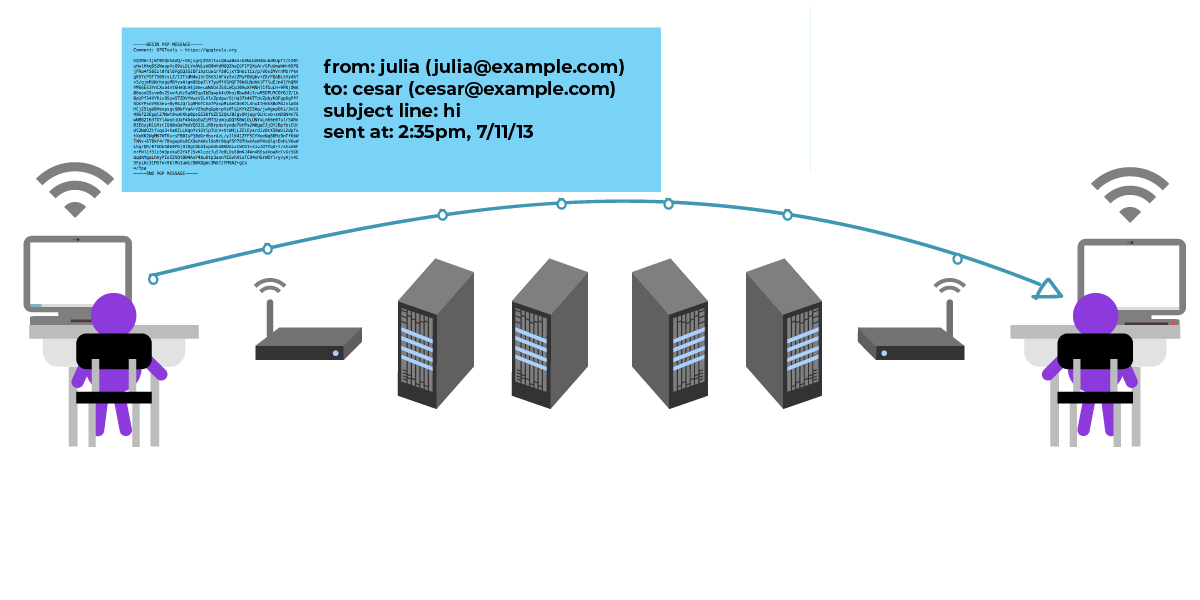
Julia 和 César 都能理解此消息,但对其他人来说,消息内容看起来都是乱码。但中转者仍能查看元数据(如主题、日期、发件人和收件人)。
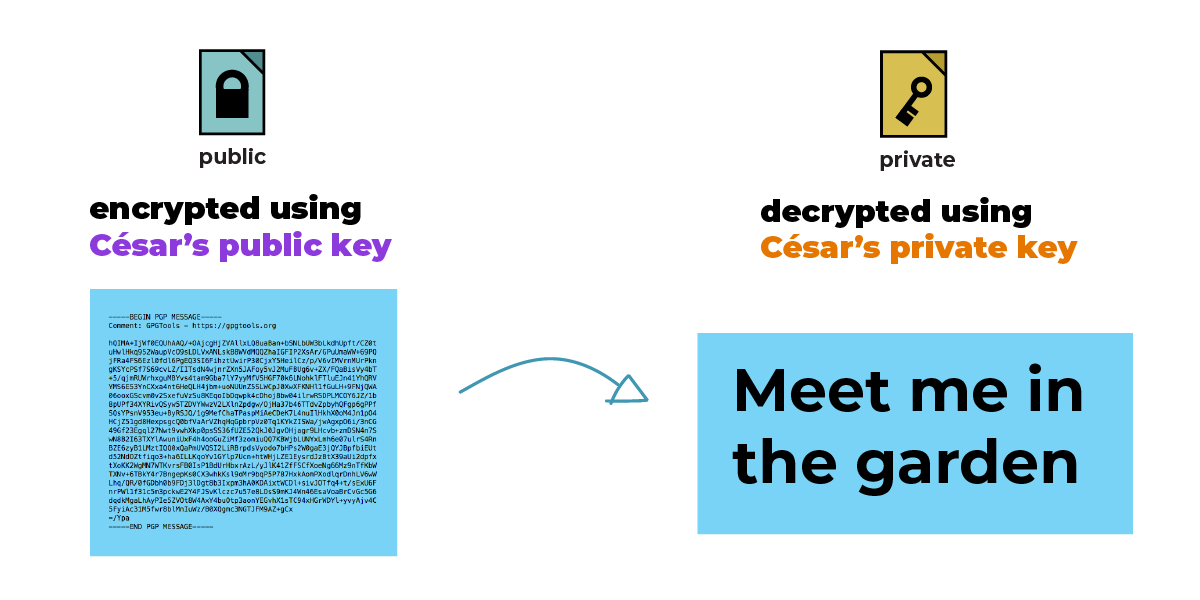
由于消息被加密为 César 的公钥,因此只有 César 和发件人 (Julia) 能解锁并读取消息的内容。
César 可使用私钥解密消息。

总结:
- 公钥密码学支持通过开放、非安全渠道传递公钥。如今,通信应用能够为用户自动完成此过程。
- 持有对方的公钥可加密发送给对方的消息。
- 私钥则用于解密发送给自己的加密消息。
- 整个过程中,中转者(如邮件服务提供商、互联网服务提供商及其网络用户)均可查看元数据,包括通信双方、接收时间、主题内容及加密状态等信息。
另一个问题:如何防范身份冒充?
在 Julia 与 César 的示例中,中转者始终可查看元数据。
我们假设中转者中存在恶意攻击者(即,试图窃取或篡改信息以实施伤害的人)。此攻击者意图窥探 Julia 发送给 César 的消息。
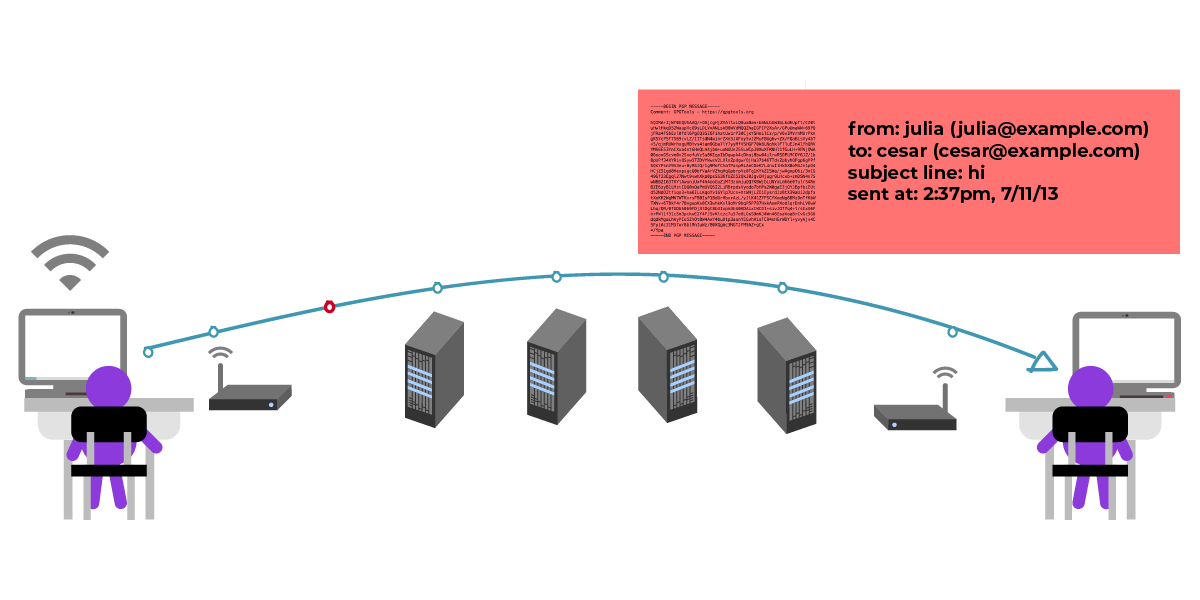
假设攻击者成功诱骗 Julia 获取错误的 César 公钥文件,而 Julia 并未察觉此公钥实际上不是 César 的。此时,攻击者将实际接收 Julia 的消息,窥探后再转发给 César。
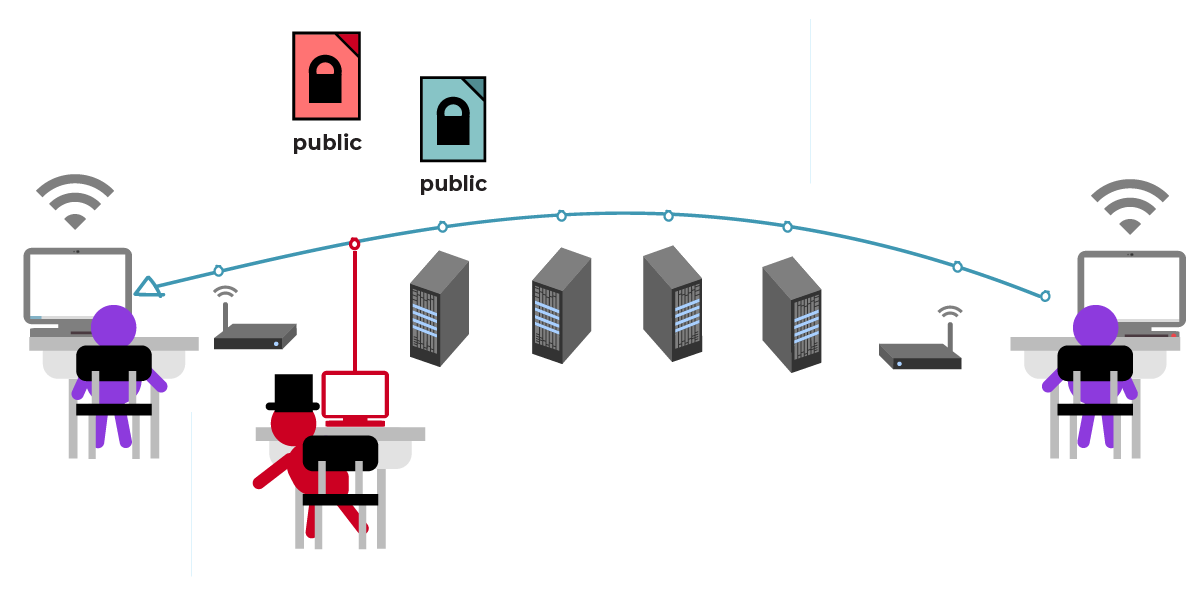
攻击者可选择篡改消息内容后再转发。例如,将“在花园见”改为“在自助餐厅见”。
但多数情况下,攻击者会按原样转发消息。于是,攻击者将 Julia 的消息原样发送给 César,César 按约定前往花园与 Julia 相会,却骇然发现攻击者也在那里!
此类攻击称为“中间人攻击”或“机器中间人攻击”。
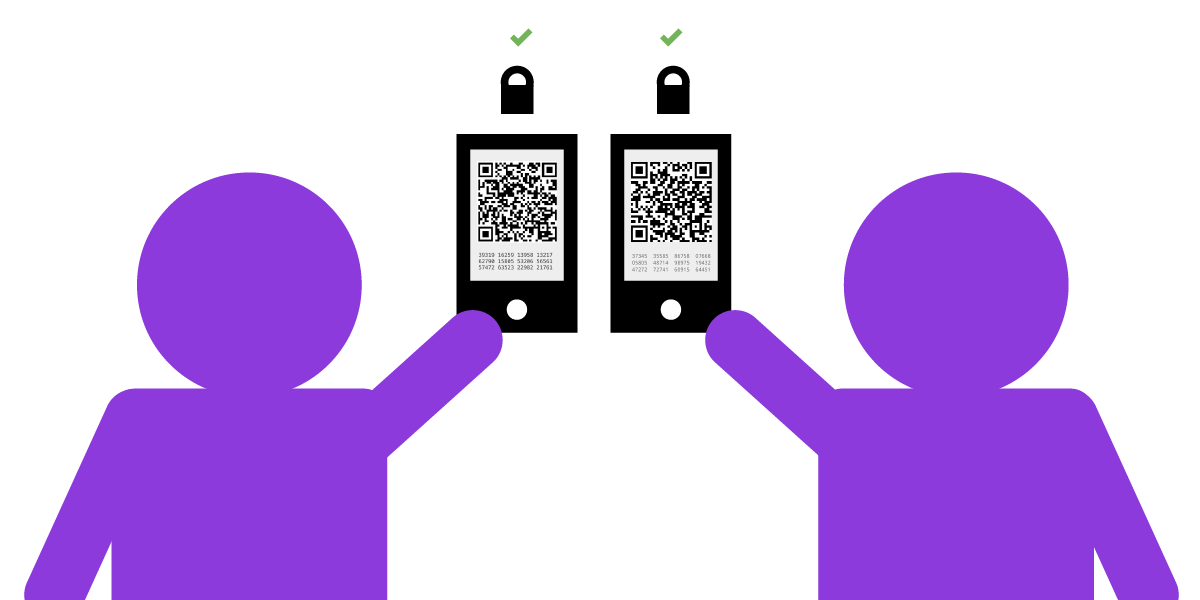
幸运的是,公钥密码学可通过“指纹验证”防范中间人攻击。如有可能,此操作最好在线下当面进行:可以将您的公钥指纹与对方设备存储的信息逐字比对,以确认准确无误。此过程虽繁琐但至关重要。
不同端到端加密应用所采用的指纹验证名称和方式也各不相同。例如,逐字符比对双方设备显示的指纹。或者扫描对方手机二维码以“验证设备”。在下例中,Julia 与 César 通过手机摄像头扫描彼此的二维码,进行线下验证指纹。
实际案例可参考 Signal 的“验证安全号码”或 WhatsApp 的“验证安全码”功能。
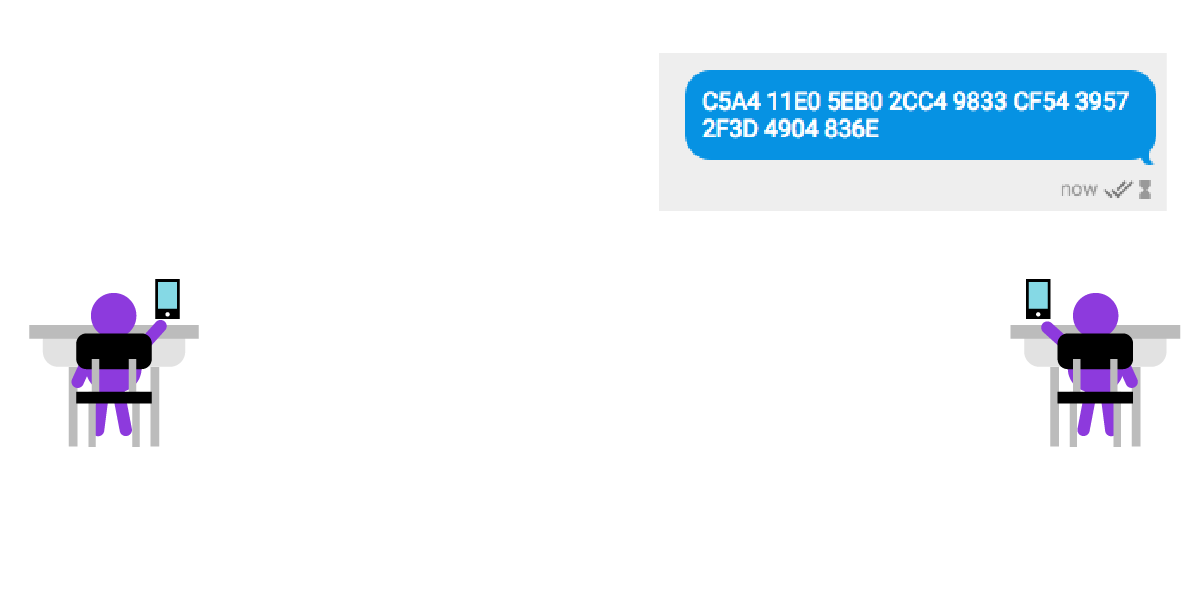
若无法线下验证,可通过其他安全渠道(如另一款端到端加密通信应用或视频通话)共享指纹。
在下例中,César 通过手机上的另一款端到端加密应用向 Julia 发送公钥指纹。
回顾:
- 中间人攻击是指攻击者拦截您发送给其他人的消息,然后篡改并发送或单纯进行窃听。
- 公钥密码学通过“指纹验证”来验证收发双方的身份,从而防范中间人攻击。
- 除了用于加密发送给目标收件人的消息外,公钥还带有“公钥指纹”,可用于验证收件人的身份。
- 私钥用于加密消息并进行数字签名(见下文)。
数字签名
若使用某公钥加密消息,则只有匹配的私钥可解密。反之亦然:用某私钥加密的消息也只有匹配的公钥可解密。
这有什么实际用处呢?假设您编写了一条消息“我承诺向 Aazul 支付 100 美元”,并用私钥进行加密。任何人均可解密此消息,但只有私钥持有者可生成该消息。若私钥保管得当,即表明,消息确实由您本人发出,也只能由您发出。使用您的私钥加密消息,即表示您确认自己的发件人身份。
换句话说,您对这条数字信息执行的操作与现实中签署文件等效,此过程称为“签名”。
签名也是数种防篡改方式中的一种。若攻击者试图“向 Aazul 支付 100 美元”的消息改为“向 Ming 支付 100 美元”,其无法用您的私钥重新签名。签名消息可保证消息来源真实且传输中未经篡改。
回顾:公钥密码学的实践
我们来总结一下。公钥密码学支持您安全地向任何已知公钥者加密并发送消息。
若他人知晓您的公钥:
- 可发送仅您能使用配对的私钥进行解密的加密消息。
- 您可用私钥签名消息,使接收者确认消息来源。
- 如今,通讯应用可为用户自动管理公钥和私钥并提供更友好的验证机制,使任何人都可以轻松地使用公钥加密,甚至对此毫无察觉。
若您知晓他人公钥:
- 可解密其签名消息并确认来源的真实性。
公钥的传播范围越广,其效用就越大。您可将公钥分享给任何希望与您通信的人。
公钥始终与名为私钥的文件配对。私钥如同实体钥匙,需严格保护。私钥既用于加密也用于解密消息。
若私钥意外从您的设备上删除,您将无法解密已加密的消息。若他人盗取了您的私钥(通过物理接触计算机、安装恶意软件或误操作),就能读取您的加密消息,还可以冒充您进行签名,声称消息是您撰写的。
政府窃取重要人士的私钥(如扣押设备或通过物理接触/钓鱼攻击来安装恶意软件)的情况时有耳闻。如此一来,公钥密码学提供的保护化为乌有。
这好比您安装了无法撬开的门锁,但有人窃取并复制了您的钥匙,再把它放回您的口袋。然后,此人无需撬锁即可自由出入您的住所。
您应根据安全计划来评估风险并加以应对。若您认为可能有人千方百计窃取您的私钥,建议避免使用浏览器内置的端到端加密方案,而应将私钥存储在属于您自己的电脑或手机上,而非属于他人的设备(如云端或服务器)。
公钥密码学的实际应用
前文分别解释了对称加密与公钥加密,但公钥加密也包含对称加密技术。公钥加密会加密一个对称密钥,后者再用于解密实际消息。
良好隐私 (PGP ) 虽已式微,仍是同时使用对称加密与公钥加密(非对称)的典型案例。使用 PGP 等端到端加密工具必须手动操作多个步骤,让您深刻体会公钥密码学的实际操作。现代通信工具隐藏了 PGP 的大部分操作,但正因其高度手动化,PGP 仍有助于理解端到端加密原理。
密钥的本质与关联机制
公钥密码学的前提基于两把密钥:加密公钥与解密私钥。公钥可经非安全渠道(如互联网)分发,即使公开张贴也不会危及加密消息的安全性。
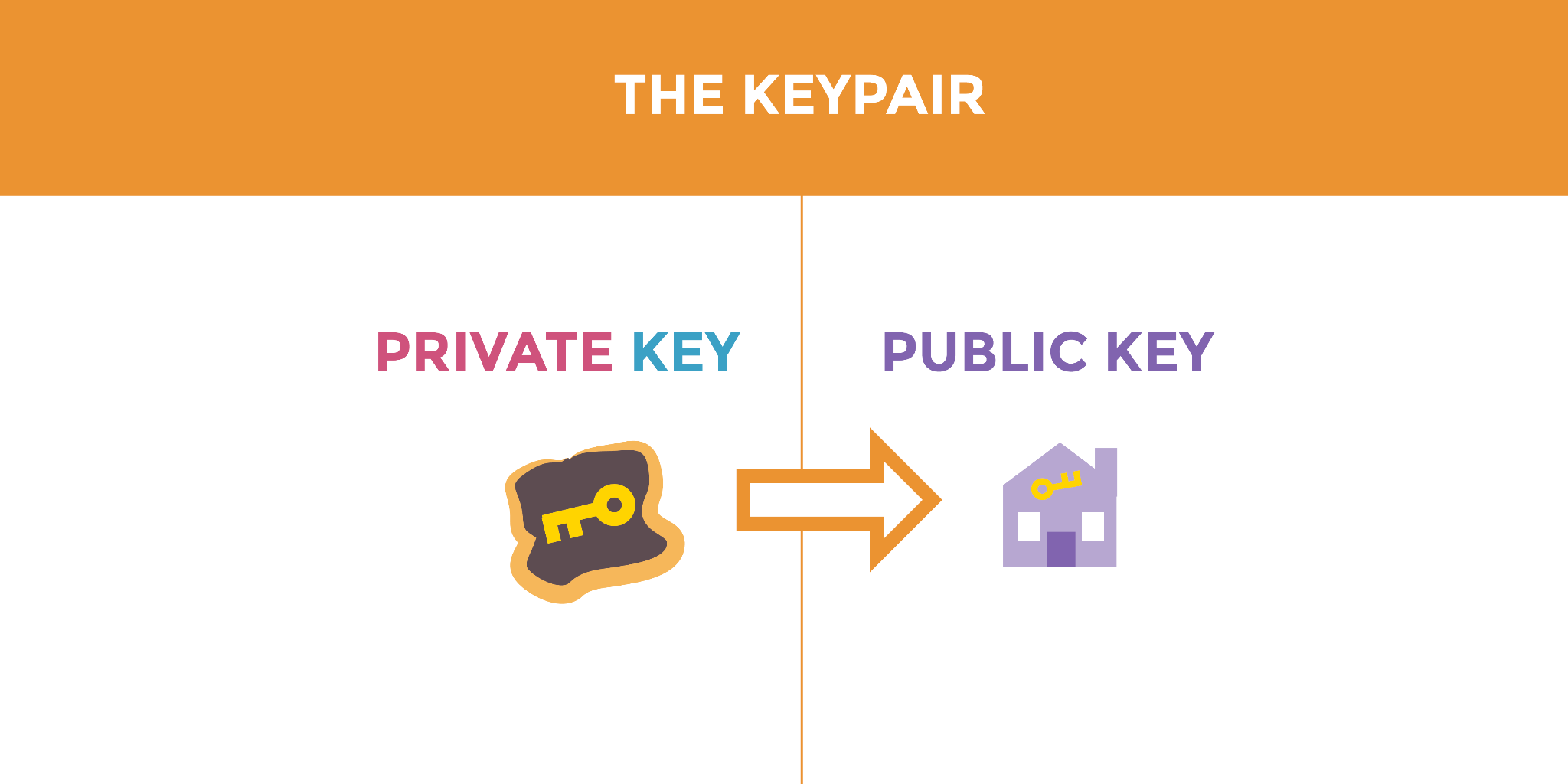
公钥始终与名为私钥的文件配对。但私钥如同实体钥匙,需严格保护。私钥既用于加密也用于解密消息。
让我们看看这在广泛使用的公钥加密算法 RSA (Rivest–Shamir–Adleman) 中是如何运作的。RSA 常用于生成 PGP 加密邮件的密钥对。
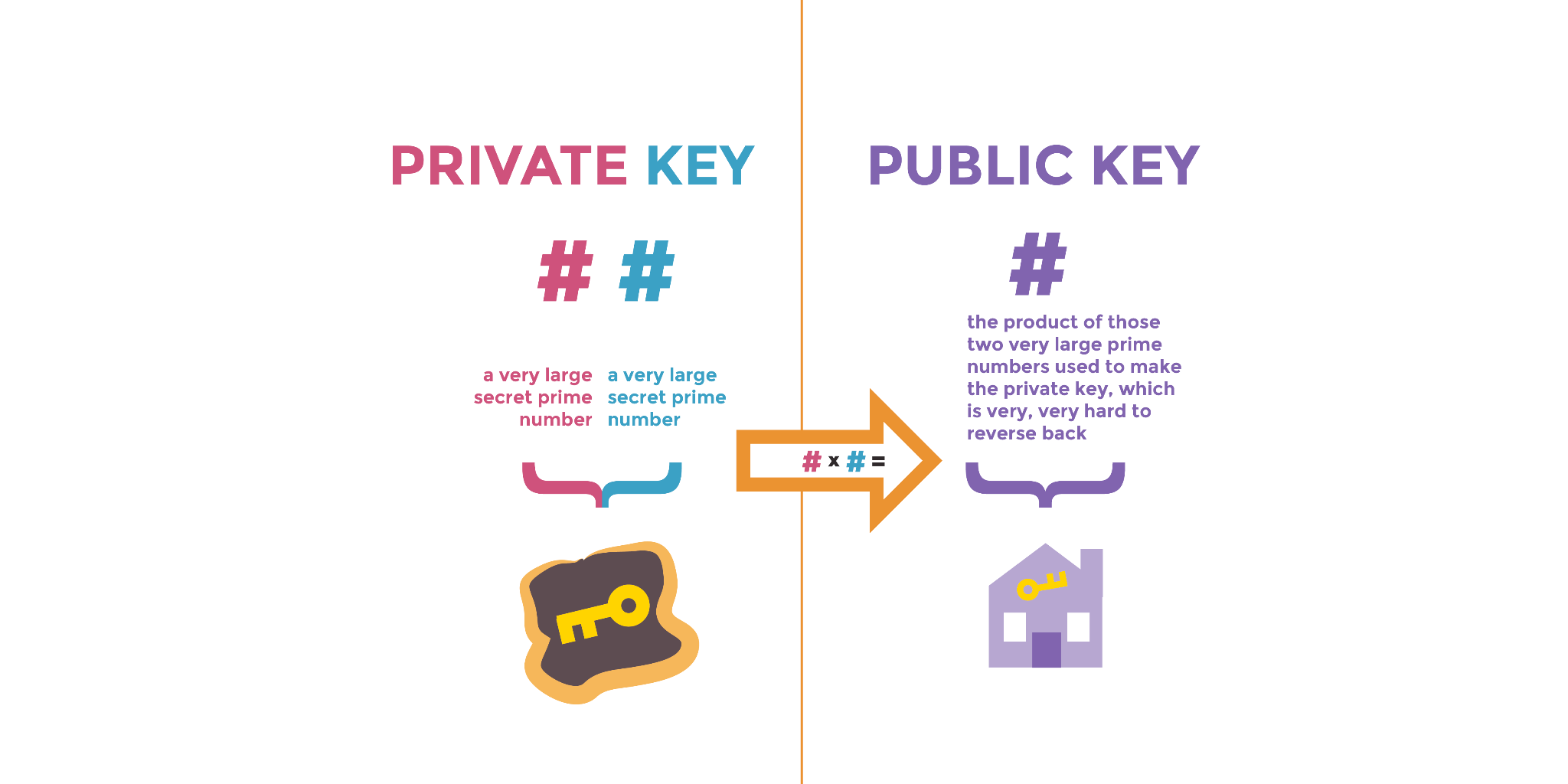
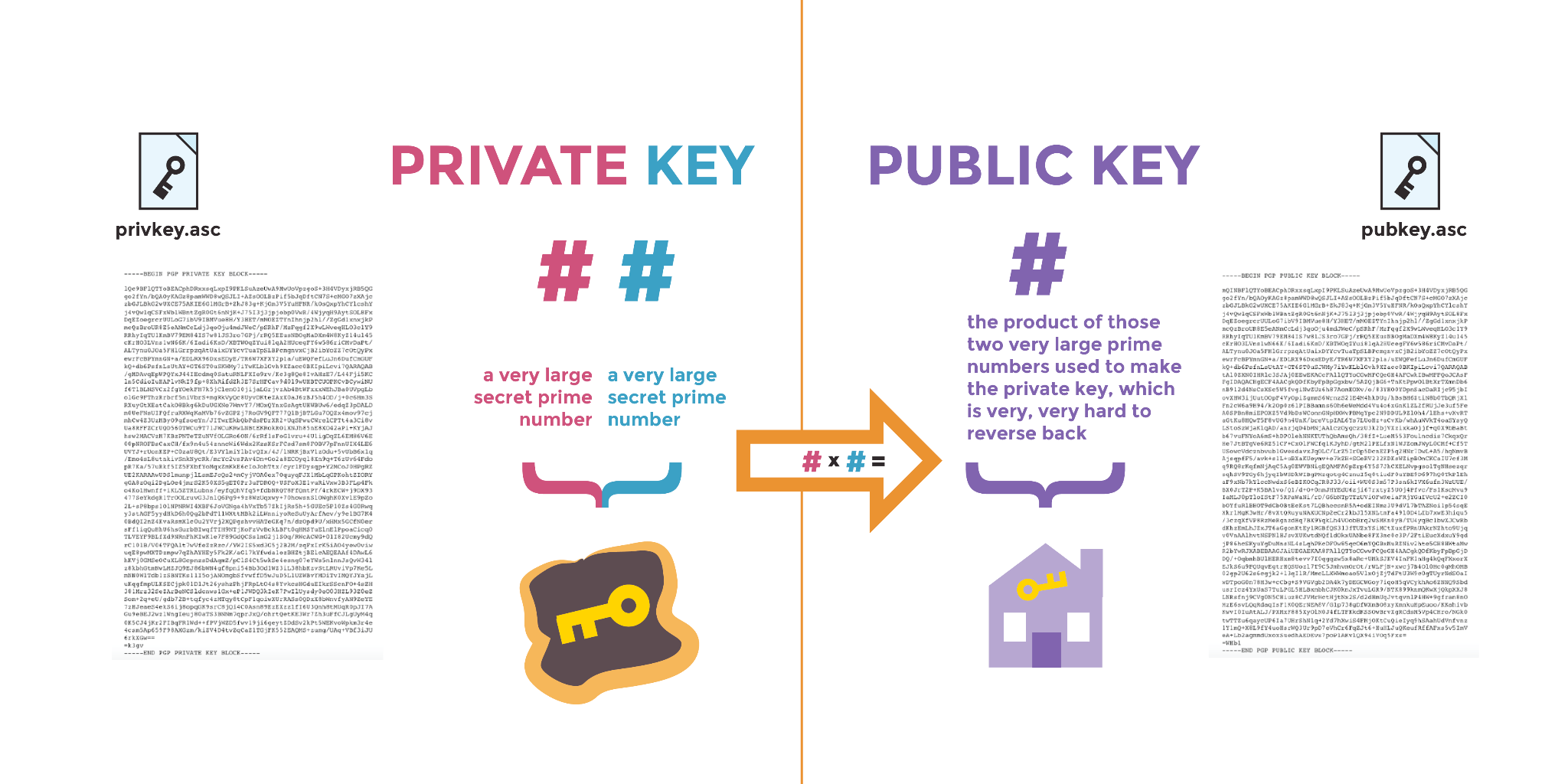
公钥和私钥基于相同秘密素数生成并相互绑定。私钥包含两个秘密素数。
打个比方,公钥如同乘积数:由用于生成私钥的两个超大素数相乘而得。而逆向推导这两个原始素数极其困难。
此问题称为“素数分解”。公钥密码学利用了计算机难以分解大素数的特性。现代密码学使用随机生成的超大素数,使人类与计算机均难以猜测。
其优势在于,用户可通过非安全渠道交换公钥以实现加密通信。在此过程中,他们绝不会泄露私钥(秘密素数),因为解密消息根本不需要发送私钥。
使用公钥加密的必要条件是,收发双方需要知道对方的公钥。
换个方式来理解,公钥和私钥如同阴阳符号,成对生成且密不可分。

公钥可搜索、可分享,可分发给任何人。也可发布于社交媒体(若不介意暴露邮箱)、个人网站等。
私钥则需严密保管。私钥只有一个,丢失、分享或复制都将危及隐私。
现代公钥加密实践:Signal 双棘轮算法
多年来,消息协议不断演进以提升安全性与易用性。这也使加密体验从透明但笨拙的操作,发展为无缝运行的后台进程,我们甚至无从察觉。典型示例为 Signal 的“双棘轮算法”。为了更好地理解此技术,我们需先回顾一下早期协议。
良好隐私 (PGP)
如前所述,PGP 在消息场景中结合非对称与对称加密,通常用于邮件加密。其非对称加密用于保护对称密钥,而后者则用于加密消息。PGP 支持异步通信,但一次密钥泄露就会让所有历史与未来消息全部暴露。因此,如果有人截获了您的密钥,他们就能访问您曾经和即将发送的所有消息。
PGP 曾经的繁荣已不复存在,但一些消息应用仍采用类似的加密技术。因而,这些应用仍存在与电邮版本同样的“入侵恢复”和“入侵存档保密性”问题。
离线记录 (OTR)
OTR 曾是早期聊天客户端(如 Pidgin)普遍使用的插件,用于 Google Hangouts 等平台。其局限性在于,必须双方在线才能建立会话。
在 OTR 中,每条往来消息均构成独立的一次“会话”。这意味着,密钥泄露仅影响当前会话的消息,其他消息则不受影响。如果某用户连续发送多条消息,则密钥泄露将暴露所有这些消息,但其他消息不受影响。密钥随消息而交换,因此新密钥会不断重新生成。
从安全的角度来看,此举非常有效,因为即使攻击者获取了密钥,也只能读取单条消息。但 OTR 的易用性较差。该技术要求双方同时在线,即便经过设置也不适合异步通信,因为新密钥仅在双方都发送消息后才会切换。这意味着,在对方响应之前,密钥材料需一直保留。此外,消息乱序跟踪(即,根据收发时间线性排列消息的功能)变得愈加复杂。消息的顺序不仅影响对话的可读性,还会影响加密的实际运作。如果消息乱序发送,接收方的应用可能无法确定使用哪个密钥解密消息。
静默圈即时消息协议 (SCIMP)
SCIMP 是一种过渡协议,率先采用了“双棘轮”机制。双棘轮是指每个发送方都拥有自己的密钥链,每个密钥都基于前一个密钥生成。这意味着消息发送后,即可安全弃置密钥材料。
想象一下棘轮:每转动一次,就会为每条消息生成一个新密钥。即便攻击者截获了该密钥,他们也无法读取之前的任何消息,因为消息发送后棘轮会再次转动,生成新密钥。但他们可能利用该密钥复制棘轮,从而读取所有未来的消息。对话双方各拥有一个棘轮,随着消息的发送而不断转动。这一设计旨在防止攻击者回溯对话以读取历史消息,即使用户连续发送多条消息也无妨。
SCIMP 提供“前向保密性”,即密钥泄露也不会暴露历史消息(尽管名为“向前”,但此技术可确保即使未来密钥泄露,历史消息也不会暴露)。但 SCIMP 不具备“未来保密性”或“入侵恢复”机制(用于防止密钥泄露后发送的消息被读取)。此外,由于需处理乱序消息,密钥材料需保留一段时间。
Signal 的双棘轮算法
Signal 结合了 OTR 与 SCIMP,支持异步通信。Signal 在其博客中解释了设计理念:“我们希望设计一种棘轮,结合 SCIMP 哈希迭代棘轮的最佳前向保密性与 OTR DH 棘轮的出色未来保密性,同时尽可能减少两者的缺陷。”
在 Signal 中,每位用户都拥有自己的 SCIMP 式棘轮,可在发送新消息(但对方未响应)时转动。不过对话双方每次消息交互时,系统就会创建一个新会话(如 OTR)。
通过整合这两种技术,攻击者要想窃听就必须逐条解密消息。在技术上,如果用户 A 连续发送多条消息而用户 B 未响应,且密钥遭到泄露,攻击者将能读取用户 A 发送的所有新消息,直至系统在用户 B 响应后升级会话。
Signal 的双棘轮算法借鉴了 SCIMP 密钥链的理念(即使某用户“连续发送消息”也能保护每条消息),并将其作为 OTR 棘轮每一步的微型链。这样可确保每次新用户响应时对话都会生成新密钥。此外,通过引入第三个“根密钥链”而减少了交互步骤。
Signal 的一大创新是支持通过离线密钥交换启动异步通信。由于设置下一条消息加密密钥仅需两步(而非三步),其中一步可提前准备并存储在 Signal 服务器上。相关密钥仅在有人使用该材料执行计算并获取共享密钥信息时生成,因此可安全预发布。Signal 称其为“预密钥”。如需查看更详细的版本,请参见此处;后量子版本参见此处。
元数据:公钥加密的盲区
公钥加密的核心是确保消息内容保密、真实且未经篡改。但这并非唯一的隐私问题。如前所述,消息的元数据可能与其内容同样敏感。
如果您与本国知名的异见人士交换加密消息,即使消息未解密,您也可能因与其通信而面临危险。在某些国家/地区,拒绝解密加密消息甚至可能导致监禁。每种加密消息工具收集的元数据量各不相同。例如,WhatsApp 虽支持端到端加密,但收集的元数据多于 Signal。
现在您已了解公钥密码学,不妨尝试使用 Signal 等端到端加密工具,进行亲身体验。

