How to: Get to Know Android Privacy and Security Settings
Open up your Android phone’s Settings app and you’ll find dozens of different options with little guidance on what those options do. Some of these settings have a serious impact on your privacy and security, altering what data gets shared automatically with apps, data brokers, and Google itself.
What sorts of changes you should make depends on how you use your phone and your security plan. There is no one-size-fits-all collection of recommended settings to change. Instead, we’ll explain what settings do to help you decide if they’re worth altering. This guide cannot cover everything, so for a deeper dive, check out our Privacy Breakdown of Mobile Phones guide.
How to use this guide: because of the sheer amount of privacy and security choices in Android, we’ve broken this into three sections, starting with the settings everyone should consider changing, and moving deeper from there. This guide is written for and is accurate as of Android 16.
Note: There are many different versions of Android and the instructions may differ depending on which company made your phone and which version of the operating system it runs. The instructions here are for the newest version of Android Google provides manufacturers and includes in its Pixel phones.
- Enable Two-Factor Authentication on Your Google Account
- Lock Your Phone Behind a Strong Passcode or Biometrics
- Audit Your Privacy Permissions
- Disable Ad Tracking
- Set Up "Find My Device" and "Theft Protection" features
- Run Through Google's "Privacy Checkup"
Level 2: Additional Steps for Some Security Plans
- Disable the ability to connect to WEP Networks
- Obscure Lockscreen Notifications
- Install a Custom Distibution
Level 1: Everyday Essentials
No matter what your specific security plan is, everyone should take a look at these settings on their phone to increase their privacy and security.
Enable Two-Factor Authentication on Your Google Account
Why
If you’ve owned an Android phone for a long time, there’s a chance you’ve already enabled two-factor authentication—a way to make your online accounts more secure by requiring additional proof it’s actually you (“factors”), alongside your password , to log in. This means that even if someone has access to your password, they wouldn’t be able to get into your Google account without this second factor. Your Google account can hold loads of sensitive data, including photos, contacts, notes, and just about anything else you’ve saved to your Google account. So it’s crucial to secure it as best as possible.
Once enabled, any time you want to log into your Google account from a new device or log into your account from a new web browser , you’ll need to enter a verification code or confirm your login on a “trusted device” (this might be your phone or laptop if you’ve logged into your Google account there). If this sounds tedious, don’t worry too much. After running through the authentication process one time, you won’t be asked to enter the verification code again unless you sign out of a device completely or erase the device and start over.
What to do
Google pushed for two-factor authentication requirements on all accounts, but it’s still possible to set up a new account without this enabled. If you’re not sure if you’ve turned it on, it’s worth checking to make sure. You can do this from any device you’re logged into your Google account on, but here’s how to check on Android:
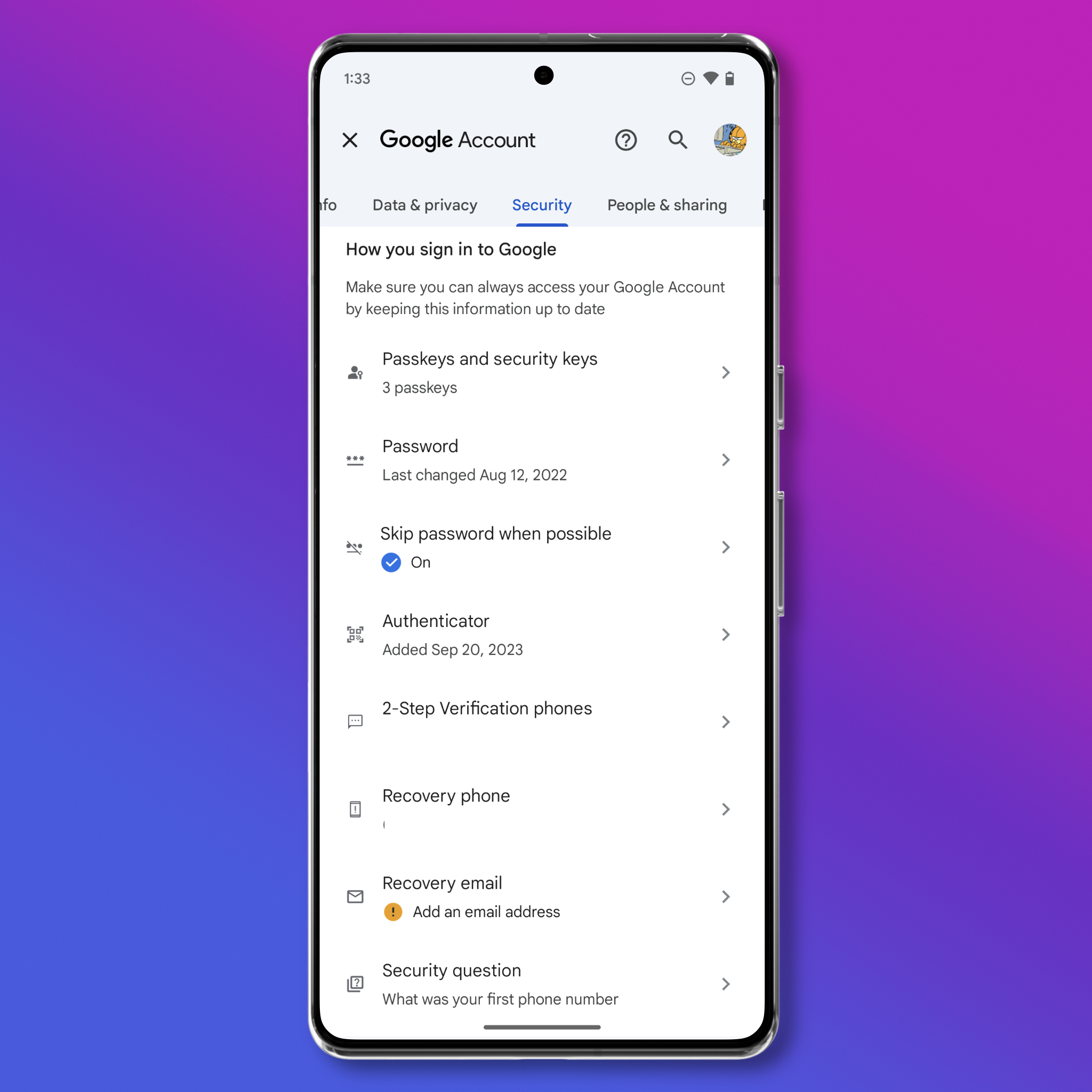
- Open Settings (you may need to then scroll down in the Settings menu and tap “Google Account” on some versions of Android) and then tap your profile picture, and tap “Manage Your Google Account.”
- On the top scroll over to Security, on the right. Select it and scroll down to “Authenticator” or “2-Step Verification phones” to enable two-factor authentication with either an app (preferred) or your phone number.
- From this menu you can also set up a passkey for your Google account. Instead of requiring you to enter your password and a code, passkeys include a second factor from your device. Each time you use the passkey to log in, your browser or operating system may ask you to re-enter your device unlock PIN. To create a passkey, tap “Passkeys and security keys,” then “Create a Passkey,” and follow Google’s directions.
If you’re at a high risk of targeted attacks, consider using a security key to lock down your Google account even stronger. Security keys are phishing resistant, but carry the risk of locking you out of your account forever if you lose the key. To set up a security key, follow these instructions.
There is yet another way to further protect your Google account with the company’s Advanced Account Protection Program. Google recommends this for at risk accounts, such as activists, journalists, and political campaigns. Once enabled, Advanced Account Protection adds new security features, such as blocking more harmful file downloads in Chrome, restricting which apps can access your personal information, and better protecting you from phishing. In order to turn this feature on, you must use either a passkey or a physical security key. You can also enable this on your phone.
Lock Your Phone Behind a Strong Passcode or Biometrics

Why
If your device is lost, stolen, or confiscated by police, “device encryption ” helps protect the data stored on your device. Modern Android phones have device encryption capabilities built into them.
What to do
You should protect your Android phone with a strong password: 8-12 random characters that are easy to remember and type in when you unlock your device. If devices are not protected by a strong password, the encryption may be easier to break using a brute-force attack. To enable or change your passcode:
- Open Settings > Security & privacy > Device unlock > Screen lock and select the type or length of passcode you'd like to use.
Once a passcode is set, you can choose to enable biometric login, using either your face or fingerprint , depending on which type of login your phone supports. This is optional and speeds up the process of unlocking your phone, but doesn’t have the same legal footing that passcodes do. Only you can decide if it's a safe choice to enable biometric login for your device, but if you want to turn it on, here’s how to do so:
- Open Settings > Security & privacy > Device unlock > Fingerprint Unlock > Add fingerprint and follow the onscreen instructions to register your face or fingerprint.
In the United States, using a biometric—like your face scan or fingerprint—to unlock your phone may also compromise legal protections for the contents of your phone afforded to you under the Fifth Amendment privilege against compelled incrimination. Under current law at time of writing, using a memorized passcode generally provides a stronger legal footing to push back against a court order of compelled device unlocking/decryption. While EFF continues to fight to strengthen our legal protections against compelling people to decrypt their devices, there is currently less protection against compelled face and fingerprint unlocking than there is against compelled password disclosure.
Audit Your Privacy Permissions
Why
Just about every app you download asks to access some sort of information about you or your device. This includes everything from obvious uses, like a camera app asking to access your camera and photos, to less obvious ones, like a newspaper app asking to access your local network.
All these permissions can be hard to keep track of. For that reason, it’s good to go through and double-check app permissions now and again. Doing so can ensure you are not sharing any data you don’t need or intend to share.
Before auditing your privacy permissions, it’s a good idea to go through all your apps and delete any you don’t need. This makes the audit easier, and the fewer apps you have installed on your phone, the fewer chances there are for your data to end up in the wrong hands.
What to do
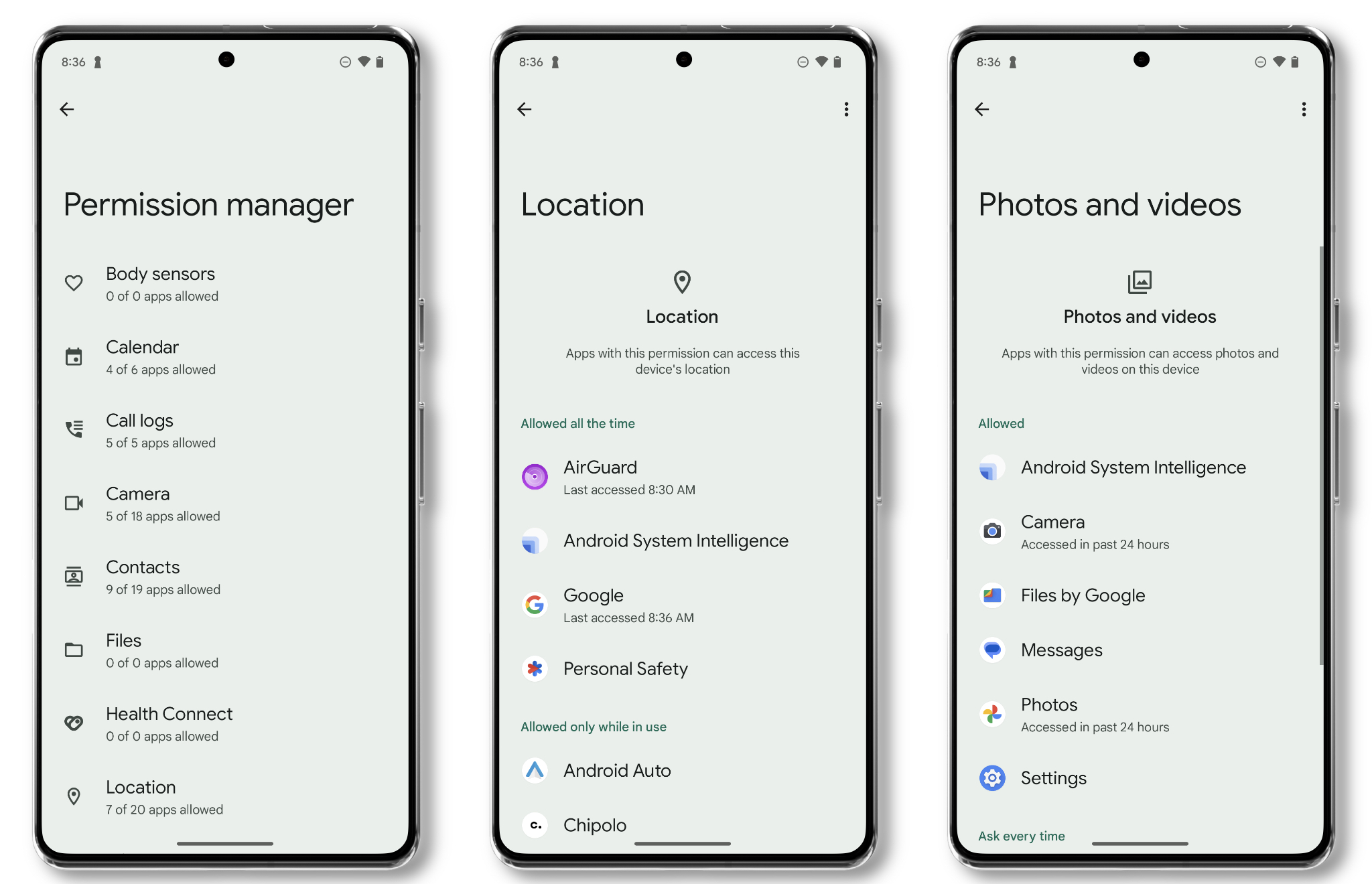
To get started, open Settings > Security & Privacy > Privacy Controls > Permission manager. Here, you’ll get to a page with an abundance of different permissions, each listing how many apps have access to that permission. Not all of these are only “on” or “off.” Some, like photos and location, offer more nuanced permissions. It’s worth going through each of these to make sure you still want that app to have that permission. If not, you can tap on the app in the permissions screen to revoke the permission. Don’t worry about breaking anything, you can always reverse the decision if an app loses functionality.
These permissions are broken into a few different sections, and there are a lot of them. It’s worth going through them all, but the most important permissions to focus on are:
Location Services
Location services are one of the most critical permissions that many apps ask for excessively. This permission gives apps access to your location (determined from GPS and Wi-Fi signals) so it knows where you’re at. Take a look through your apps listed here and ask yourself if they really need your location in order to function. If not, then it’s worth disabling location access completely or limiting it to only when you have the app open. Location services have a lot of variety for when an app can access your location:
- Don’t allow: the app will not get any location information from your Android device.
- Ask every time: Any time you open the app, it will ask for your location info.
- Allow only while using the app: The app can only access your location information when you have the app open. When you close the app, it’ll stop getting that information.
- Always: The app will receive your location information all the time.
You can change how exact the location information an app gets is, granting access to either your precise location, or a more generalized location. Disabling the precise location option means the app will only be able to access your general location. Precise location is necessary for mapping apps in particular, but may not be needed for many others.
Contacts
If an app needs access to your contacts, you can either grant it full access—which provides the app with your entire contact list, including all the information stored on their contact card—or not allow it to see your contact list at all.
Photos and videos
You can change a number of aspects around how apps access your photo roll:
- Always allow all: an app can access your entire photo roll.
- Allow limited access: you pick and choose specific photos an app gets access to.
- Don’t allow: the app can’t access your phone’s photo library at all.
Consider limiting access to your photo library in any app where you’d prefer some photos couldn’t get uploaded, even by accident. For example, if you use Slack at work, it may be best to limit access so you don’t accidentally upload your full set of vacation photos when you just intend to share one photo from the beach.
Camera
Here, you’ll find apps that have asked to access your camera. The most obvious use is third-party camera apps, but you may also see apps that use QR code scanning for two-factor authentication, notes apps, and more.
If an app has access to your camera and you do not understand why, disable it. You can always turn it back on if you need to.
Microphone
For the most part, you’ll find only apps you use for voice calls or video here. But if there’s an app that appears to be accessing your microphone and you can’t figure out why, disable it.
If you don’t open an app for a while, Android automatically resets your permissions to the default, so an app cannot access any extra data from your device at all.
Disable Ad Tracking
Why
The ad identifier—aka “AAID” on Android— enables most third-party tracking on mobile devices. Disabling it will make it substantially harder for advertisers and data brokers to track and profile you, and will limit the amount of your personal information up for sale.
What to do
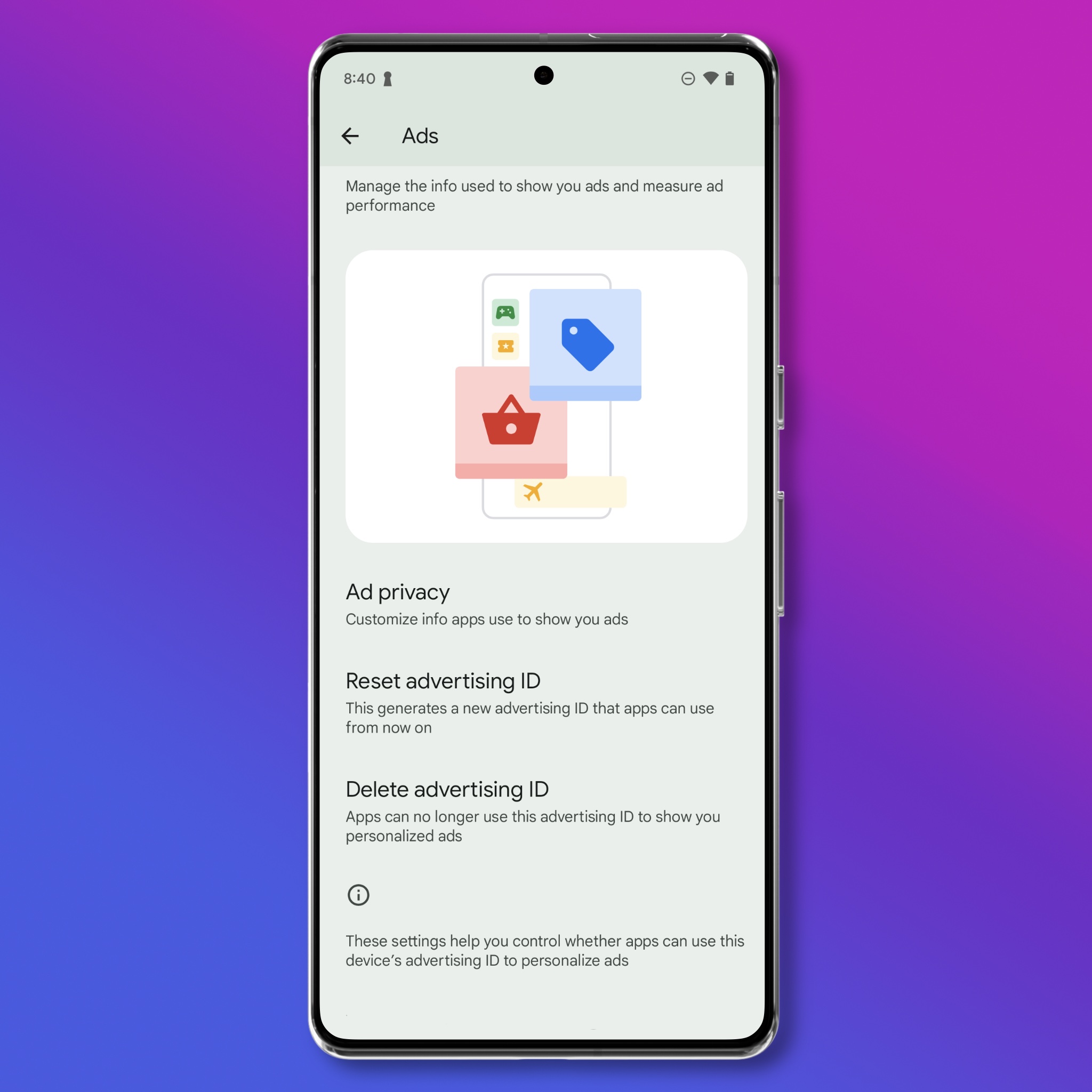
If preventing advertisers and data brokers from tracking you is important, you can disable the advertising ID entirely on an Android device:
- Open Settings > Security & privacy > Privacy controls > Ads, and tap “Delete advertising ID.”
Set Up “Find My Device” and "Theft Protection" Features
Why
Find My Device is best known as a tool that allows you to see the location of your Android if you lose it or if it’s stolen. This is helpful, but the security and privacy benefits of setting this up assume you won’t get your phone back. If you think your phone is long gone, you can remotely wipe it and delete everything on it.
Once enabled, if you lose a device or it’s stolen, you can find it on a map, or more importantly, remotely wipe its contents. You can find directions for doing so here.
By its nature, Find My Device uses location information to find your phone. To do this, it uses a combination of Wi-Fi, cellular, and other nearby Google devices with Bluetooth. Google claims this information is end-to-end encrypted and the location is “only visible to you and those you share your items with in Find My Device.” There is always some risk with using any sort of location-based tracking that the information will leak or be used in an unintended way.
What to do
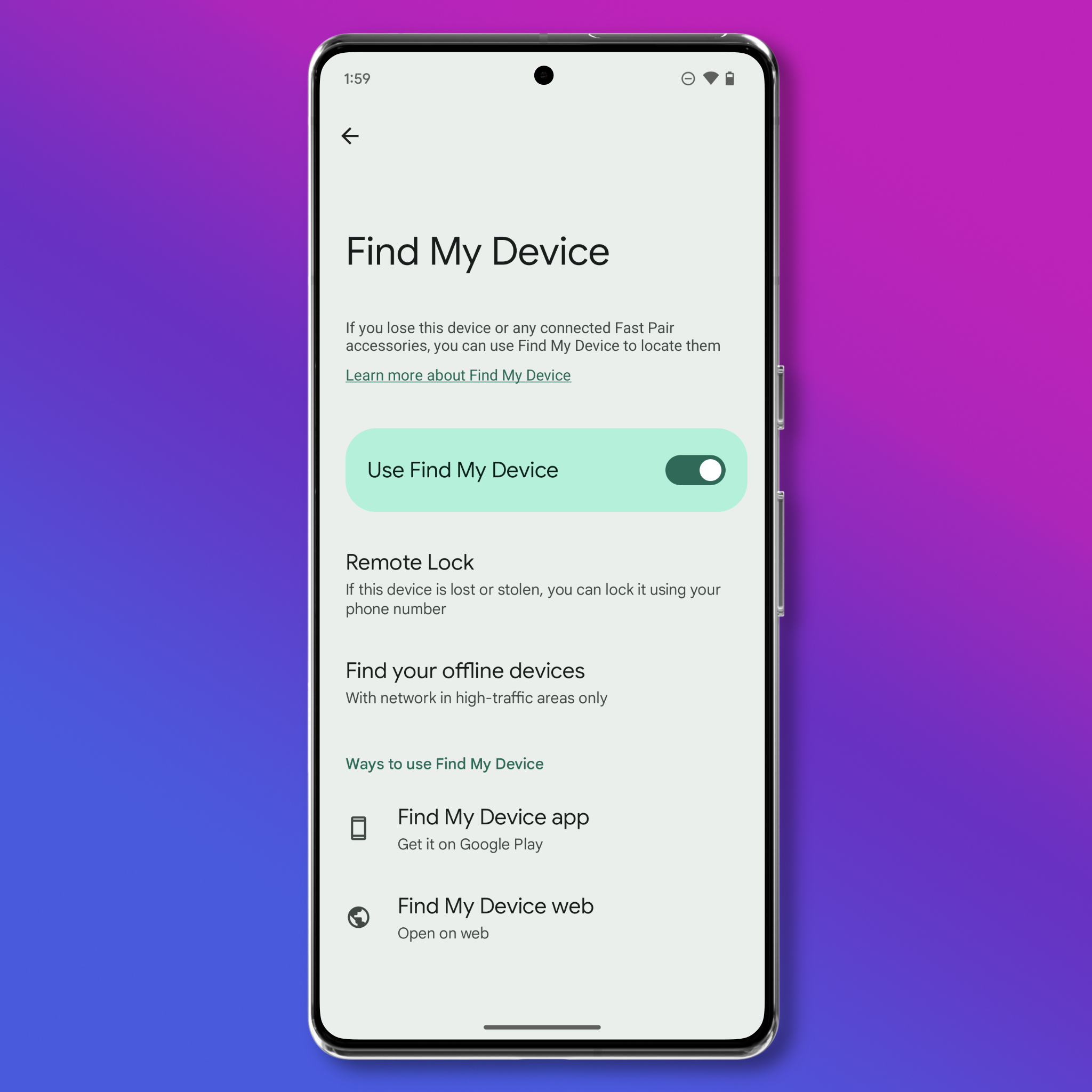
- Open Settings > Security & privacy > Device Finders > Find My Device, and enable “Use Find My Device.”
- On this screen, you can also optionally enable “Remote Lock.” This feature allows you to remotely lock your device using just your phone number. This is useful if your device is stolen or taken while unlocked.
- You may also consider enabling “Theft Protection.” This feature uses your device’s motion sensors, Wi-Fi, and Bluetooth to detect if someone takes your device and runs away. If a theft like this is detected, your screen will be locked. Open Settings > Security & privacy > Device Unlock > Theft Protection, and enable “Theft Detection Lock.” You can also enable “Offline Device Lock,” which can lock your screen if it’s stolen and the thief immediately turns off location services.
- On that same Settings page, consider setting up “Identity Check,” a feature that adds a biometric requirement to change certain critical settings, including running a factory reset and turning off Find My Device. This is meant to protect the data on your phone and your Google Account in a case where someone steals your phone and attempts to change critical settings to lock you out. This is only available on select Android devices, but if your phone supports it you will find the “Identity Check” setting under Settings > Security & privacy > Device Unlock > Theft Protection.
Run Through Google’s “Privacy Checkup”
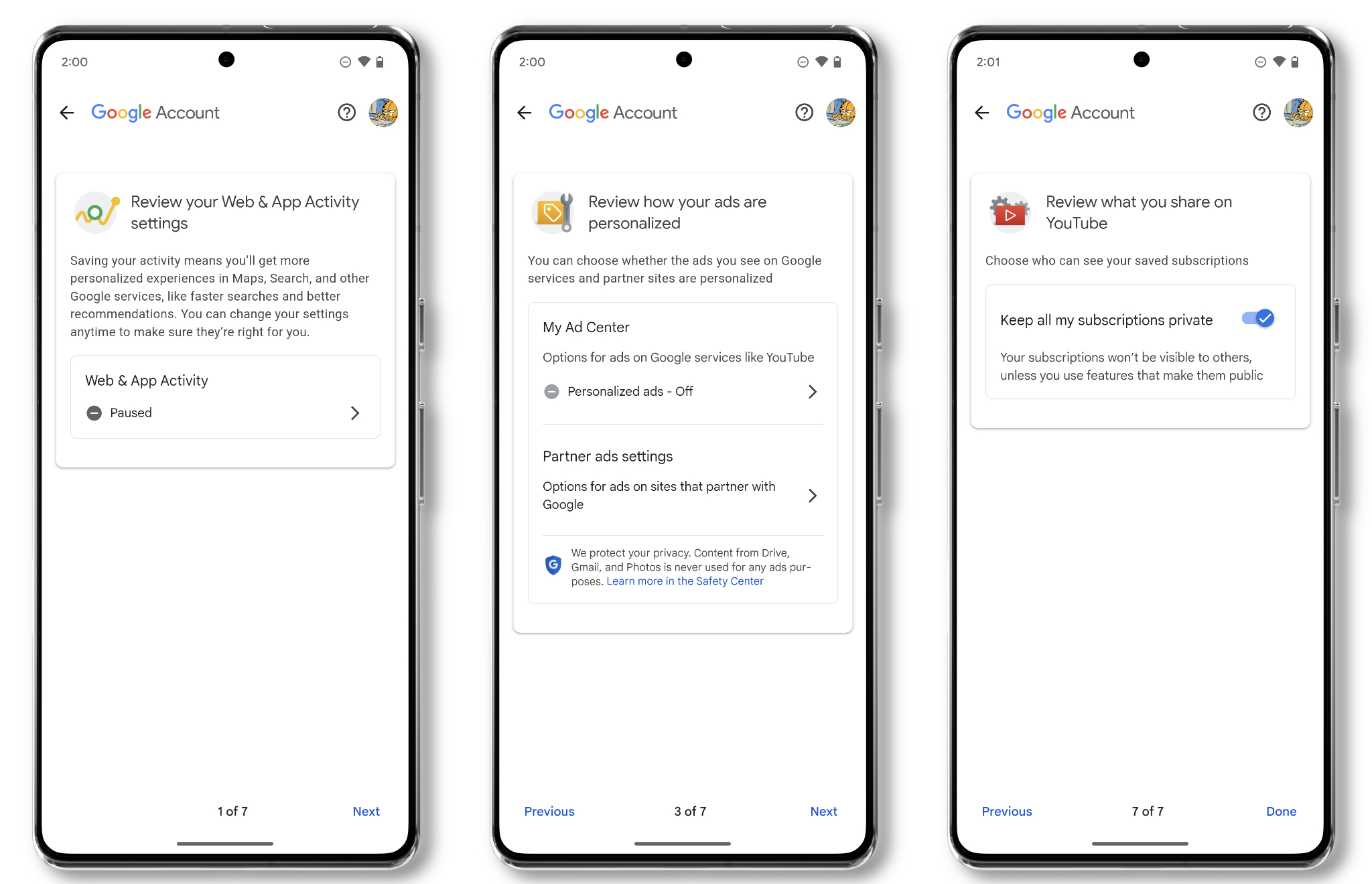
Why
You likely use your Google account across devices, like on a computer and your Android phone. Many of the most critical privacy settings are tucked away not on some specific page in your Android’s settings, but on your Google account itself. For this reason, it’s a good idea to run through the company’s “privacy checkup” to make sure you’re not inadvertently sharing information about your YouTube habits, location, or anything else.
What to do
- On your phone, open up Settings (you may need to then scroll down and tap “Google Account” on some versions of Android) and tap your profile icon. Tap the “Review your privacy settings,” option at the bottom of the page, or if that option isn’t available, tap “Manage Your Google Account,” then scroll down to “Privacy suggestions available.”
- In a browser, you can also go directly to the Privacy Checkup page so long as you’re logged into your Google account.
- Run through each page to make sure you are not saving or sharing data you do not mean to.
Level 2: Additional Steps for Some Security Plans
Decide How You Want to Handle Backups
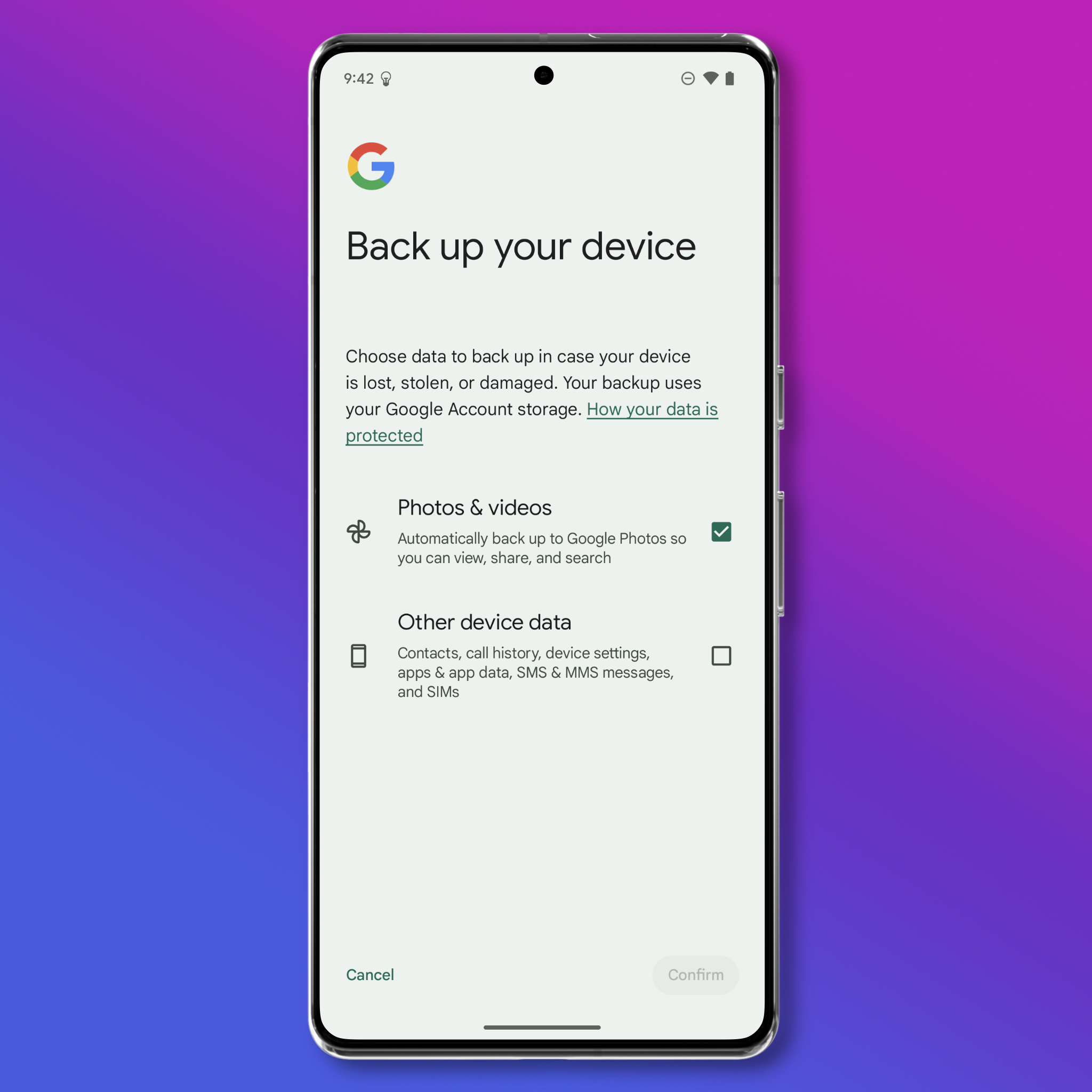
Why
Device backups are an important way to protect your data in case you lose your phone or it breaks. Backups are also useful in cases where you intentionally wipe your phone, like when you get a new phone, or if you’re going into a situation where you do not want to carry any personal data. With an up-to-date backup, you can restore your phone quickly without needing to go in and manually redownload all of your apps and data.
Every Google account includes 15 GB of free storage space, but the storage quota is shared across Google Drive, Google Photos, and Gmail. Depending on how many photos and videos you have, this may not be enough to store your backup and you may need to pay a monthly fee for additional space.
On Android, the backup process is divided into two options: photos and videos, and everything else. All photos and videos are stored in Google Photos, and are not end-to-end encrypted. This means the photos and videos do not use a type of backup storage that prevents Google (or anyone else with access to Google’s backup system) from seeing that content. You can also choose to back up everything else: device data, like contacts, call history, settings, app data, and messages. Some of this information, like app data, should be end-to-end encrypted if you use a device passcode, meaning Google can’t access it. However, it is not always clear what data is encrypted this way and what is not.
What to do
Android allows you to customize how backups are handled to some extent, but not by much.
- Open Settings > System > Backup.
- Here, you can choose to automatically back up just your photos and videos to Google, or everything else. Remember, some of this data is end-to-end encrypted with your device’s passcode, but not all of it.
If you prefer to back up your device locally to a personal computer, Windows users can use Google’s Quick Share software to do so wirelessly, or simply attach your phone to your computer with a USB cable and choose the “File Transfer” option when prompted on your phone. When the file transfer window opens up, drag any files you want to save over to your computer.
There is currently no easy and free way to manually back up to a Mac, but check Google’s official support documentation for updates.
If you are selling or giving away an Android phone, or if you want to wipe it temporarily for any reason, follow Google’s directions to complete a factory reset, which can be specific to each device manufacturer. To restore from the backup, just be sure to log into a phone with the same Google account you stored your backed up on and follow the on-screen directions to restore the backup.
Enable Advanced Protection
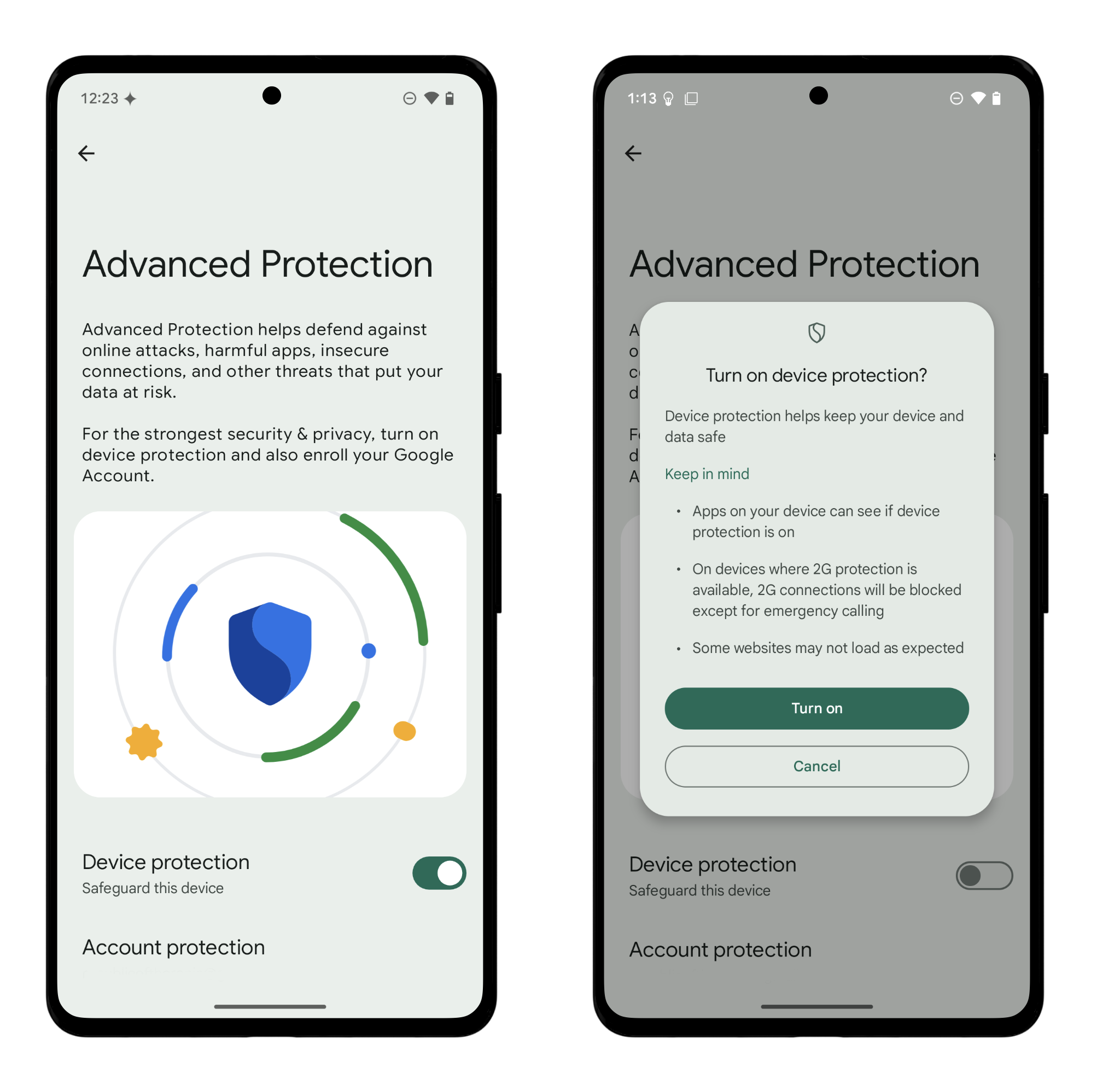
Why
Advanced Protection is an extension of Google’s Advanced Protection Program, which protects your Google account from phishing and harmful downloads. When enabled on Android, it’s meant to provide stronger security by: enabling certain features that aren’t on by default, disabling the ability to turn off features that are enabled by default, and adding new security features. Put together, this suite of features is designed to isolate data where possible, and reduce the chances of interacting with unsecure websites and unknown individuals.
For example, when it comes to enabling existing features, Advanced Protection configures several features mentioned already in this SSD guide, like Android’s “theft detection” features (designed to protect against in-person thefts) and disabling 2G (which helps prevent your phone from connecting to some Cell Site Simulators). It also forces Chrome to use HTTPS for all website connections and enables scam protection features in Google Messages. Advanced Protection also prevents you from disabling certain core security features that are enabled by default, like Google Play Protect (Android’s built-in malware protection) and Android Safe Browsing (which safeguards against malicious websites).
Advanced Protection adds some new features too. Once turned on, the “Inactivity reboot” feature restarts your device if it’s locked for 72 hours, which prevents ease of access that can occur when your device is on for a while and you have settings that could unlock your device. By forcing a reboot, it resets the data to being encrypted and behind biometric or PIN access. It also prevents your device from auto-reconnecting to unsecured Wi-Fi networks. Some additional features, like the ability to generate security logs and block USB connections when locked, are planned for future updates.
How
Advanced Protection is easy to turn on and off, so there’s no harm in giving it a try. Though, enabling Advanced Protection may impact how you use your device. For example, Advanced Protection disables the JavaScript optimizer in Chrome, which may break some websites, and since Advanced Protection blocks unknown apps, you won’t be able to side-load. There’s also the chance that some of the call screening and scam detection features may misfire and flag legitimate calls. The feature is currently available only for phones running Android 16, so if your phone doesn’t support Android 16, you won’t have the option to turn this on.
- Open the Settings app.
- Tap Security and Privacy > Advanced Protection, and enable the option next to “Device Protection.”
Set Up a Private Space
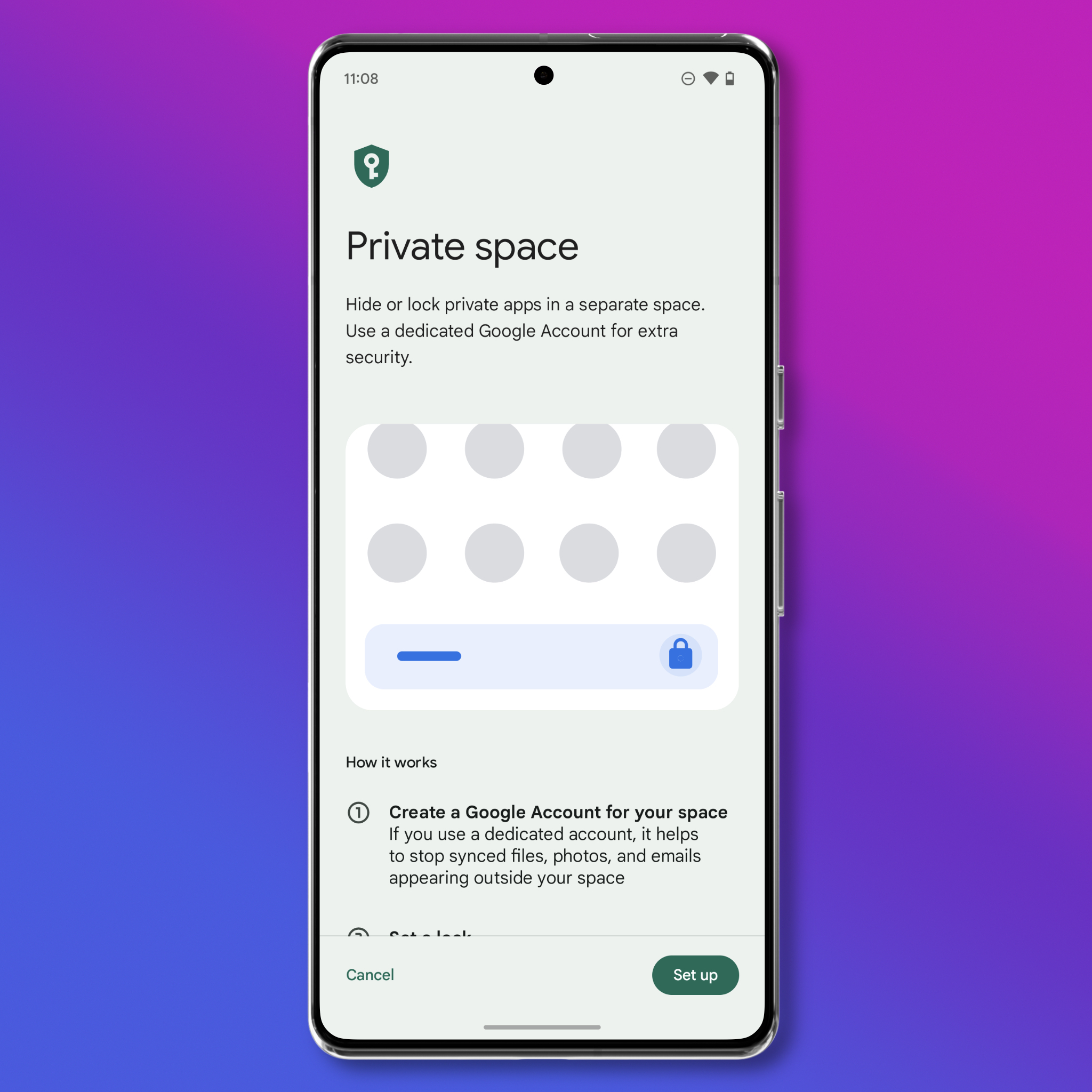
Why
If you want to hide sensitive apps, the “private space” feature is the simplest way to do so. Think of private space like an entirely different Android device that functions inside your primary one. Once set up, you get a secondary set of apps, which can optionally be tied to a completely different Google account. These apps have then all of their data isolated from the rest of your phone. This can be useful for information you want private, like encrypted communication apps or a photo library, or for apps you know aren’t private but you have to use occasionally, like a mapping app or ride share app.
Note: This is available on Android 15 and above for devices with at least 6GB of RAM. If you don’t see the following menu items, your device may not be supported.
What to do
- Open up Settings > Security & privacy > Private space and follow the directions to create a new space. You can choose to use a separate PIN or the one you use to unlock your phone.
- When prompted, optionally create a new Google account. This isn’t required, but setting up a new account means you don’t run the risk of accidentally syncing information to your primary account—like browsing history, photos, or whatever else you decide to use the private space for.
- Once setup is complete, the apps in your Private space are accessible at the bottom of your app drawer.
Read Google’s documentation for more information on all the nuances of what is and is not available in a private space.
If you share your phone with others often or have a second profile for work, multiple user profiles might be a better fit than a private space. To create a new profile, open up Settings > System > Multiple users, and enable “Allow multiple users.” Tap the button to either add a new user, with their own Google account, or a guest user, which doesn’t require an account. Each profile is encrypted with its own encryption key and a person using one profile cannot access any data from another profile without a password.
Disable 2G
Why
IMSI catchers—also known as Cell Site Simulators and Stingrays—are a tool that law enforcement and governments can use to track the location of phones, interept or disrupt communications, and gain new entry points into your phone to install malware. IMSI catchers can also be used to send spam and engage in fraud. IMSI catchers may try to trick your phone into connecting to a fake 2G cell tower. To prevent your phone from automatically connecting to one of these, you can disable 2G on your phone. Despite very little concrete evidence of cell site simulators being used against protesters in the U.S., we also think that the steps required to protect yourself are simple enough that this is a reasonable protective measure for most people to take and doesn’t really change how you’ll experience using your device:
What to do
- Depending on which version of the operating system you're running, the manufacturer of your phone, and your carrier, you may be able to disable 2G, require encrypted cell connections, or both. Open up Settings > Network & Internet > SIMs > [Your carrier name], find the "Allow 2G" option, and turn it off to disable 2G entirely.
- You may also see an option on the SIMs page to "Require Encryption." If you see this option, turn it on to prevent your phone from using a "null cipher" when connecting to a cell tower.
Level 3: Extra Credit
Not everyone has the same needs, and some changes in Android are easier than others. Here are a few more things to consider changing, depending on your needs:
Disable the ability to connect to WEP Networks
WEP is an older Wi-Fi network protocol with major security issues. It’s old enough that most people will not need to worry about running into networks that use it, but it still happens. This feature was added in Android 15 and is not available on older devices.
To ensure you can’t connect to one of these networks, open Settings > Network & internet > Internet, then scroll down to Network preferences and disable the option to “Allow WEP networks.”
Obscure Lockscreen Notifications
By default, the notifications you receive are visible on the lockscreen, meaning if you leave your phone out, someone could see any messages you receive and what apps you’re using without needing to unlock your device.
If you want to disable these previews, open Settings > Notifications > Notifications on lock screen, then disable the option for “Sensitive notifications.” What is and is not sensitive is defined by the app that’s sending the notification, and every app treats this differently, so this may not always work as you want. If you are very concerned with a notification revealing information, you may need to consider disabling notifications for that app entirely.
Install a Custom Distribution
Google’s mobile services are deeply integrated in most editions of Android. While the steps in this SSD guide can mitigate some of the most privacy-invasive issues with Google, you cannot remove that threat completely without using a different operating system entirely. Likewise, most phone manufacturers (including Google) use custom versions of Android that add in their own specific software or services.
It is possible to install other operating systems on many Android-based phones, though. A number of alternative Android distributions (often referred to as “custom ROMs” or “Android ROMs”) exist that may increase your privacy while using an Android device. This will fundamentally change the way your phone works and may make some apps you need not work at all.
Custom ROMs also introduce new risks, as these distributions are not vetted in the same ways and with the same amount of resources as Google puts into the core edition of Android. But most device-makers customize Android for their devices, and how those versions get vetted depends on the company that makes the phone. Because of this, we only recommend using custom ROMs if you have a deep understanding of these potential threats and take the time to develop your personal security plan to help you focus on what you’d be looking for in a custom ROM.
In some cases, a custom ROM can increase the privacy and security of your Android device, extend security updates if Google or your device-maker has stopped issuing them, or add special new features. If they’re designed to be private by default, they also require less tinkering of settings to ensure you’re using them as privately as possible. Popular custom ROMs that focus on security or privacy include:
EFF cannot vouch for any custom ROM. Take time to research recommendations and news stories to reveal any glaring issues they have, or that security researchers may find in the future. By their nature using a custom ROM may compromise many of the built-in security features in some versions of Android. Do not use a custom ROM that you do not trust.

