How to: Use Tor for Linux
Last Reviewed: July 10, 2023
We've updated this guide to a new page. Please see the new version here.
Computer requirements: An internet connection, a computer running your favorite Linux distribution.
Versions used in this guide: Ubuntu 20.04.4 LTS; Tor Browser: 12.5
License: Free Software ; mix of Free Software licenses
Level: Beginner-Intermediate
Time required: 15-30 minutes
Other reading:
- https://tb-manual.torproject.org/installation/
- https://tor.stackexchange.com/
- https://www.eff.org/pages/tor-and-https
- https://www.youtube.com/@TheTorProject/playlists?view=1&sort=dd&shelf_id=0
What is Tor?
Tor is a volunteer-run service that provides both privacy and anonymity online by masking who you are and from where you are connecting. The service also protects you from the Tor network itself—so you can have good assurance that you’ll remain anonymous to other Tor users.
For people who might need occasional anonymity and privacy when accessing websites, the Tor Browser provides a quick and easy way to use the Tor network.
The Tor Browser works just like a regular web browser . Web browsers are programs you use to view web sites. Examples include Chrome, Firefox, and Safari. Unlike other web browsers, though, the Tor Browser sends your communications through Tor, making it harder for people who are monitoring you to know exactly what you're doing online, and harder for people monitoring the sites you use to know where you're connecting from.
Keep in mind that only activities you do inside of Tor Browser itself will be anonymized. Having Tor Browser installed on your computer does not make anonymous things you do on the same computer using other software (such as your regular web browser). But there are steps you can take to protect that data too, if needed.
Some Tips to Keep in Mind When Using Tor
Tor is a useful tool for privacy and anonymity, but remember that it's generally impossible to achieve perfect anonymity. Knowing the limitations of Tor, and following some best practices, can help you stay safe online without too many surprises:
- Browsing the web is much slower over Tor, and certain websites may not work at all.
- The Tor Browser funnels only the browsing you do in the browser through the Tor network. Other apps or services installed on your device will not be routed through Tor.
- If you log into a website using the Tor Browser or fill out forms with personally identifying information, that website will be able to identify you and may know that you're using Tor.
- You can use Tor to circumvent censorship in a number of countries, but keep in mind that anyone who can see your network activity can also see that you're using Tor.
- Don't install or add any additional browser plugins to the Tor Browser that could de-anonymize you. Tor is already set up with a set of privacy protecting rules, so you do not need additional ad or tracker blockers.
- Beware of opening documents downloaded with Tor, especially when you have Tor running. Some documents may include internet-connected resources that may be downloaded when you open the document outside of Tor, which could reveal your IP address .
- The Tor Browser can access both the regular web that you're used to, as well as special ".onion" sites that only live on the Tor network. Unlike traditional websites, which have a public IP address, a .onion address is hidden, unique, and provides end-to-end encryption . You can check a number of EFF sites this way, including Surveillance Self-Defense itself (this link will only work in the Tor Browser).
The Tor Project maintains a page with other tips for anonymity that is worth checking periodically for other best practices for using Tor safely.
Getting Tor Browser
Open a browser like Firefox or Chrome and go to:
https://www.torproject.org/download/
If you are using a search engine to look for the Tor Browser, make sure that the URL is correct.
Only download Tor from the official website, and if you are prompted to accept alternative HTTPS (SSL/TLS) security certificates, do not proceed.
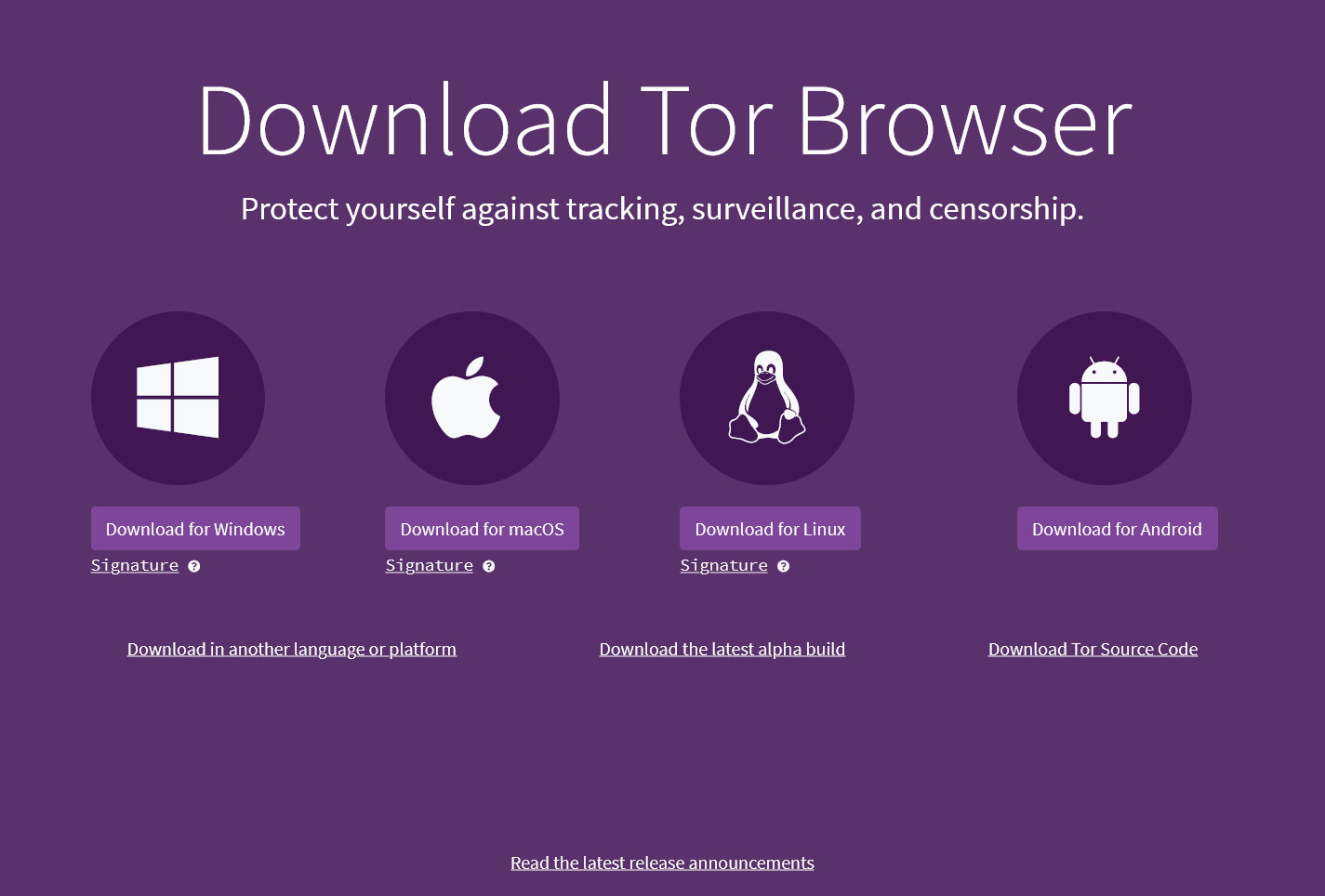
Select the "Download for Linux" icon:

Some browsers will ask you to confirm whether you want to download this file, otherwise it should automatically download the application.
This example shows Tor Browser version 12.5, which is the current version at the time of writing this guide. There may be a more recent version of Tor Browser available for download by the time you read this, so please download and use the current version that Tor Project provides.
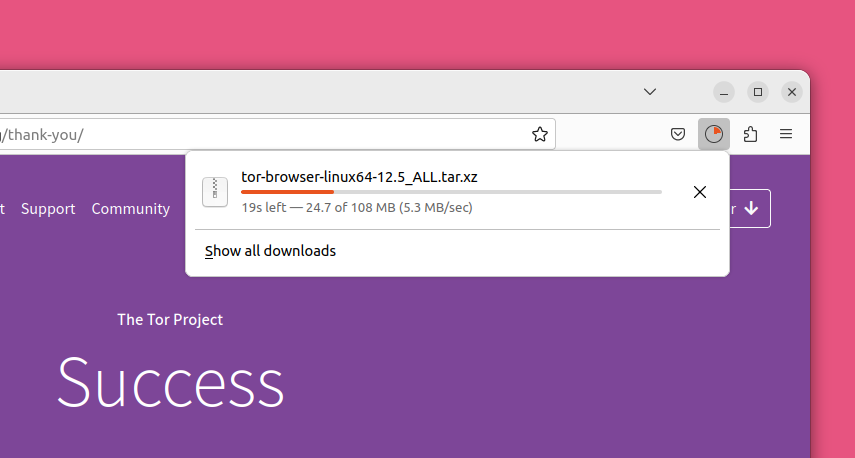
Installing Tor Browser
After the download is complete, go to your "Downloads" folder. You should always make sure you trust the software you want to install and that you got an authentic copy from the official site over a secure connection. Since you know this software is legitimate and the download was from the Tor Project's secure HTTPS site, double-click on the file “tor-browser-linux64-12.5_ALL.tar.xz”.
After double-clicking on the Tor Browser archive file, wait for it to load and then choose where you want to extract its contents.
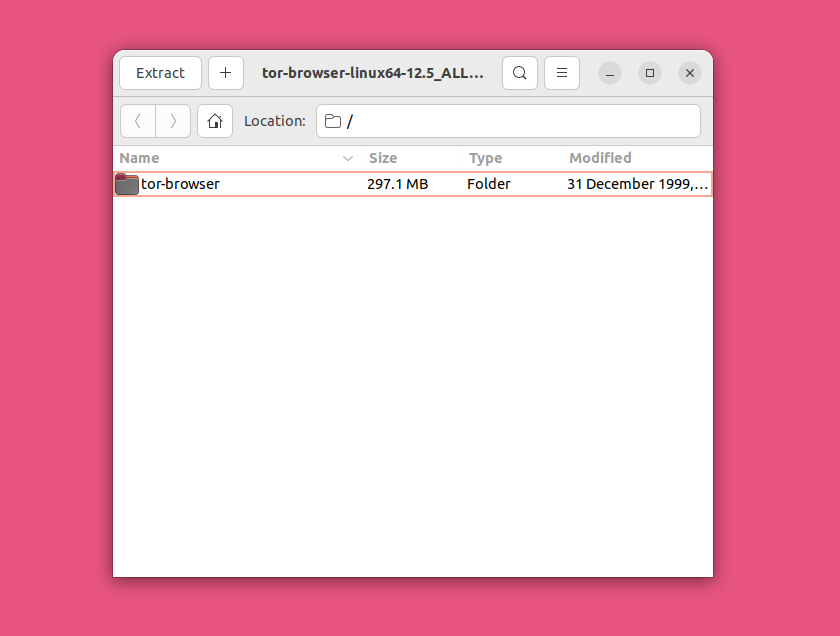
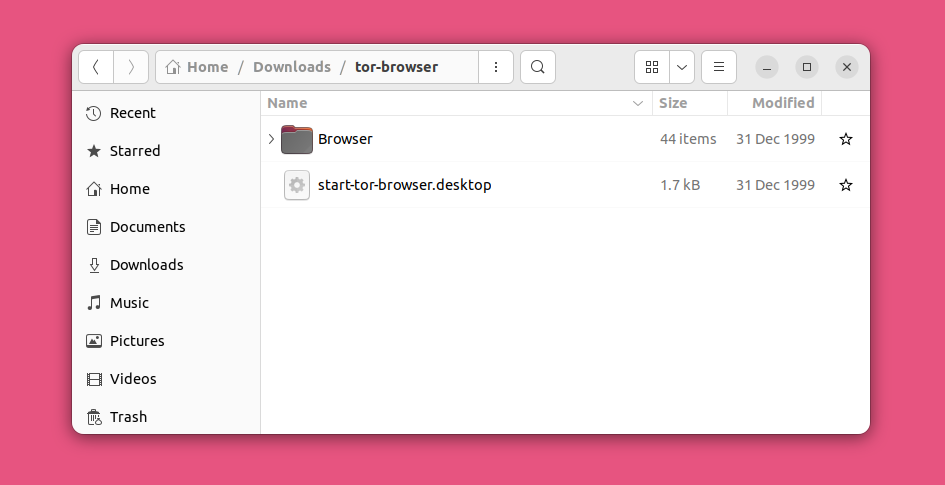
After the extraction is complete, open the “tor-browser” folder. Then, right-click on the file “start-tor-browser.desktop” and go to “Properties.”
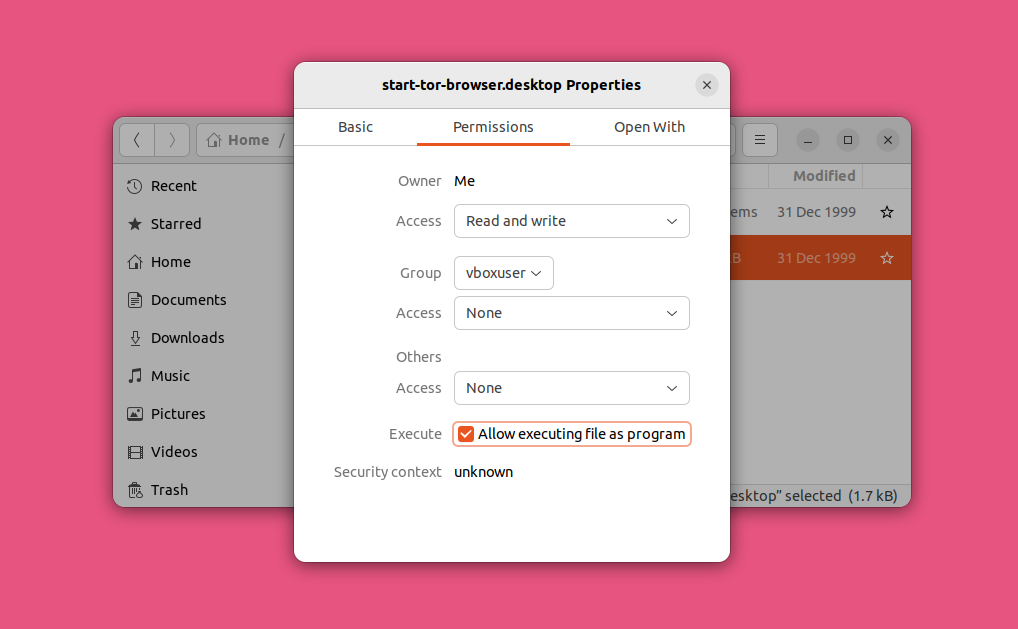
You will see another dialogue window pop up. Go to the “Permissions” tab and view the “Execute” property. Check the box next to this property.
Go back to the file and double-click it. Proceed to run the program if asked what to do.
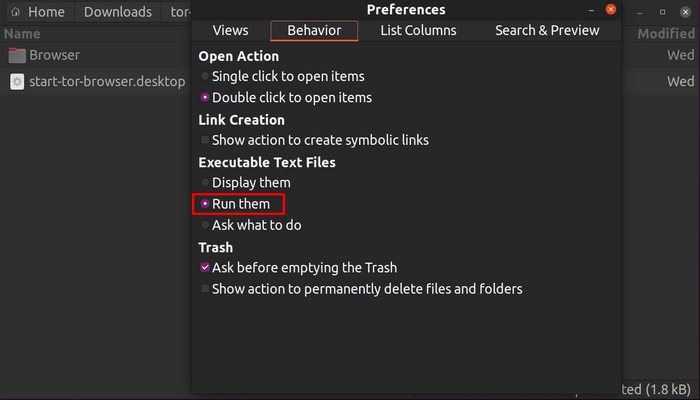
If the file does not run, you may have to take additional steps to set this type of file to run:
- Launch "Files."
- Click on “Preferences” in the menu at the top right.
- Navigate to the "Behavior" tab.
- Select "Run them" or "Ask what to do" under "Executable Text Files."
- If you choose the latter, click on "Run" after launching the start-tor-browser.desktop file.
If you are terminal savvy, you can also run the program from the command line by typing ./start-tor-browser.desktop and hitting enter.
Using Tor Browser
The first time Tor Browser starts, you'll get a window that allows you to modify some settings. You might have to come back and change some configuration settings later, but for now go ahead and try to connect to the Tor network by clicking the “Connect” button.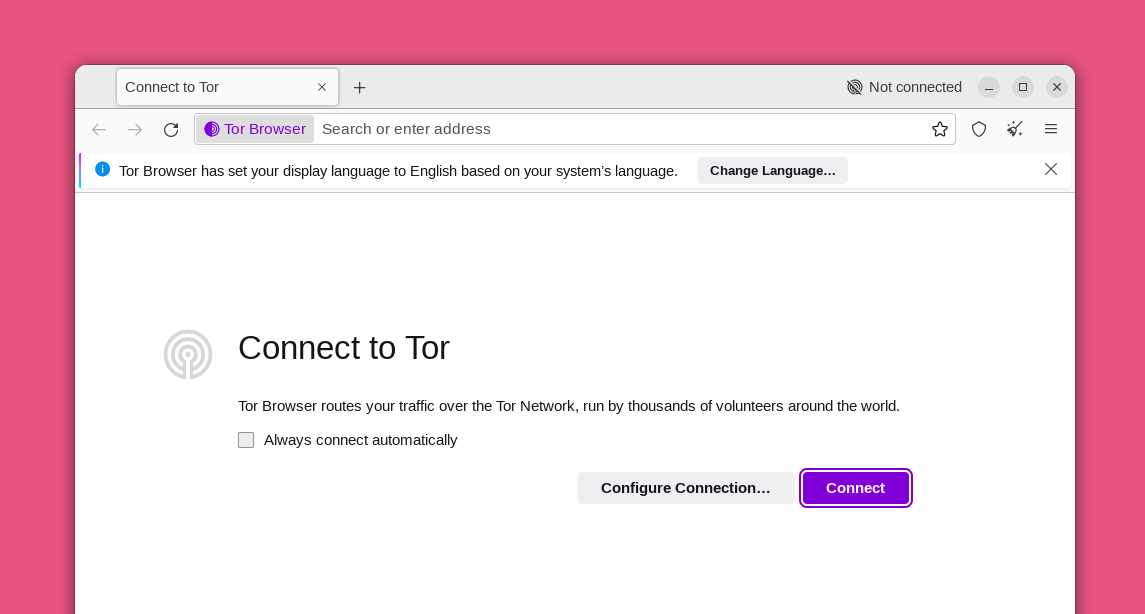
If Tor is blocked for you, the Connection Assist feature helps you choose a “bridge” using your location.
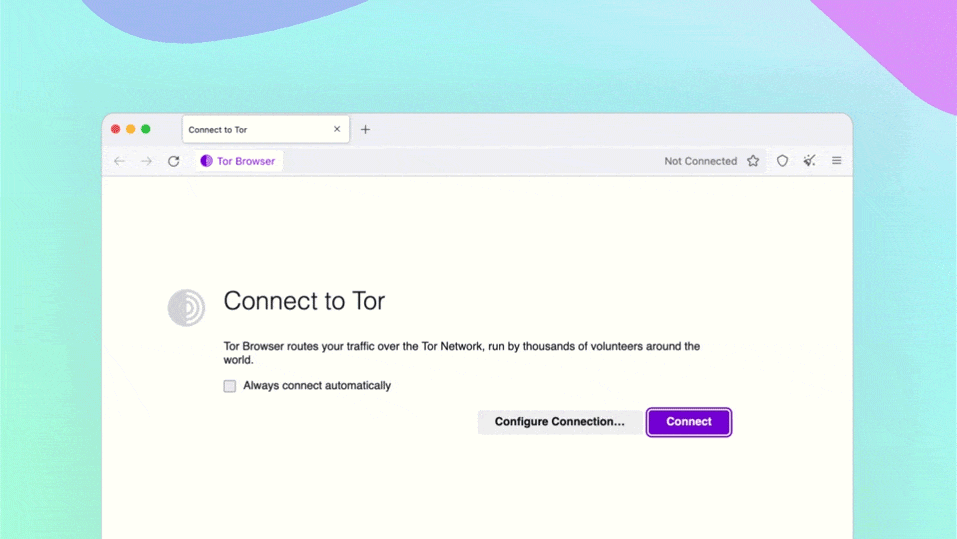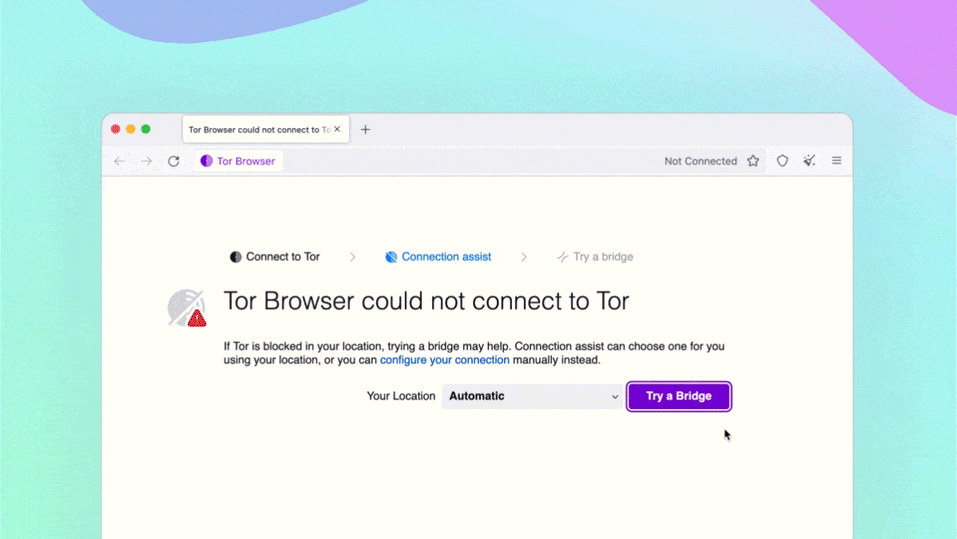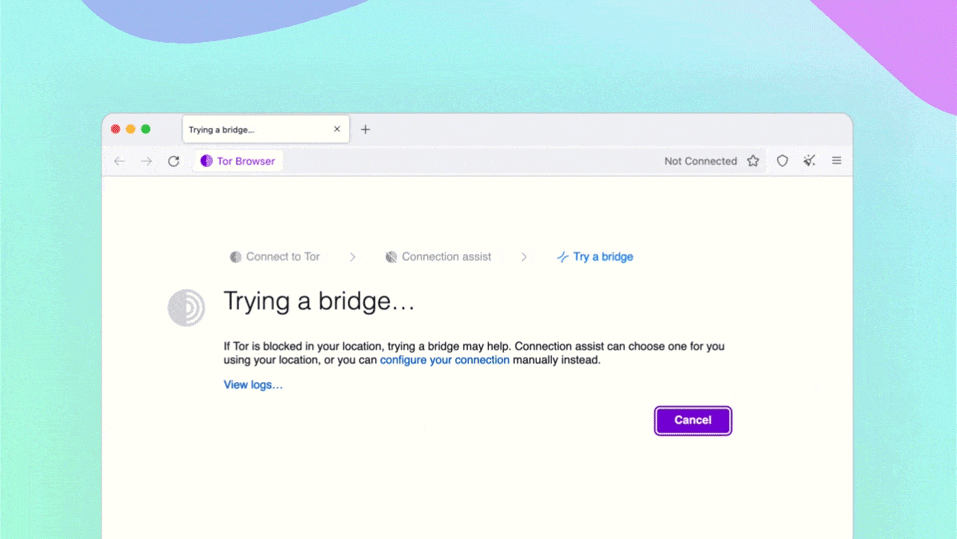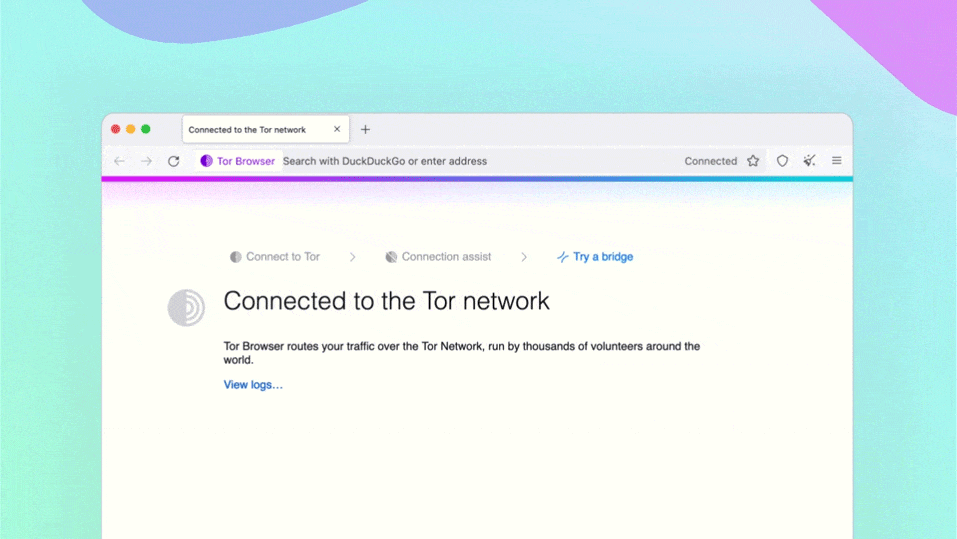 The first time Tor Browser starts, it might take a long time. Be patient, within a minute or two Tor Browser will connect.
The first time Tor Browser starts, it might take a long time. Be patient, within a minute or two Tor Browser will connect.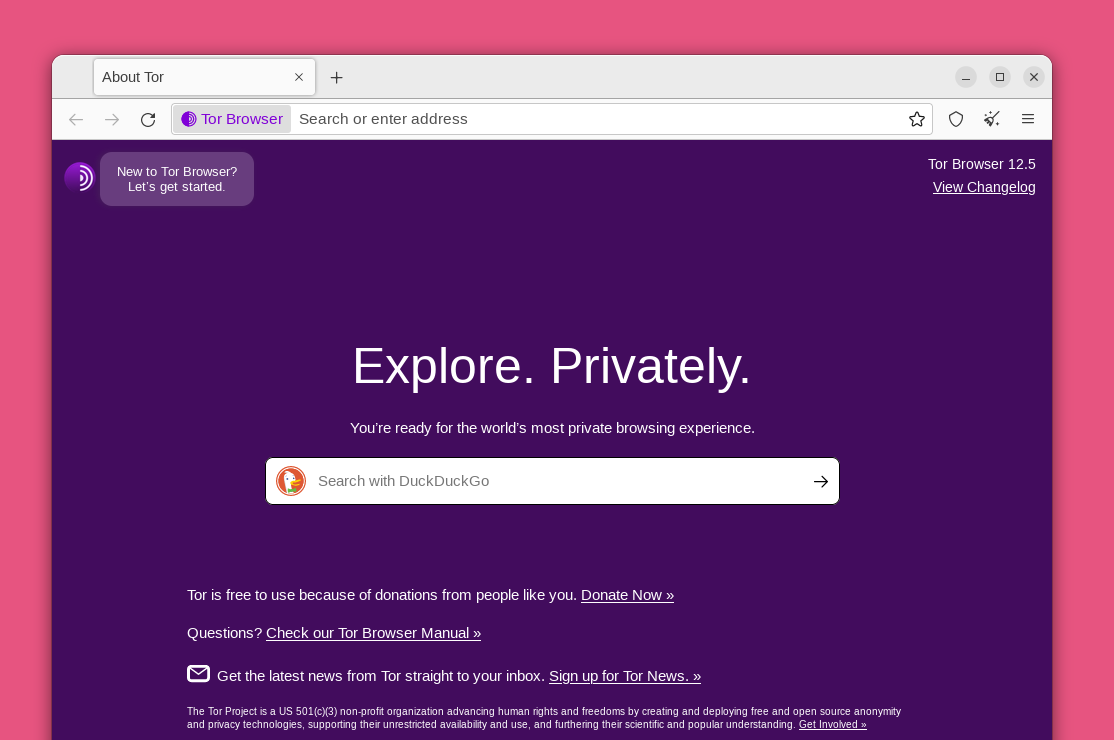 You will be greeted by the welcome screen. Click on the purple onion icon in the upper left corner to review a tutorial on how Tor works.
You will be greeted by the welcome screen. Click on the purple onion icon in the upper left corner to review a tutorial on how Tor works.
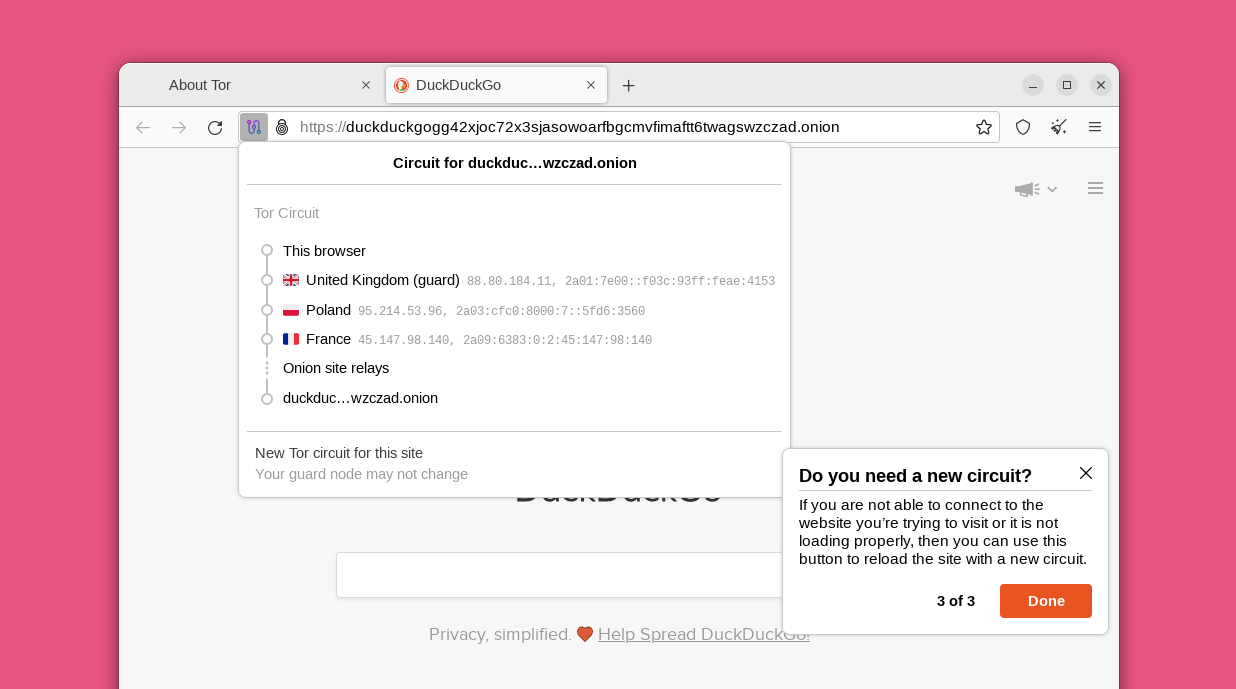
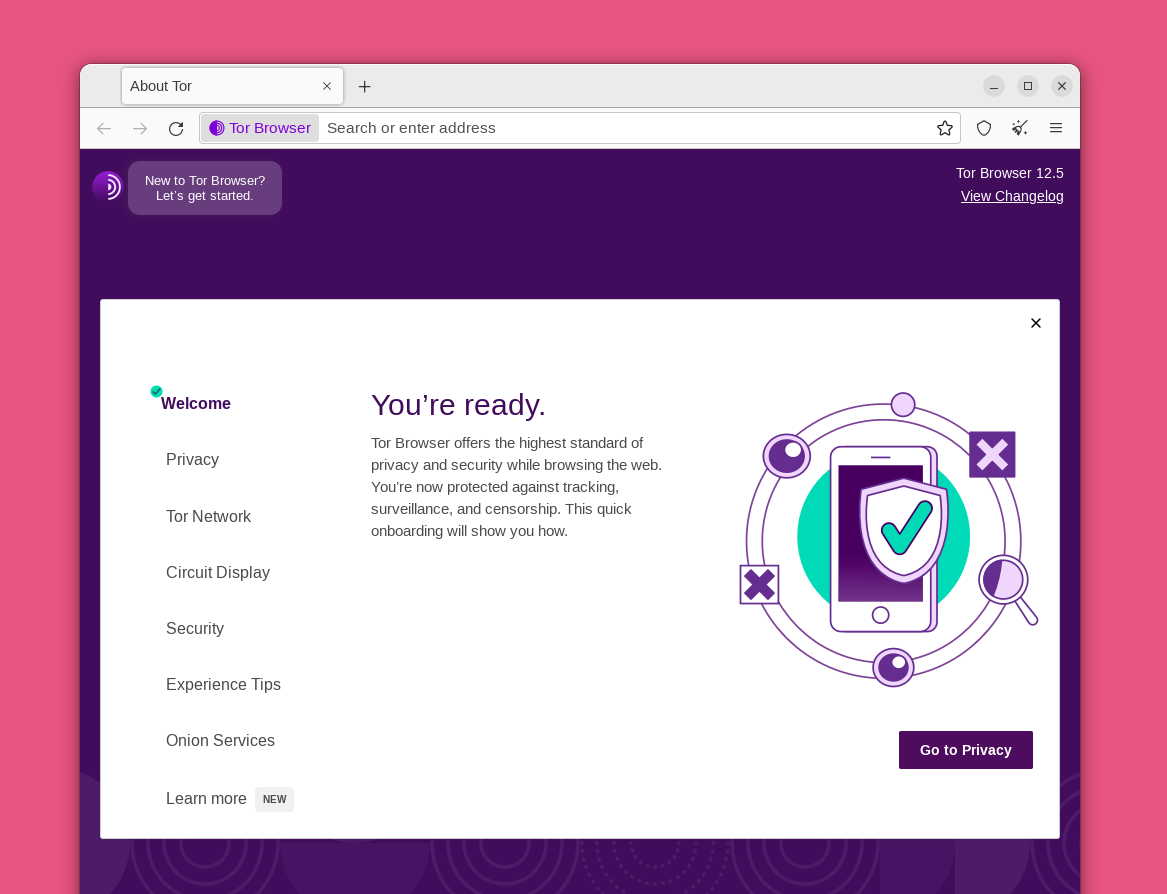 The tutorial includes an explanation of how Tor circuits work and how they allow you to browse privately online.
The tutorial includes an explanation of how Tor circuits work and how they allow you to browse privately online.

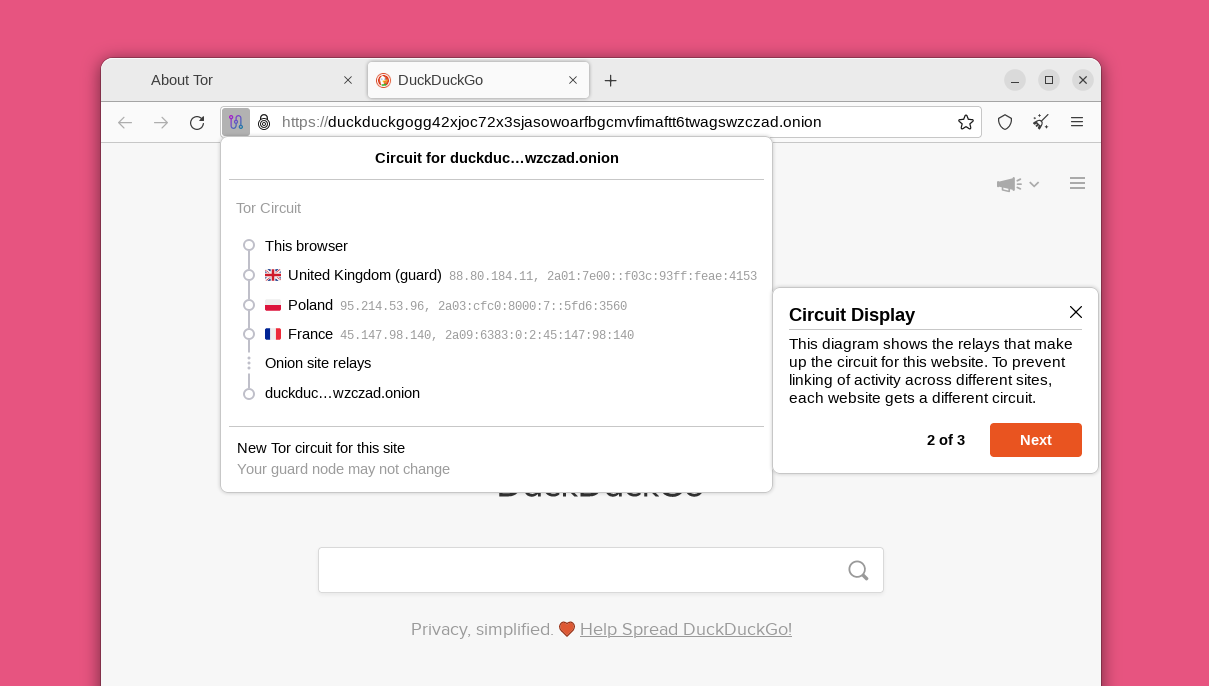
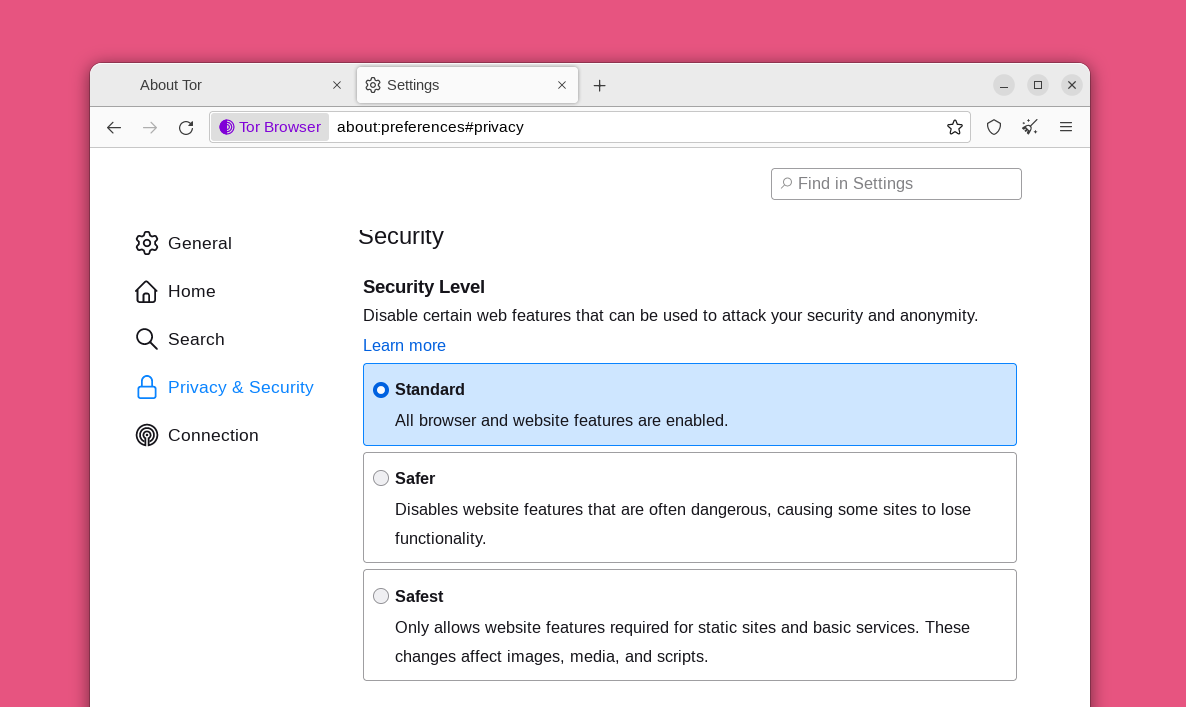
The Tor Browser's default security level will block many known privacy and security issues found in other web browsers. For example, it uses an HTTPS-only mode and NoScript by default. You can also crank up the security further if needed.
Click the shield icon in the top right corner, then click "Settings," and you're taken to the "Privacy & Security" settings. Changing Tor's "Security Level" to its "Safest" setting disables a variety of website features that can potentially be used against you. This will make you safer from well-funded attackers who can interfere with your internet connection or use new unknown bugs in these features. Unfortunately, the "Safest" setting can make some websites unusable. The default "Standard" setting is fine for everyday privacy protection, but you can set it to "Safest" if you are worried about sophisticated attackers, or if you don't mind if some websites do not display correctly. You can get more information about each security level here.
Finally, browsing with Tor is different in some ways from the normal browsing experience. We recommend reading these tips for properly browsing with the Tor Browser and retaining your anonymity.
You are now ready to browse the Internet anonymously with the Tor Browser.

