Mobile Phones: Spying on Mobile Communications
Spying on Mobile Communications
Mobile phone networks were not originally designed to use technical means to protect subscribers' calls against eavesdropping. That meant that anybody with the right kind of radio receiver could listen in on the calls.
The situation is somewhat better today with encryption technology. But many of these technologies have been poorly designed (sometimes deliberately, due to government pressure not to use strong encryption). They have been unevenly deployed, so they might be available on one carrier but not another, or in one country but not another, and have sometimes been implemented incorrectly. For example, in some countries carriers do not enable encryption at all, or they use obsolete technical standards. This means it is often still possible for someone with the right kind of radio receiver to intercept calls and text messages as they're transmitted over the air. Law enforcement can also intercept your real-time communications with the aid of providers after obtaining special wiretapping warrants, or obtain your stored communications from a provider with a warrant.
The safest practice is to assume that traditional calls and SMS text messages have not been secured against eavesdropping or recording. Even though the technical details vary significantly from place to place and system to system, the technical protections are often weak and can be bypassed in many situations.
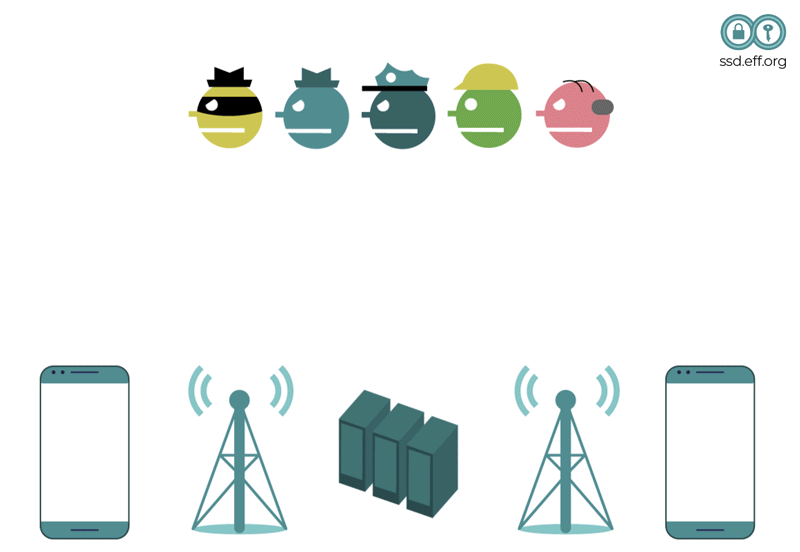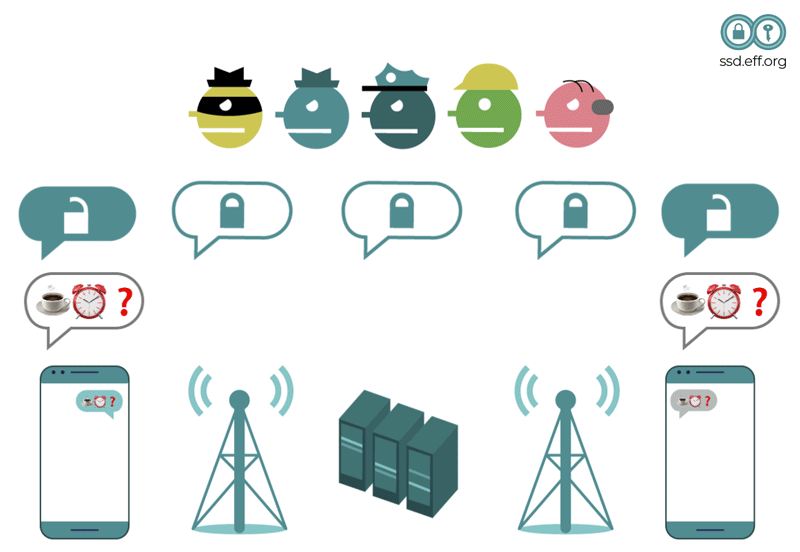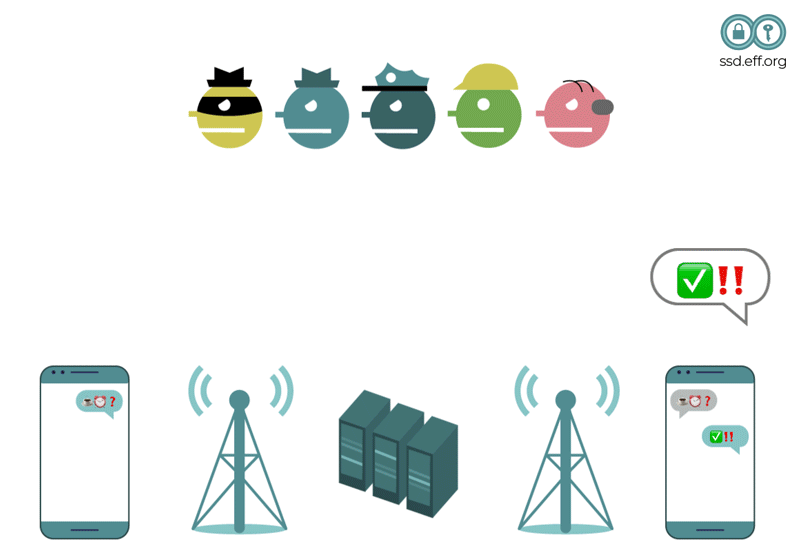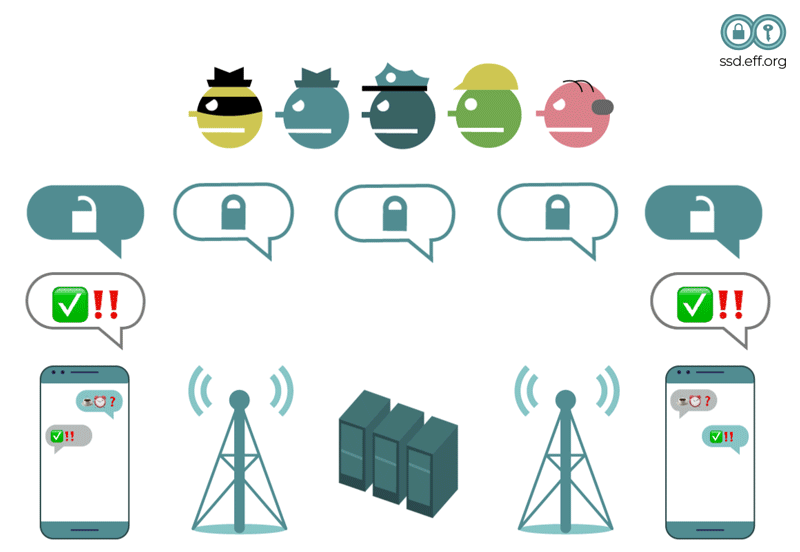
What you can do: There is a solution here, though: end-to-end encryption . This type of encryption wraps the content of your conversation in complex math so only you and the person you’re communicating with can read the messages. It’s good to use apps that support end-to-end encryption as often as possible. Some options include Signal, WhatsApp, and Apple’s iMessage (but these conversations are only end-to-end encrypted when you’re chatting with other Apple users, signaled by the conversation bubbles being blue instead of green).