How to: Delete your Data Securely on Linux
Last Reviewed: July 20, 2018
We are in the process of updating several guides, including this one, and are aware that some of this information is out of date.
Download location: https://www.bleachbit.org/download/linux
Computer requirements: Any major Linux distribution. For reference Ubuntu 18.04 is used in this guide.
Versions used in this guide: BleachBit 2.0
License: GPLv3
Level: Beginner
Time required: 10 minutes to several hours (depending on size of files/disks to be securely deleted)
The instructions below should only be used for securely deleting data from spinning drives. These instructions apply only to traditional disk drives, and not to Solid State Drives (SSDs), which are standard in modern computers, USB keys/USB thumb drives, or SD cards/flash memory cards. Secure deletion on SSDs, USB flash drives, and SD cards is very hard! This is because these types of drives use a technique called wear leveling and do not provide low-level access to the bits as stored on the drive. (You can read more about why this causes problems for secure deletion here.) If you’re using an SSD or a USB flash drive, jump to this section below.
Did you know that when you move a file on your computer into your computer's trash folder and empty the trash, the file is not completely erased? Computers normally don't “delete” files; when you move a file to the trash, your computer just makes the file invisible and allows the space it took up to be overwritten by something else sometime in the future. Therefore, it may be weeks, months, or even years before that file is overwritten. Until this happens, that “deleted” file is still on your disk; it’s just invisible to normal operations. And with a little work and the right tools (such as “undelete” software or forensic methods), that “deleted” file can be retrieved.
So, what’s the best way to delete a file forever? Ensure it gets overwritten immediately. This makes it difficult to retrieve what used to be written there. Your operating system probably already has software that can do this for you—software that can overwrite all of the “empty” space on your disk with gibberish and thereby protect the confidentiality of deleted data.
On Linux, we currently suggest using BleachBit, an open-source secure deletion tool for Linux and Windows. It’s much more sophisticated than the built-in “shred.” BleachBit can be used to quickly and easily target individual files for secure deletion, or to implement periodic secure deletion policies. It is also possible to write custom file deletion instructions. You can find further information in the documentation.
Installing BleachBit
Installing with Ubuntu Software
You can get BleachBit on Ubuntu by using the Ubuntu Software application. If it’s in your favorite applications, you can click on it on the left-hand side of the screen.
Otherwise, click on the application button in the lower left-hand side of the screen and use the search field.
Type “software” in the search field and click the Ubuntu Software icon.

By default, BleachBit will not be listed. To ensure that it is listed, enable community-maintained packages by clicking “Ubuntu Software” in the top menu and then clicking “Software & Updates.”
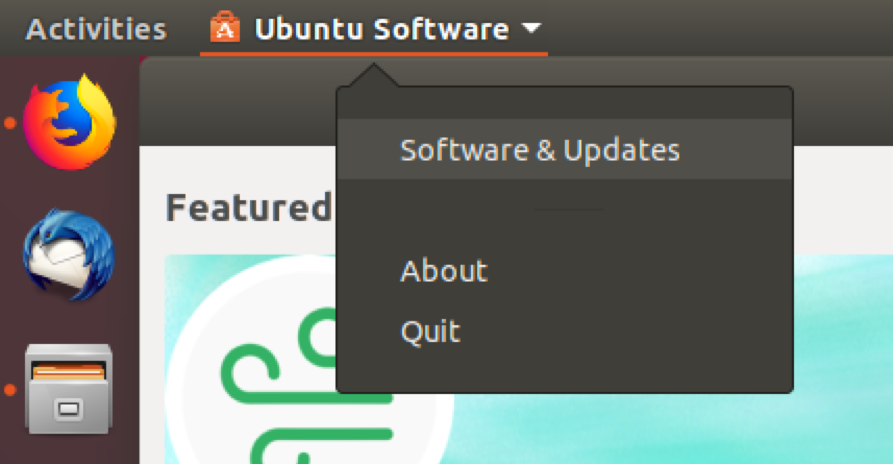
In the new window, make sure the box next to “Community-maintained free and open-source software (universe)” is checked, then click “Close” and “Reload.” If it is already checked, you may just click “Close.”
You can now browse through Ubuntu Software to look for BleachBit, but searching for it is faster. Use the search field by clicking the magnifying glass in the top-right corner of the window.
Then enter “BleachBit” in the search field.
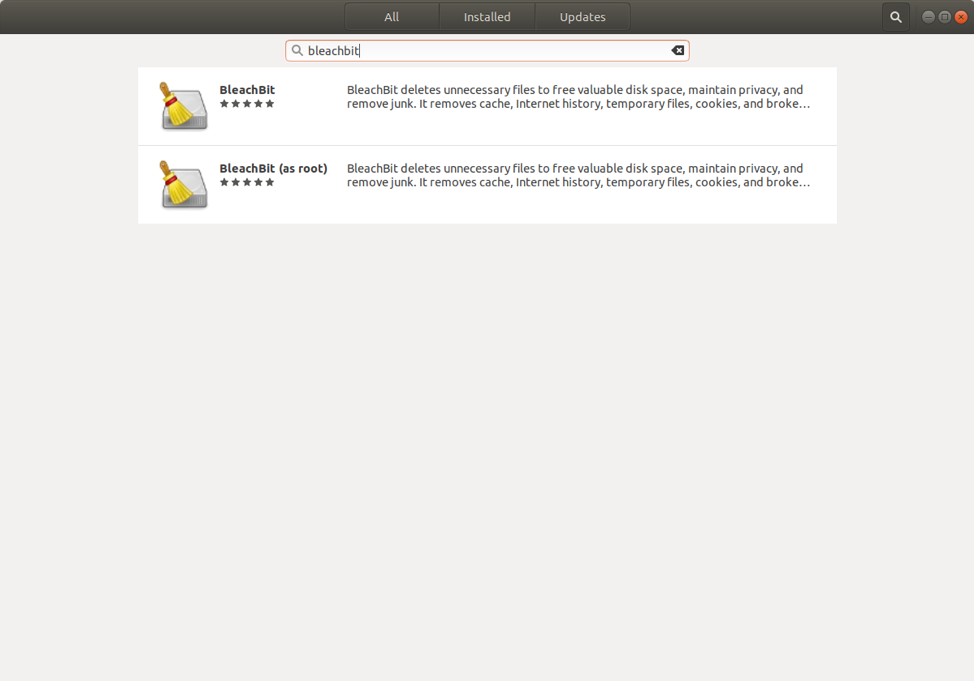
Click on BleachBit and click the Install button.
Ubuntu Software will ask for your password for permission. Enter your password and click the Authenticate button.
The Ubuntu Software Center will install BleachBit and show you a small progress bar. When the installation is done you will see a “Launch” and “Remove” button.
Installing From the Terminal
You can also get BleachBit on Ubuntu by using the Terminal. Click on the application button in the lower left-hand side of the screen and use the search field.
Type “terminal” in the search field and click the Terminal icon.
Type “sudo apt-get install bleachbit” and press Enter.
You’ll be asked to enter your password to verify that you want to install BleachBit. Enter your password and press Enter.
Now you'll see the progress of the installation of BleachBit and when it is done you should be back at the command line where you started.
Adding BleachBit to Sidebar
Click on the application button in the lower left-hand side of the screen and use the search field.
Type “bleach” in the search field and two options will appear: BleachBit and BleachBit (as root).
Only use the BleachBit (as root) option if you know what you are doing because it can cause irreparable harm if you use it to delete files needed by the operating system.
Right-click on BleachBit and select “Add to Favorites.”
Using BleachBit
Click on the BleachBit icon from your Favorites on the left side of the screen.

The main BleachBit window will open and BleachBit will give you an overview of the preferences. We recommend checking the “Overwrite contents of files to prevent recovery” option.
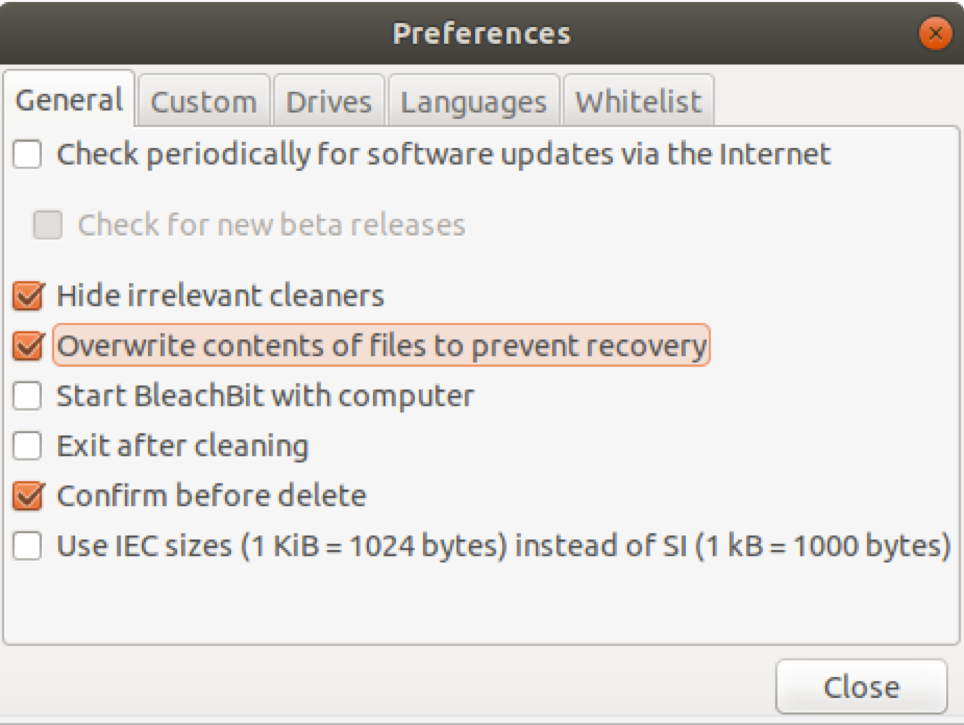
Click the “Close” button.
BleachBit will detect several commonly installed programs and will show special options for each program.
Using Presets
Some software leaves behind records of when and how it was used. Two important examples that merely begin to illustrate this widespread issue are Recent Documents and web browser history. Software that tracks the recently-edited documents leaves a record of the names of files you've been working with, even if those files themselves have been deleted. And web browsers usually keep detailed records of what sites you've visited recently, and even keep cached copies of pages and images from those sites to make them load faster next time you visit.
BleachBit provides “presets” that can remove some of these records for you, based on the BleachBit authors' research about locations of records on your computer that tend to reveal your previous activity. We'll describe using just two of these presets so you can get an idea of how they work.
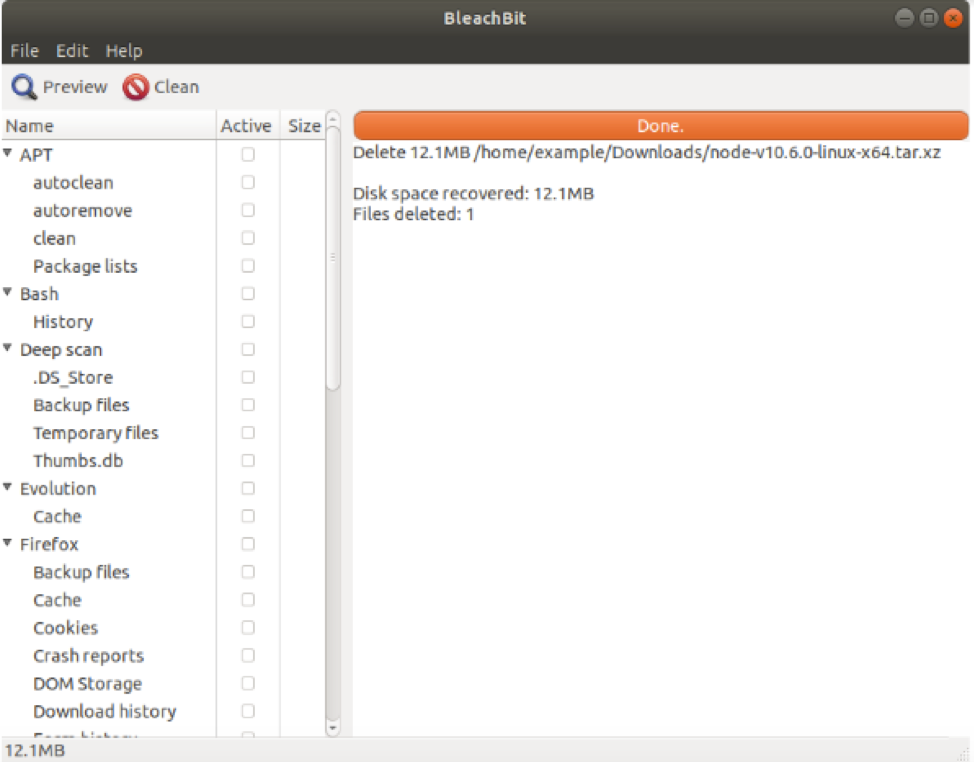
Check the box next to System. Notice that this marks all the checkboxes under the System category. Uncheck the System box and check the following boxes: Recent document list and Trash. Click the “Clean” button.
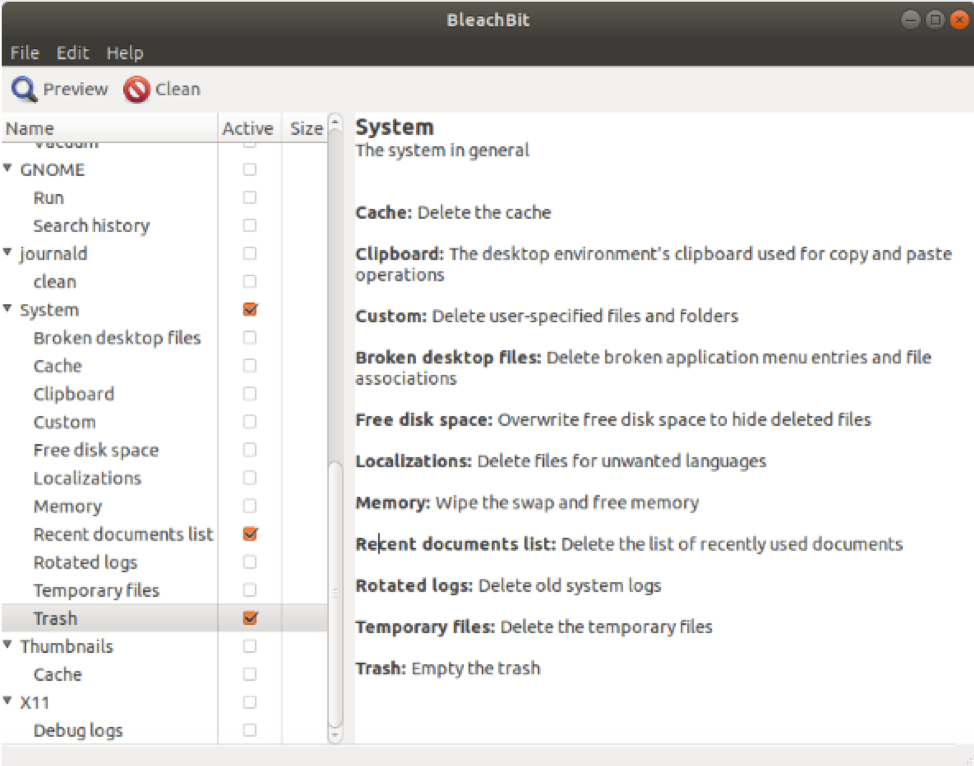
BleachBit will now ask you for confirmation. Click the Delete button.
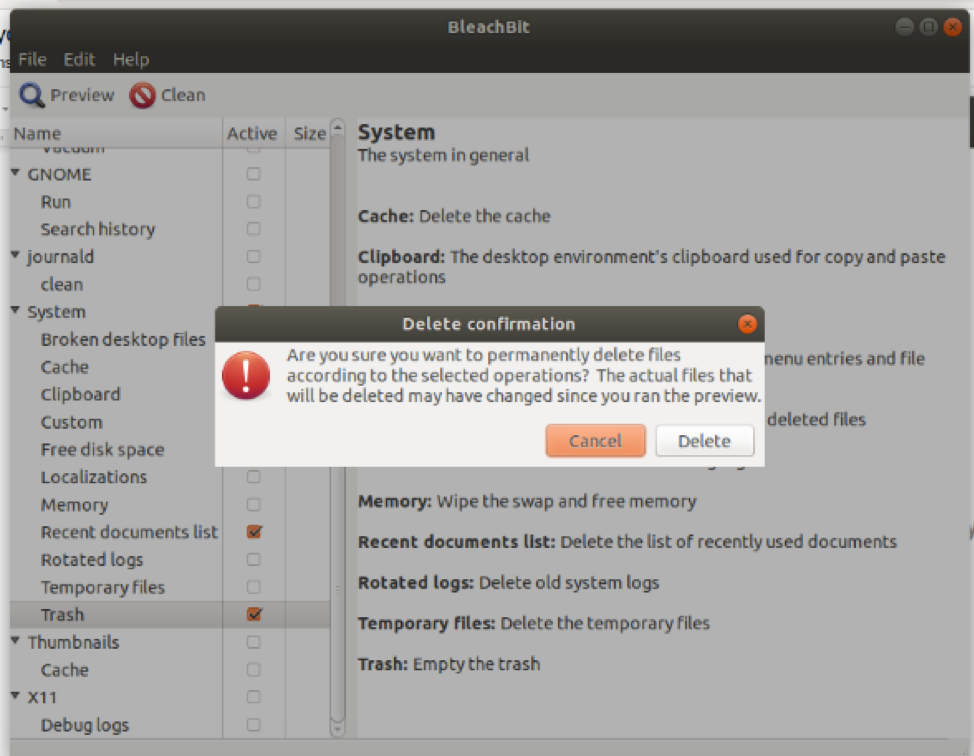
BleachBit will now clean up certain files and show you the progress.
How to Securely Delete a Folder
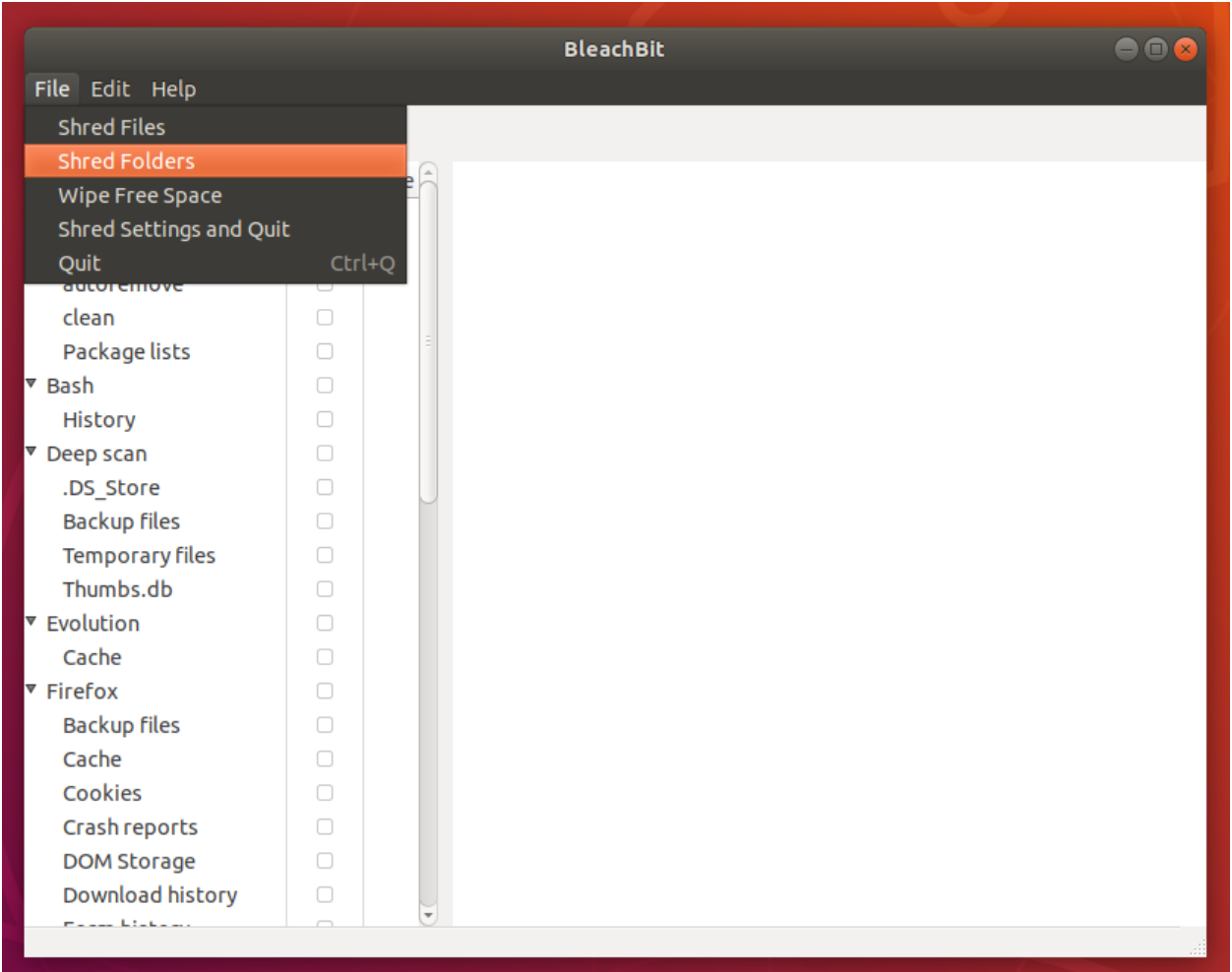
Click the “File” menu and select “Shred Folders.”
A small window will open. Select the folder you want to shred.
BleachBit will ask you to confirm whether you want to permanently delete the files you selected. Click the “Delete” button.
BleachBit will show you the files you deleted. Notice that BleachBit securely deletes each file in the folder, then securely deletes the folder.
How to Securely Delete a File
Click the File menu and select Shred Files.
A file selection window will open. Select the files you want to shred.

BleachBit will ask you to confirm whether you want to permanently delete the files you selected. Click the “Delete” button.

BleachBit has a number of other features. The most useful one may be wiping free space. This will attempt to remove any traces of files you have already deleted. Often Linux will leave all or part of the data from deleted files in the remaining free space left on the hard drive. Wiping free space will overwrite these supposedly empty parts of the hard drive with random data. Wiping free space can take a lot of time, depending on how much spare capacity your drive has.
A Warning About the Limitations of Secure Deletion Tools
Remember that the advice above only deletes files on the disk of the computer you’re using. None of the tools above will delete backups that were made to somewhere else on your computer, another disk or USB drive, a “Time Machine,” on an email server, in the cloud, or sent to your contacts. In order to securely delete a file, you must delete every copy of that file, everywhere it was stored or sent. Additionally, once a file is stored in the cloud (e.g. via Dropbox or some other file-sharing service) there’s usually no way to guarantee that it will be deleted forever.
Unfortunately, there’s also another limitation to secure deletion tools. Even if you follow the advice above and you’ve deleted all copies of a file, there is a chance that certain traces of deleted files may persist on your computer, not because the files themselves haven't been properly deleted, but because some part of the operating system or some other program keeps a deliberate record of them.
There are many ways in which this could occur, but two examples should suffice to convey the possibility. On Windows or macOS, Microsoft Office may retain a reference to the name of a file in the “Recent Documents” menu, even if the file has been deleted (Office might sometimes even keep temporary files containing the contents of the file). LibreOffice may keep as many records as Microsoft Office, and a user's shell history file may contain commands that include the file's name, even though the file has been securely deleted. In practice, there may be dozens of programs that behave like this.
It's hard to know how to respond to this problem. It is safe to assume that even if a file has been securely deleted, its name will probably continue to exist for some time on your computer. Overwriting the entire disk is the only way to be 100% sure the name is gone. Some of you may be wondering, “Could I search the raw data on the disk to see if there are any copies of the data anywhere?” The answer is yes and no. Searching the disk (e.g. by using a command like grep -ab /dev/ on Linux) will tell you if the data is present in plaintext, but it won't tell you if some program has compressed or otherwise coded references to it. Also, be careful that the search itself does not leave a record! The probability that the file's contents may persist is lower, but not impossible. Overwriting the entire disk and installing a fresh operating system is the only way to be 100% certain that records of a file have been erased.
Secure Deletion When Discarding Old Hardware
If you want to throw a piece of hardware away or sell it on eBay, you'll want to make sure no one can retrieve your data from it. Studies have repeatedly found that computer owners usually fail to do this―hard drives are often resold chock-full of highly sensitive information. So, before selling or recycling a computer, be sure to overwrite its storage media with gibberish first. And even if you're not getting rid of it right away, if you have a computer that has reached the end of its life and is no longer in use, it's also safer to wipe the hard drive before stashing the machine in a corner or a closet. Darik's Boot and Nuke is a tool designed for this purpose, and there are a variety of tutorials on how to use it across the web (including here).
Some full-disk encryption software has the ability to destroy the master key , rendering a hard drive's encrypted contents permanently incomprehensible. Since the key is a tiny amount of data and can be destroyed almost instantaneously, this represents a much faster alternative to overwriting with software like Darik's Boot and Nuke, which can be quite time-consuming for larger drives. However, this option is only feasible if the hard drive was always encrypted. If you weren't using full-disk encryption ahead of time, you'll need to overwrite the whole drive before getting rid of it.
Discarding CD- or DVD-ROMs
When it comes to CD- or DVD-ROMs, you should do the same thing you do with paper―shred them. There are inexpensive shredders that will chew them up. Never just toss a CD or DVD-ROM in the garbage unless you're absolutely sure there's nothing sensitive on it.
Secure Deletion on Solid-state Disks (SSDs), USB Flash Drives, and SD Cards
Unfortunately, due to the way SSDs, USB flash drives, and SD cards work, it is difficult, if not impossible, to securely delete both individual files and free space. As a result, your best bet in terms of protection is to use encryption. That way, even if the file is still on the disk, it will at least look like gibberish to anyone who gets ahold of it and can’t force you to decrypt it. At this point in time, we cannot provide a good general procedure that will definitely remove your data from an SSD. If you want to know why it’s so hard to delete data, read on.
As we mentioned above, SSDs and USB flash drives use a technique called wear leveling. At a high level, wear leveling works as follows. The space on every disk is divided into blocks, kind of like the pages in a book. When a file is written to disk, it’s assigned to a certain block or set of blocks (pages). If you wanted to overwrite the file, then all you would have to do is tell the disk to overwrite those blocks. But in SSDs and USB drives, erasing and re-writing the same block can wear it out. Each block can only be erased and rewritten a limited number of times before that block just won’t work anymore (the same way if you keep writing and erasing with a pencil and paper, eventually the paper might rip and be useless). To counteract this, SSDs and USB drives will try to make sure that the amount of times each block has been erased and rewritten is about the same, so that the drive will last as long as possible (thus the term wear leveling). As a side effect, sometimes instead of erasing and writing the block a file was originally stored on, the drive will instead leave that block alone, mark it as invalid, and just write the modified file to a different block. This is kind of like leaving the page in the book unchanged, writing the modified file on a different page, and then just updating the book’s table of contents to point to the new page. All of this occurs at a very low level in the electronics of the disk, so the operating system doesn’t even realize it’s happened. This means, however, that even if you try to overwrite a file, there’s no guarantee the drive will actually overwrite it, and that’s why secure deletion with SSDs is so much harder.